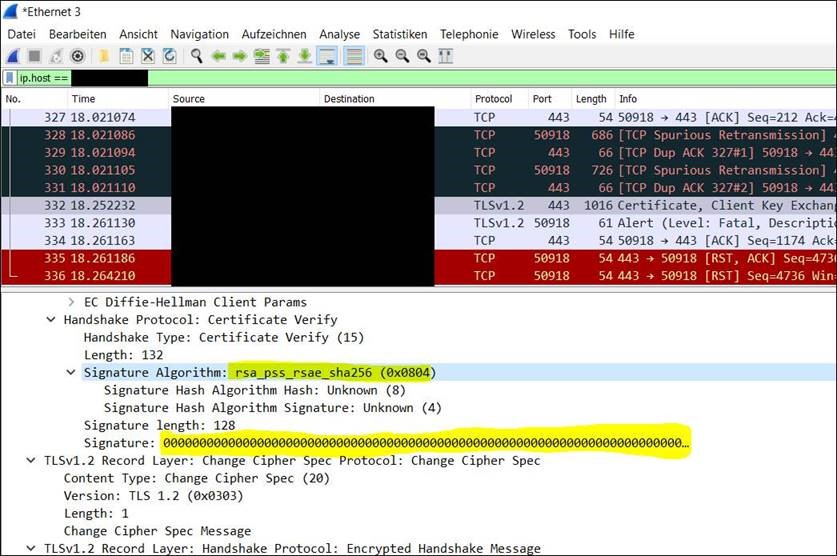
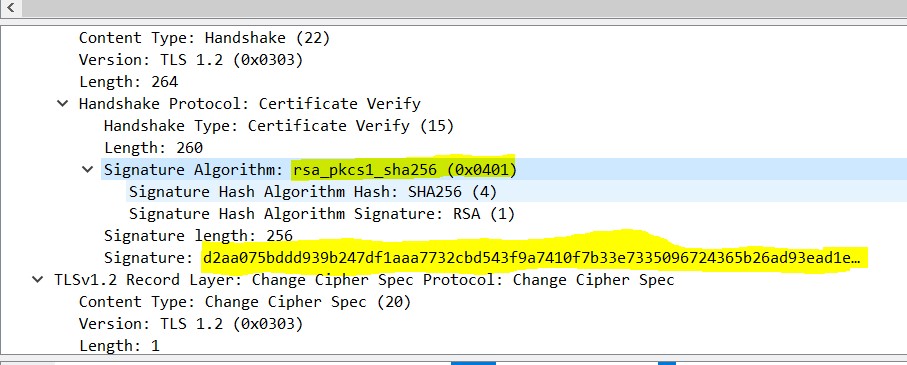
This problem gave me the following error when saving the Bitlocker recovery key in AzureAD:
Failed to backup BitLocker Drive Encryption recovery information for volume C: to your Azure AD.
TraceId: {....}
Error: Unknown HResult Error code: 0x80072f8f
Problem occured on Windows 11 version 10.0.22621
Removing the 3 registry values helped.
Output from tpmtool getdeviceinformation
-TPM Present: True
-TPM version: 2.0
-TPM Vendor ID: IFX
- Full name of TPM manufacturer: Infineon
-TPM Manufacturer Version: 7.63.3353.0
-PPI version: 1.3
-Is initialized: True
-Ready to save: True
-Ready for Evidence: True
-Is verifiable: True
-Must be deleted to restore: False
-Can be deleted: True
Incorrect
-Bitlocker PCR7 Binding Status: Bound
-Maintenance task completed: True
-TPM specification version: 1.16
-TPM Errata Date: Wednesday, September 21, 2016
-PC client version: 1.00
-Lockout information:
-Is blocked: False
-Lockout counter: 0
-Max. Authentication error: 31
-Lockout interval: 600s
-Lockout recovery: 86400s