Migrate a manually registered Azure VPN Client to the Microsoft-registered client
This article helps you migrate from a manually registered Azure VPN Client to the Microsoft-registered Azure VPN Client for point-to-site (P2S) Microsoft Entra ID authentication. The Microsoft-registered Azure VPN client uses a different Audience value. When you update an Audience value, you must make the change on both the P2S VPN gateway, and on any previously configured VPN clients. For more information about Audience values, see About point-to-site VPN - Microsoft Entra ID authentication.
The following table shows the available supported Audience values.
| App ID | Supported Audience values | Supported clients |
|---|---|---|
| Microsoft-registered | - Azure Public: c632b3df-fb67-4d84-bdcf-b95ad541b5c8 |
- Linux - Windows - macOS |
| Manually registered | - Azure Public: 41b23e61-6c1e-4545-b367-cd054e0ed4b4- Azure Government: 51bb15d4-3a4f-4ebf-9dca-40096fe32426- Azure Germany: 538ee9e6-310a-468d-afef-ea97365856a9- Microsoft Azure operated by 21Vianet: 49f817b6-84ae-4cc0-928c-73f27289b3aa |
- Windows - macOS |
| Custom | <custom-app-id> |
- Linux - Windows - macOS |
The examples in this article use the new Audience value for Azure Public. This article doesn't apply to custom Audience value configurations. To modify a custom audience app ID, see Create or modify a custom audience app ID for P2S VPN Microsoft Entra ID authentication.
Workflow
The standard workflow is:
- Update P2S gateway settings.
- Generate and download new VPN client configuration files.
- Update the VPN client either by importing the client configuration package, or (optionally) updating the settings on the already configured VPN client.
- Remove the old Azure VPN Client from the tenant. This step isn't required in order to make a P2S connection using the new Audience value, but it's good practice.
Update P2S gateway settings
When you update audience values on an existing gateway, you incur fewer than 5 minutes of downtime.
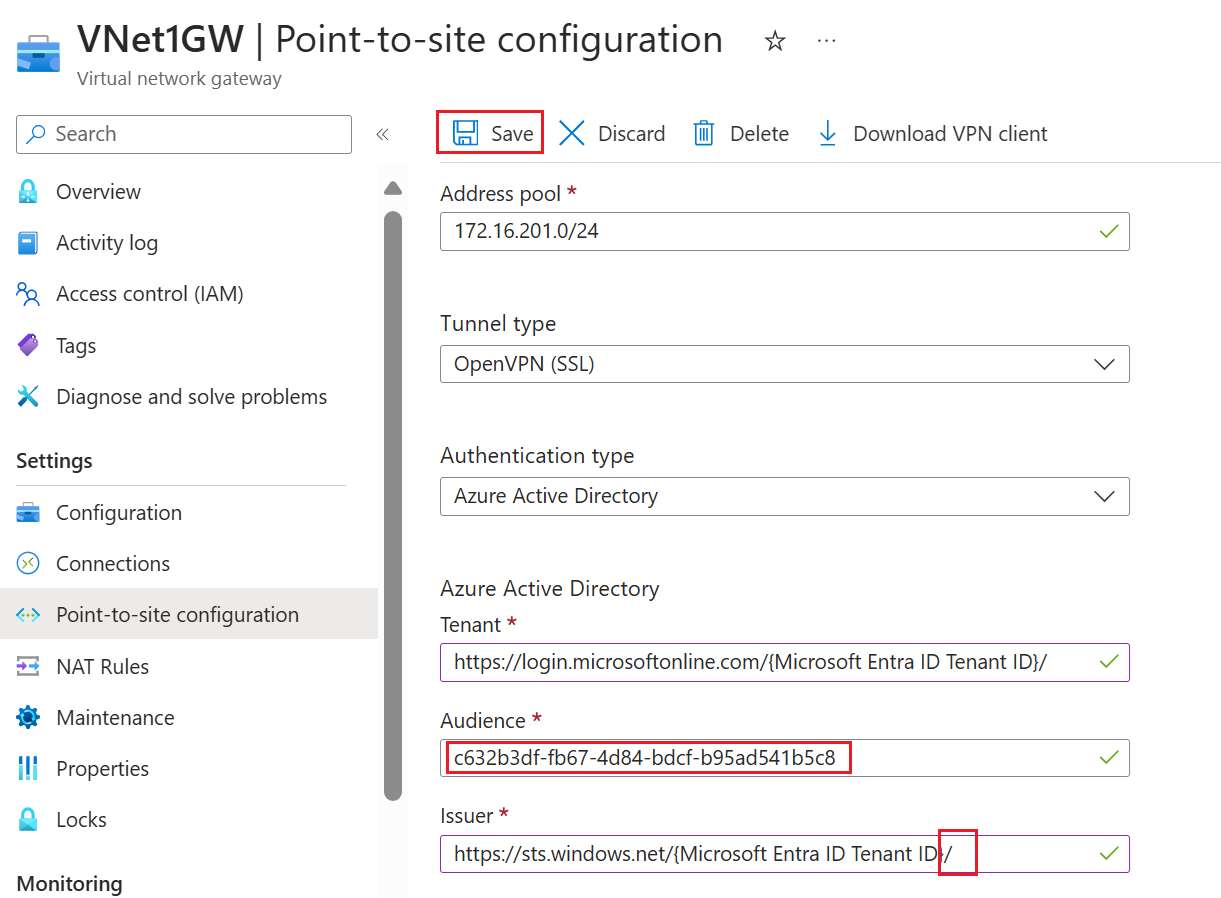
Go to the virtual network gateway. In the left pane, click Point-to-site configuration, then Configure now to open the Point-to-site configuration page.
Change the Audience value. For this example, we changed the Audience value to the Azure Public value for the Microsoft-registered Azure VPN Client; c632b3df-fb67-4d84-bdcf-b95ad541b5c8.
Leave the other settings the same, unless you have changed tenants and need to change the tenant IDs. If you update the Issuer field, take care to include the trailing slash at the end. For more information about each of the fields, see Microsoft Entra ID values.
