Hi,
Currently I am trying to create various policies.
One of those is to allow the creation of a storageAccount but disallow the creation of Queues. The policy is deployed through the use of a Bicep template:
resource policyBlockResourceTypes 'Microsoft.Authorization/policyDefinitions@2020-09-01' = {
name: policyConfigurations.policyBlockResourceTypes.name
properties: {
displayName: '[${policyConfigurations.policyBlockResourceTypes.name}] BlockResourceTypesqueues'
policyType: 'Custom'
mode: 'All'
description: 'Policy to whitelist resource types'
metadata: policyConfigurations.policyBlockResourceTypes.metadata
policyRule: {
if: {
anyOf: [
{
field: 'type'
like: 'Microsoft.Storage/storageAccounts/queueServices/queues'
}
]
}
then: {
effect: 'deny'
}
}
}
}
The policy has been applied at both the Subscription and Resource Group level but unfortunately I am still able to create queues.
The policy definition:
{
"properties": {
"displayName": "[pol-sandbox-res-003] BlockResourceTypesqueues",
"policyType": "Custom",
"mode": "All",
"description": "Policy to whitelist resource types",
"metadata": {
"version": "0.1.0",
"category": "category",
"source": "source",
"createdBy": "a1a2eac0-6a29-470b-8101-3106532c28fd",
"createdOn": "2023-03-31T07:27:30.5601202Z",
"updatedBy": "a1a2eac0-6a29-470b-8101-3106532c28fd",
"updatedOn": "2023-04-03T10:17:16.1670547Z"
},
"policyRule": {
"if": {
"anyOf": [
{
"field": "type",
"like": "Microsoft.Storage/storageAccounts/queueServices/queues"
}
]
},
"then": {
"effect": "deny"
}
}
},
"id": "/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/providers/Microsoft.Authorization/policyDefinitions/pol-sandbox-res-003",
"type": "Microsoft.Authorization/policyDefinitions",
"name": "pol-sandbox-res-003",
"systemData": {
"createdBy": "ferdi.stoeltie@lagersmit.com",
"createdByType": "User",
"createdAt": "2023-03-31T07:27:30.5132596Z",
"lastModifiedBy": "ferdi.stoeltie@lagersmit.com",
"lastModifiedByType": "User",
"lastModifiedAt": "2023-04-03T10:17:16.1376884Z"
}
}
While creating new StorageAccounts and new Queues the activity log of the policy assignment shows the following:
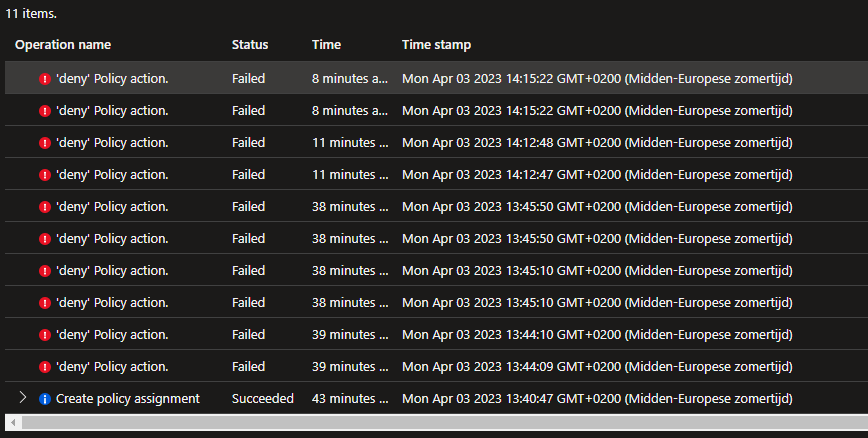
And the JSON that is attached to it:
{
"authorization": {
"action": "Microsoft.Storage/storageAccounts/queueServices/queues/write",
"scope": "/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/resourceGroups/Dev-Portal-01_group/providers/Microsoft.Storage/storageAccounts/testdeleter/queueServices/default/queues/failplease"
},
"caller": "ferdi.stoeltie@lagersmit.com",
"channels": "Operation",
"claims": {
"aud": "https://management.core.windows.net/",
"iss": "https://sts.windows.net/f91416ec-377f-48d6-bd99-f28817bce3dc/",
"iat": "1680523633",
"nbf": "1680523633",
"exp": "1680528537",
"http://schemas.microsoft.com/claims/authnclassreference": "1",
"aio": "AVQAq/8TAAAAKV/OnG0x/cI4SVvWK6c2etStWaTdDJkSRzLJ07qCPrAiPYUvB7JFZnTT+nruFThiATyJMZsJOrsJx4q8mPqYbjJb5aZTjt7SAUN0zeneBWE=",
"http://schemas.microsoft.com/claims/authnmethodsreferences": "pwd,mfa",
"appid": "c44b4083-3bb0-49c1-b47d-974e53cbdf3c",
"appidacr": "2",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname": "Stoeltie",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname": "Ferdi",
"groups": "985d2338-c8bc-4c55-93cb-f90b1e34b3ed,ac67795f-6bad-4ecb-b8d7-be911d31e7e4,12bafa71-dc5e-4258-bb05-bbc996223da3,3738e0d1-d621-4570-9c38-76463baf5a3f,d8ca68fa-e9bb-45ff-8971-1825ed77b4f5,2ba38dfd-a2d9-4d1c-8e83-a76a69b1ebd3",
"ipaddr": "144.178.95.58",
"name": "Ferdi Stoeltie",
"http://schemas.microsoft.com/identity/claims/objectidentifier": "a1a2eac0-6a29-470b-8101-3106532c28fd",
"onprem_sid": "S-1-5-21-1977833990-800392848-2552735390-2570",
"puid": "10032000614610D9",
"rh": "0.AUgA7BYU-X831ki9mfKIF7zj3EZIf3kAutdPukPawfj2MBNIAPo.",
"http://schemas.microsoft.com/identity/claims/scope": "user_impersonation",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier": "klzQAajHXWfEVC20moxob409cbOdu3qzlg5_UO7GdDM",
"http://schemas.microsoft.com/identity/claims/tenantid": "f91416ec-377f-48d6-bd99-f28817bce3dc",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name": "ferdi.stoeltie@lagersmit.com",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn": "ferdi.stoeltie@lagersmit.com",
