Conditional Access policy templates
Conditional Access templates provide a convenient method to deploy new policies aligned with Microsoft recommendations. These templates are designed to provide maximum protection aligned with commonly used policies across various customer types and locations.
Template categories
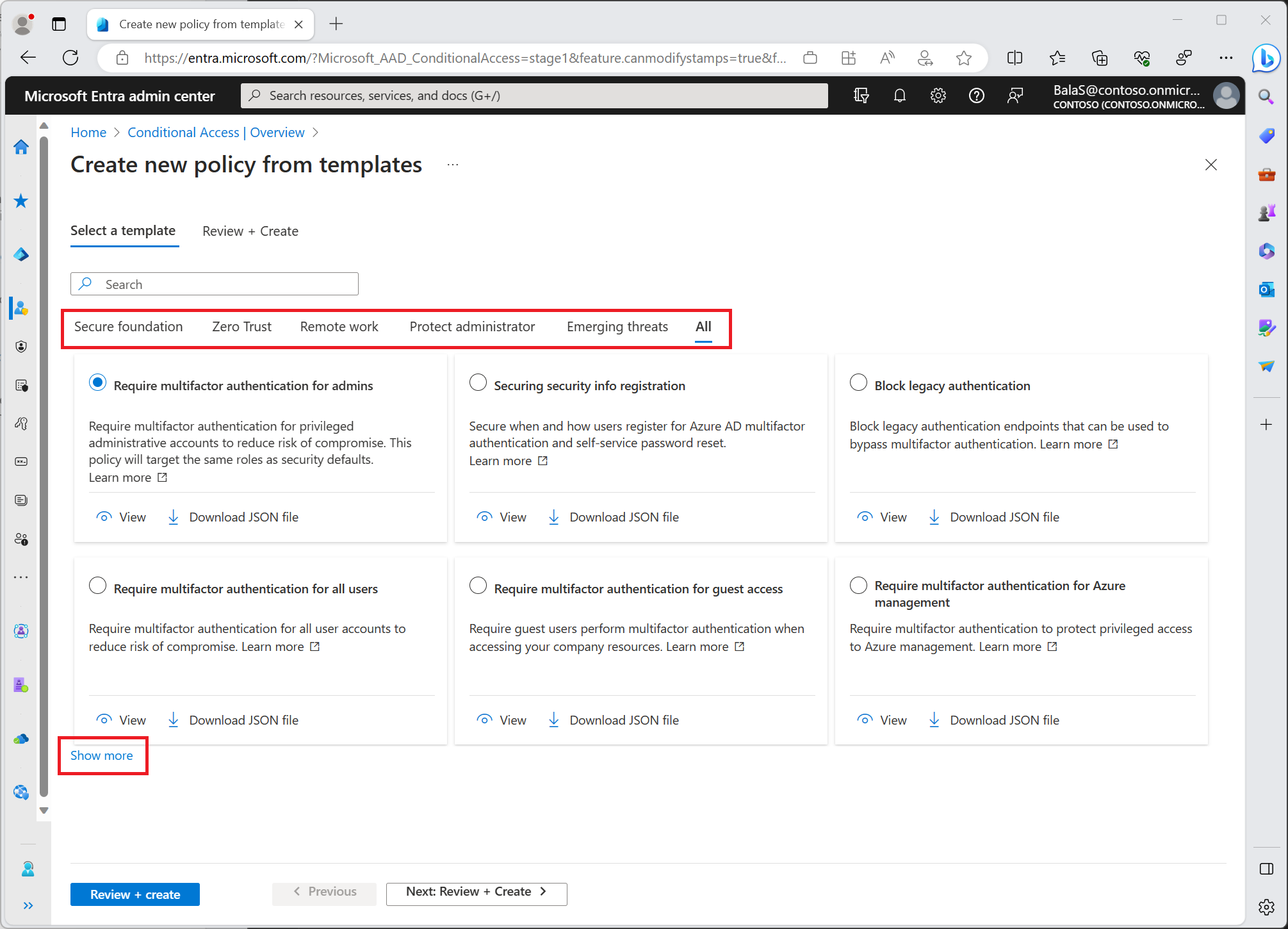
Conditional Access policy templates are organized into the following categories:
Microsoft recommends these policies as the base for all organizations. We recommend these policies be deployed as a group.
- Require multifactor authentication for admins
- Securing security info registration
- Block legacy authentication
- Require multifactor authentication for admins accessing Microsoft admin portals
- Require multifactor authentication for all users
- Require multifactor authentication for Azure management
- Require compliant or Microsoft Entra hybrid joined device or multifactor authentication for all users
- Require compliant device
Find these templates in the Microsoft Entra admin center > Protection > Conditional Access > Create new policy from templates. Select Show more to see all policy templates in each category.
Important
Conditional Access template policies will exclude only the user creating the policy from the template. If your organization needs to exclude other accounts, you will be able to modify the policy once they are created. You can find these policies in the Microsoft Entra admin center > Protection > Conditional Access > Policies. Select a policy to open the editor and modify the excluded users and groups to select accounts you want to exclude.
By default, each policy is created in report-only mode, we recommended organizations test and monitor usage, to ensure intended result, before turning on each policy.
Organizations can select individual policy templates and:
- View a summary of the policy settings.
- Edit, to customize based on organizational needs.
- Export the JSON definition for use in programmatic workflows.
- These JSON definitions can be edited and then imported on the main Conditional Access policies page using the Upload policy file option.
Other common policies
- Require multifactor authentication for device registration
- Block access by location
- Block access except specific apps
User exclusions
Conditional Access policies are powerful tools, we recommend excluding the following accounts from your policies:
- Emergency access or break-glass accounts to prevent lockout due to policy misconfiguration. In the unlikely scenario all administrators are locked out, your emergency-access administrative account can be used to log in and take steps to recover access.
- More information can be found in the article, Manage emergency access accounts in Microsoft Entra ID.
- Service accounts and Service principals, such as the Microsoft Entra Connect Sync Account. Service accounts are non-interactive accounts that aren't tied to any particular user. They're normally used by back-end services allowing programmatic access to applications, but are also used to sign in to systems for administrative purposes. Calls made by service principals won't be blocked by Conditional Access policies scoped to users. Use Conditional Access for workload identities to define policies targeting service principals.
- If your organization has these accounts in use in scripts or code, consider replacing them with managed identities.