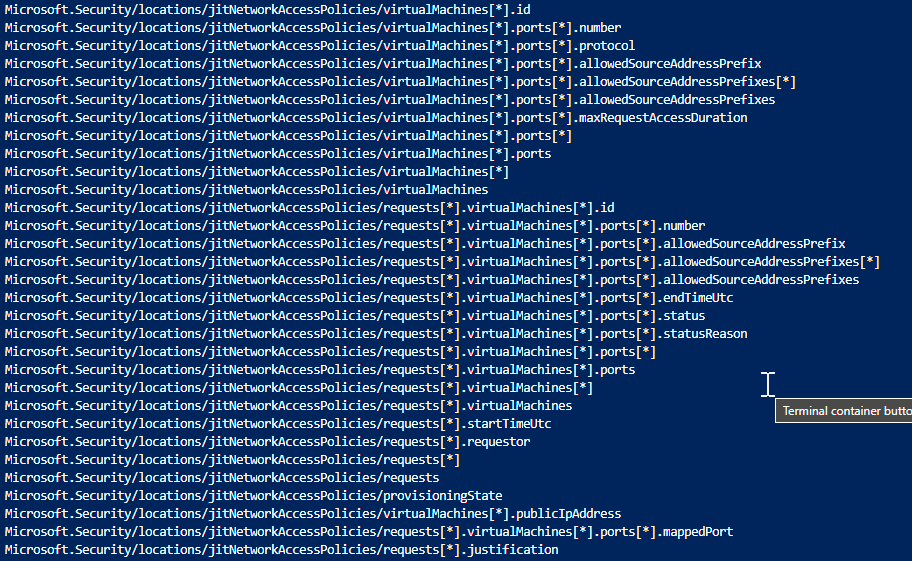
Hello gents,
I'm having some issues with JIT for Azure VMs.
We want to use JIT to allow externals (Third-parties or contractors) to access specifics VMs remotely. As we have an huge list of externals (big enterprise, long list of applications from different providers), we can't provide a specific list of IPs into JIT configuration as we don't know the public IPs of all external companies. Due to that, we left the default rule "Per request" in JIT on the VM.
Next to that, I deployed an Azure Policy to restrict NSG rule so users cannot create a rule opening RDP or SSH from any, internet or 0.0.0.0/0. I tested the Policy by creating a rule in NSG manually, I get denied so that works.
During testing, I found out two issues:
- I see that by default, the portal select "All configured IPs" in the "Connect" blade of Azure VM and I didn't find in JIT a way to remove that option to only have "My IP" or "Other IP/IPs". That option doesn't exist when going through "Security" blade but users won't go that way when the "Connect" blade takes 2 clicks instead of 5 in different panels through "Security". Is there a way to remove that option?
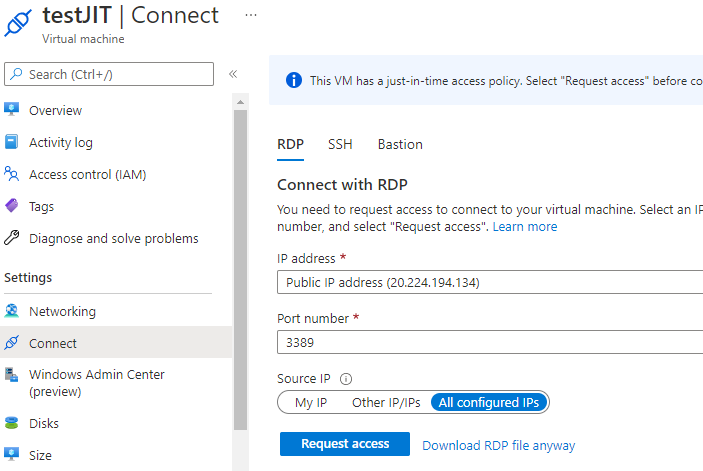
- JIT ignores Azure Policy. Thanks to my Azure Policy, I cannot create manually a NSG rule to open RDP from any, but JIT doesn't throw an error and the "SecurityCenter-JITRule-" opening RDP from Any is created successfully. Can we make JIT under control by Azure Policy?
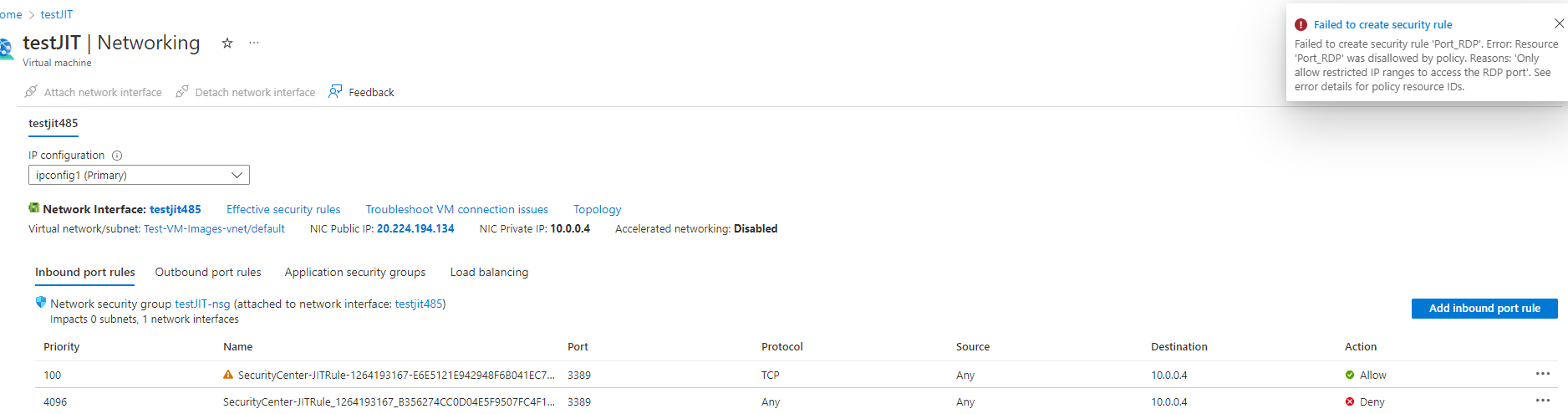
Notes to counter questions:
Yes, I tested to create a Rule in NSG manually using exactly the same configuration as JIT: my Azure Policy triggered and denied me.
We have scenarios where the Azure Vnet hosting the VM is not connected to our network, so VPN or access from company network is not possible either.
I know Bastion but it has a cost so we are looking at other options before validating the best option.
Thank you in advance,
Teddy