"uti": "8Fwx9r9rG02NrX5h1fwcAA",
"ver": "1.0",
"xms_tcdt": "1412679501"
},
"correlationId": "da5c76a2-305b-47ff-852d-555cc1fe1e8f",
"description": "",
"eventDataId": "ba2b009a-b63c-4b40-bcd7-3a670ed11df1",
"eventName": {
"value": "EndRequest",
"localizedValue": "End request"
},
"category": {
"value": "Policy",
"localizedValue": "Policy"
},
"eventTimestamp": "2023-04-03T12:15:22.6941244Z",
"id": "/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/resourceGroups/Dev-Portal-01_group/providers/Microsoft.Storage/storageAccounts/testdeleter/queueServices/default/queues/failplease/events/ba2b009a-b63c-4b40-bcd7-3a670ed11df1/ticks/638161209226941244",
"level": "Error",
"operationId": "da5c76a2-305b-47ff-852d-555cc1fe1e8f",
"operationName": {
"value": "Microsoft.Authorization/policies/deny/action",
"localizedValue": "'deny' Policy action."
},
"resourceGroupName": "Dev-Portal-01_group",
"resourceProviderName": {
"value": "Microsoft.Storage",
"localizedValue": "Microsoft.Storage"
},
"resourceType": {
"value": "Microsoft.Storage/storageAccounts/queueServices/queues",
"localizedValue": "Microsoft.Storage/storageAccounts/queueServices/queues"
},
"resourceId": "/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/resourceGroups/Dev-Portal-01_group/providers/Microsoft.Storage/storageAccounts/testdeleter/queueServices/default/queues/failplease",
"status": {
"value": "Failed",
"localizedValue": "Failed"
},
"subStatus": {
"value": "",
"localizedValue": ""
},
"submissionTimestamp": "2023-04-03T12:18:27Z",
"subscriptionId": "2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d",
"tenantId": "f91416ec-377f-48d6-bd99-f28817bce3dc",
"properties": {
"isComplianceCheck": "False",
"resourceLocation": null,
"ancestors": "management-group-root,f91416ec-377f-48d6-bd99-f28817bce3dc",
"policies": "[{\"policyDefinitionId\":\"/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/providers/Microsoft.Authorization/policyDefinitions/pol-sandbox-res-003\",\"policyDefinitionName\":\"pol-sandbox-res-003\",\"policyDefinitionDisplayName\":\"[pol-sandbox-res-003] BlockResourceTypesqueues\",\"policyDefinitionVersion\":\"0.1.0\",\"policyDefinitionEffect\":\"deny\",\"policyAssignmentId\":\"/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/providers/Microsoft.Authorization/policyAssignments/7530423b51484d90b6d748bf\",\"policyAssignmentName\":\"7530423b51484d90b6d748bf\",\"policyAssignmentDisplayName\":\"[pol-sandbox-res-003] BlockResourceTypesqueues\",\"policyAssignmentScope\":\"/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d\",\"policyAssignmentParameters\":{},\"policyAssignmentEnforcementMode\":\"Default\",\"policyExemptionIds\":[]},{\"policyDefinitionId\":\"/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/providers/Microsoft.Authorization/policyDefinitions/pol-sandbox-res-003\",\"policyDefinitionName\":\"pol-sandbox-res-003\",\"policyDefinitionDisplayName\":\"[pol-sandbox-res-003] BlockResourceTypesqueues\",\"policyDefinitionVersion\":\"0.1.0\",\"policyDefinitionEffect\":\"deny\",\"policyAssignmentId\":\"/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/resourceGroups/Dev-Portal-01_group/providers/Microsoft.Authorization/policyAssignments/b003d53de1fb4f3ca83913f8\",\"policyAssignmentName\":\"b003d53de1fb4f3ca83913f8\",\"policyAssignmentDisplayName\":\"[pol-sandbox-res-003] BlockResourceTypesqueues\",\"policyAssignmentScope\":\"/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/resourceGroups/Dev-Portal-01_group\",\"policyAssignmentParameters\":{},\"policyAssignmentEnforcementMode\":\"Default\",\"policyExemptionIds\":[]}]",
"eventCategory": "Policy",
"entity": "/subscriptions/2dda353d-ea8e-4c76-9e7d-0cbec6f34e5d/resourceGroups/Dev-Portal-01_group/providers/Microsoft.Storage/storageAccounts/testdeleter/queueServices/default/queues/failplease",
"message": "Microsoft.Authorization/policies/deny/action",
"hierarchy": ""
},
"relatedEvents": []
}
Does anyone know if there is a limitation in Azure policies regarding the above? Or a better method to implement such as a limit?
Kind regards
