Address compromised user accounts with automated investigation and response
Tip
Did you know you can try the features in Microsoft Defender XDR for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
Microsoft Defender for Office 365 Plan 2 includes powerful automated investigation and response (AIR) capabilities. Such capabilities can save your security operations team a lot of time and effort dealing with threats. This article describes one of the facets of the AIR capabilities, the compromised user security playbook.
The compromised user security playbook enables your organization's security team to:
- Speed up detection of compromised user accounts;
- Limit the scope of a breach when an account is compromised; and
- Respond to compromised users more effectively and efficiently.
Compromised user alerts
When a user account is compromised, atypical or anomalous behaviors occur. For example, phishing and spam messages might be sent internally from a trusted user account. Defender for Office 365 can detect such anomalies in email patterns and collaboration activity within Office 365. When this happens, alerts are triggered, and the threat mitigation process begins.
Investigate and respond to a compromised user
When a user account is compromised, alerts are triggered. And in some cases, that user account is blocked and prevented from sending any further email messages until the issue is resolved by your organization's security operations team. In other cases, an automated investigation begins which can result in recommended actions that your security team should take.
Important
You must have appropriate permissions to perform the following tasks. See Required permissions to use AIR capabilities.
Watch this short video to learn how you can detect and respond to user compromise in Microsoft Defender for Office 365 using Automated Investigation and Response (AIR) and compromised user alerts.
View and investigate restricted users
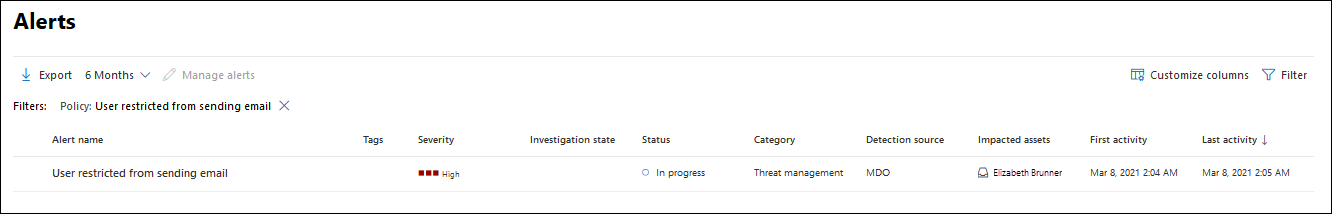
You have a few options for navigating to a list of restricted users. For example, in the Microsoft Defender portal, you can go to Email & collaboration > Review > Restricted Users. The following procedure describes navigation using the Alerts dashboard, which is a good way to see various kinds of alerts that might have been triggered.
Open the Microsoft Defender portal at https://security.microsoft.com and go to Incidents & alerts > Alerts. Or, to go directly to the Alerts page, use https://security.microsoft.com/alerts.
On the Alerts page, filter the results by time period and the policy named User restricted from sending email.
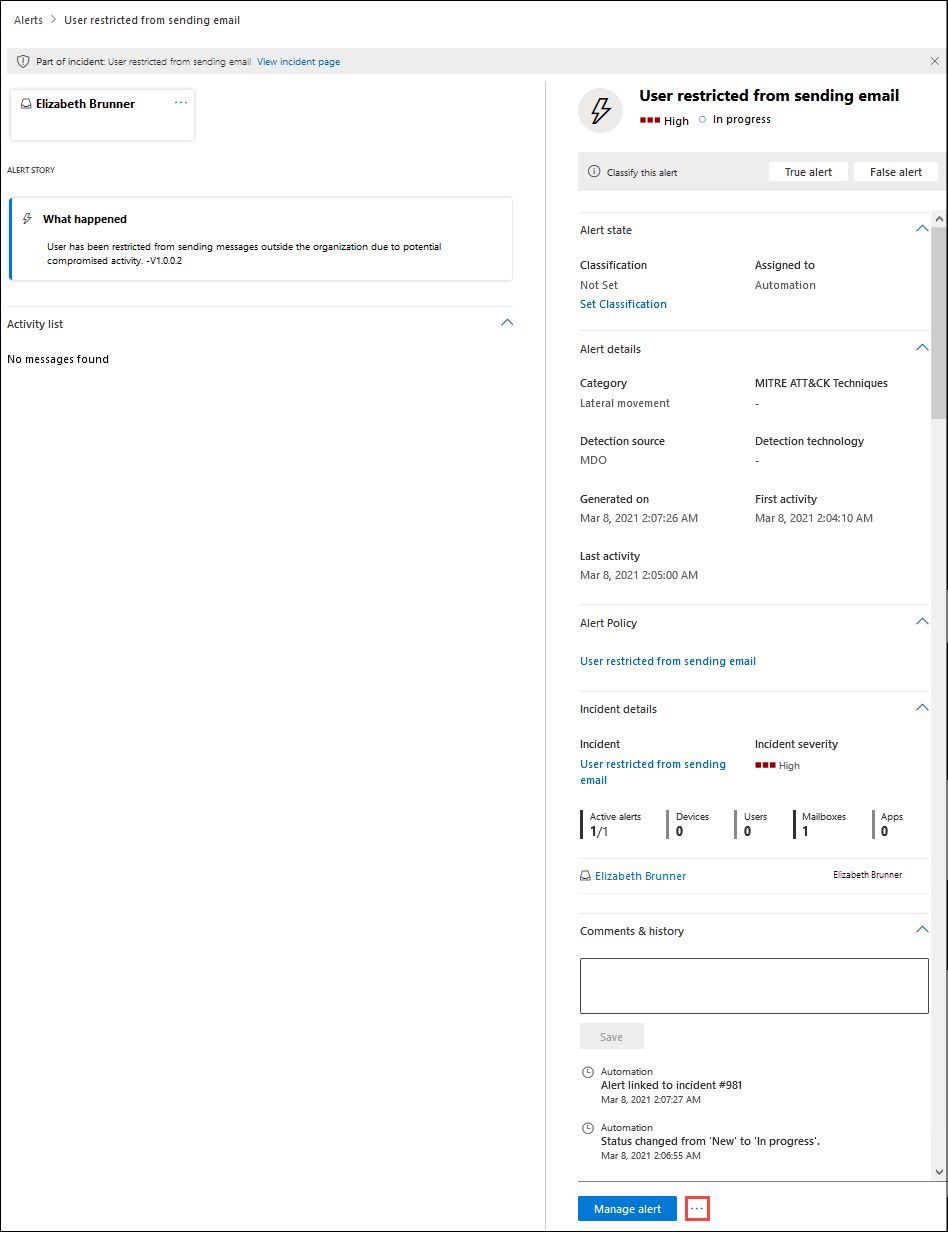
If you select the entry by clicking on the name, a User restricted from sending email page opens with additional details for you to review. Next to the Manage alert button, you can click
 More options and then select View restricted user details to go to the Restricted users page, where you can release the restricted user.
More options and then select View restricted user details to go to the Restricted users page, where you can release the restricted user.
View details about automated investigations
When an automated investigation has begun, you can see its details and results in the Action center in the Microsoft Defender portal.
To learn more, see View details of an investigation.
Keep the following points in mind
Stay on top of your alerts. As you know, the longer a compromise goes undetected, the larger the potential for widespread impact and cost to your organization, customers, and partners. Early detection and timely response are critical to mitigate threats, and especially when a user's account is compromised.
Automation assists your security operations team. Automated investigation and response capabilities can detect a compromised user early on and enable your security operations team to take action to remediate the threat. Need some help with this? See Review and approve actions.