Investigate connection events that occur behind forward proxies
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
Want to experience Defender for Endpoint? Sign up for a free trial.
Defender for Endpoint supports network connection monitoring from different levels of the network stack. A challenging case is when the network uses a forward proxy as a gateway to the Internet.
The proxy acts as if it was the target endpoint. In these cases, simple network connection monitors audit the connections with the proxy that is correct but has lower investigation value.
Defender for Endpoint supports advanced HTTP level monitoring through network protection. When turned on, a new type of event is surfaced which exposes the real target domain names.
Use network protection to monitor network connection behind a firewall
Monitoring network connection behind a forward proxy is possible due to other network events that originate from network protection. To see them on a device timeline, turn on network protection (at the minimum in audit mode).
Network protection can be controlled using the following modes:
- Block: Users or apps are blocked from connecting to dangerous domains. You'll be able to see this activity in Microsoft Defender XDR.
- Audit: Users or apps won't be blocked from connecting to dangerous domains. However, you'll still see this activity in Microsoft Defender XDR.
If you turn off network protection, users or apps won't be blocked from connecting to dangerous domains. You won't see any network activity in Microsoft Defender XDR.
If you don't configure it, network blocking is turned off by default.
For more information, see Enable network protection.
Investigation impact
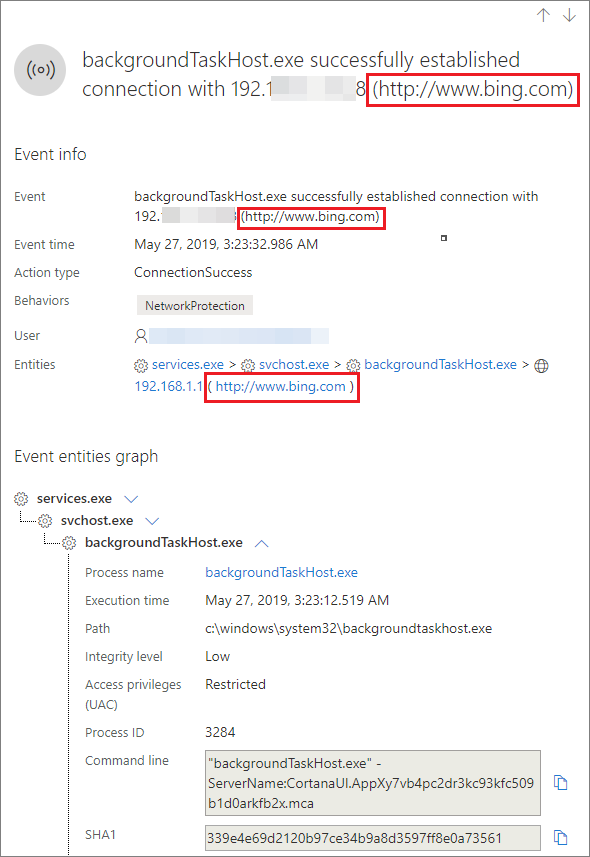
When network protection is turned on, you'll see that on a device's timeline the IP address keeps representing the proxy, while the real target address shows up.
Other events triggered by the network protection layer are now available to surface the real domain names even behind a proxy.
Event's information:
Hunt for connection events using advanced hunting
All new connection events are available for you to hunt on through advanced hunting as well. Since these events are connection events, you can find them under the DeviceNetworkEvents table under the ConnecionSuccess action type.
Using this simple query shows you all the relevant events:
DeviceNetworkEvents
| where ActionType == "ConnectionSuccess"
| take 10
You can also filter out events that are related to connection to the proxy itself.
Use the following query to filter out the connections to the proxy:
DeviceNetworkEvents
| where ActionType == "ConnectionSuccess" and RemoteIP != "ProxyIP"
| take 10
Related articles
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.