Once you finish configuring settings, click Save at the top of the page.
The new settings save to the P2S gateway and the gateway updates. This takes about 5 minutes to complete.
Update VPN client settings
When you make a change to a P2S gateway, you typically need to generate and download a new VPN client profile configuration package. This package contains the updated settings from the P2S VPN gateway. If you're configuring new Azure VPN Clients, you must generate this configuration package.
However, when you update only the Audience or tenant values, you have a couple of options when reconfiguring already deployed Azure VPN Clients.
If the Azure VPN Client is already configured to connect to this P2S gateway, you can manually update the VPN client.
If you've updated multiple values on the P2S gateway, or you want easily update the VPN clients by importing the new values, you can generate and download a new P2S VPN client profile configuration package and import it to each client.
Update an Azure VPN Client
These steps help you update the Azure VPN Client manually, without using the profile configuration package.
- Launch the Azure VPN Client app.
- Select the VPN connection profile that you want to update.
- Click ..., then Configure.
- Update the Audience field to the new Audience value. This value must match the P2S gateway value to which this client connects.
- If you also updated the Tenant ID values, change them on the client. These values must match the P2S gateway values.
- Click Save to save the settings.
Update using a profile configuration package
If you want to use the VPN client profile configuration files to configure your Azure VPN Client, you can generate a profile configuration package that contains the new P2S gateway settings.
At the top of the Point-to-site configuration page, click Download VPN client. It takes a few minutes for the client configuration package to generate.
Your browser indicates that a client configuration zip file is available. It's named the same name as your gateway.
Extract the downloaded zip file.
Browse to the unzipped "AzureVPN" folder.
Make a note of the location of the “azurevpnconfig.xml” file. The azurevpnconfig.xml contains the setting for the VPN connection. You can also distribute this file to all the users that need to connect via e-mail or other means. The user will need valid Microsoft Entra ID credentials to connect successfully.
Next steps
For more information about configuring the Azure VPN Client for Microsoft Entra ID authentication, see the following articles: