Tutorial: Deploy a confidential container to Azure Container Instances via Azure portal
In this tutorial, you use Azure portal to deploy a confidential container to Azure Container Instances with a development confidential computing enforcement policy. After deploying the container, you can browse to the running application.
Note
When deploying confidential containers on Azure Container Instances via Portal you will only be able to deploy with a development confidential computing enforcement policy. This policy is only recommended for development and test workloads. Logging, and exec functionality are still available in the container group when using this policiy and software components are not validated. To full attest your container group while running production workloads, it is recommended that you deploy with a custom confidential computing enforcement policy via an Azure Resource Manager template. For more information, see the tutorial.
Sign in to Azure
Sign in to the Azure portal at https://portal.azure.com
If you don't have an Azure subscription, create a free account before you begin.
Create a confidential container on Azure Container Instances
On the Azure portal homepage, select Create a resource.
Select Containers > Container Instances.
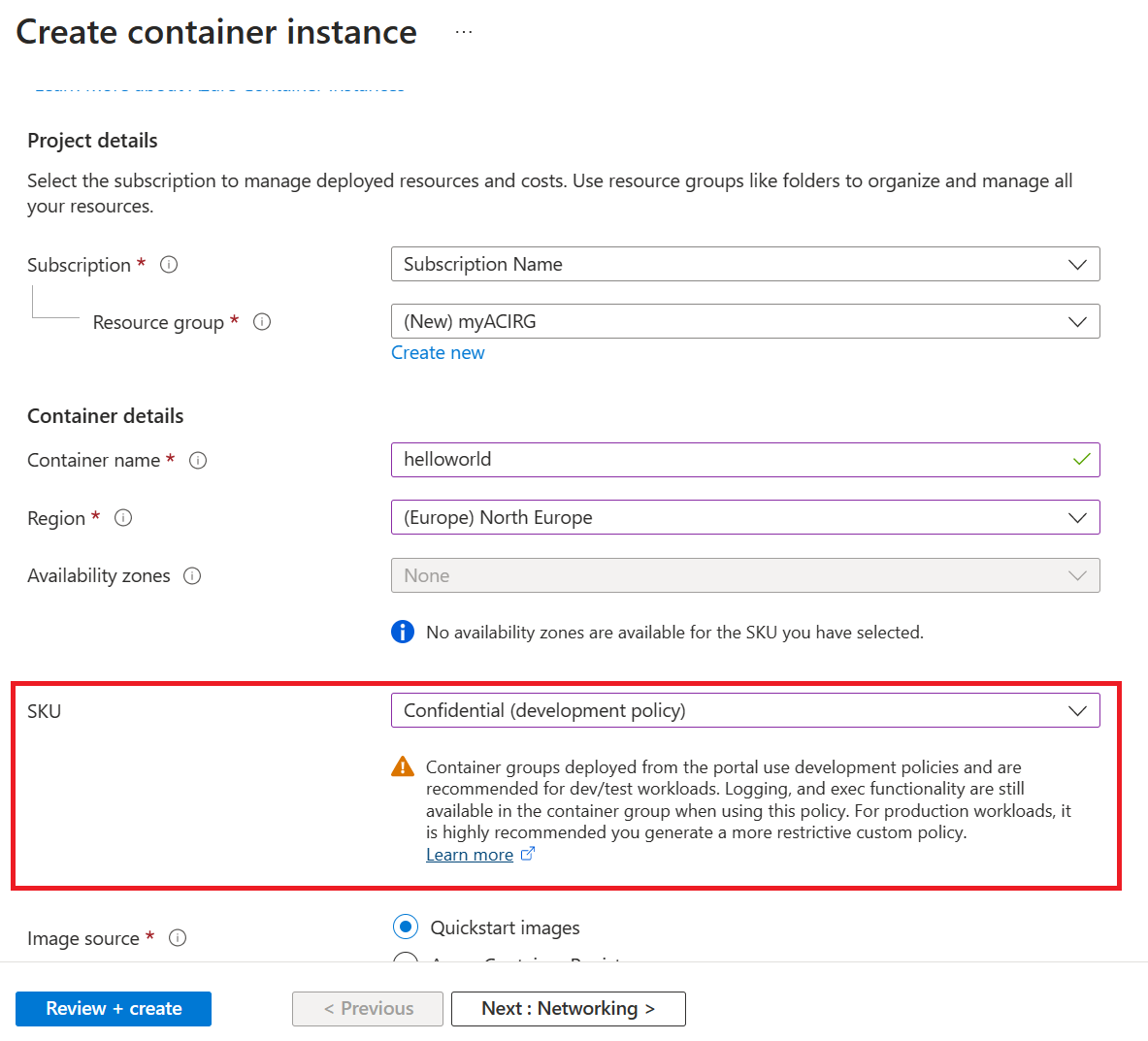
On the Basics page, choose a subscription and enter the following values for Resource group, Container name, Image source, and Container image.
- Resource group: Create new >
myresourcegroup - Container name:
helloworld - Region: One of
West Europe/North Europe/East US - SKU:
Confidential (development policy) - Image source: Quickstart images
- Container image:
mcr.microsoft.com/acc/samples/aci/helloworld:2.8(Linux)
Note
When deploying confidential containers on Azure Container Instances via Portal you will only be able to deploy with a development confidential computing enforcement policy. This policy is only recommended for development and test workloads. Logging, and exec functionality are still available in the container group when using this policiy and software components are not validated. To full attest your container group while running production workloads, it is recommended that you deploy with a custom confidential computing enforcement policy via an Azure Resource Manager template. For more information, see the tutorial.
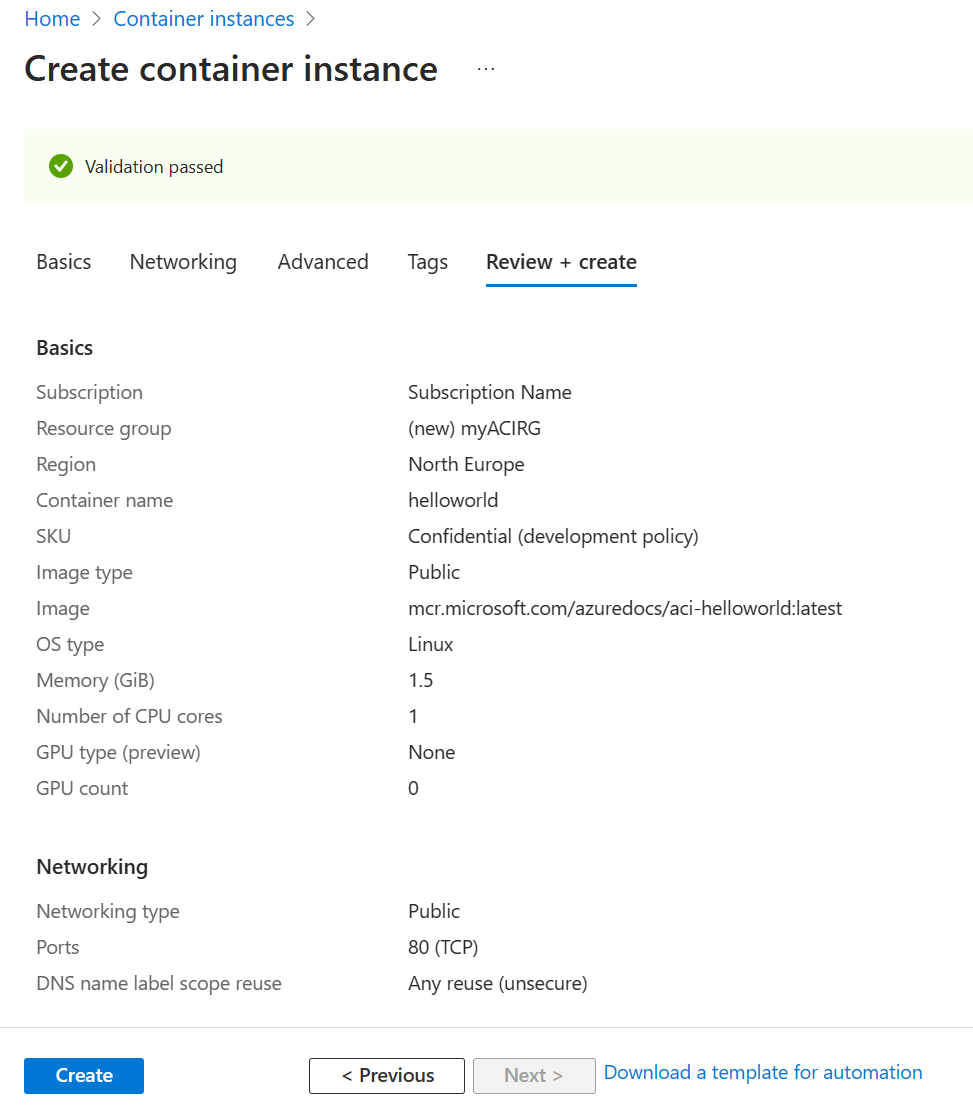
Leave all other settings as their defaults, then select Review + create.
When the validation completes, you're shown a summary of the container's settings. Select Create to submit your container deployment request.
When deployment starts, a notification appears that indicates the deployment is in progress. Another notification is displayed when the container group deployed.
Open the overview for the container group by navigating to Resource Groups > myACIRG > helloworld. Make a note of the IP of the container instance and its Status.
On the Overview page, note the Status of the instance and its IP address.
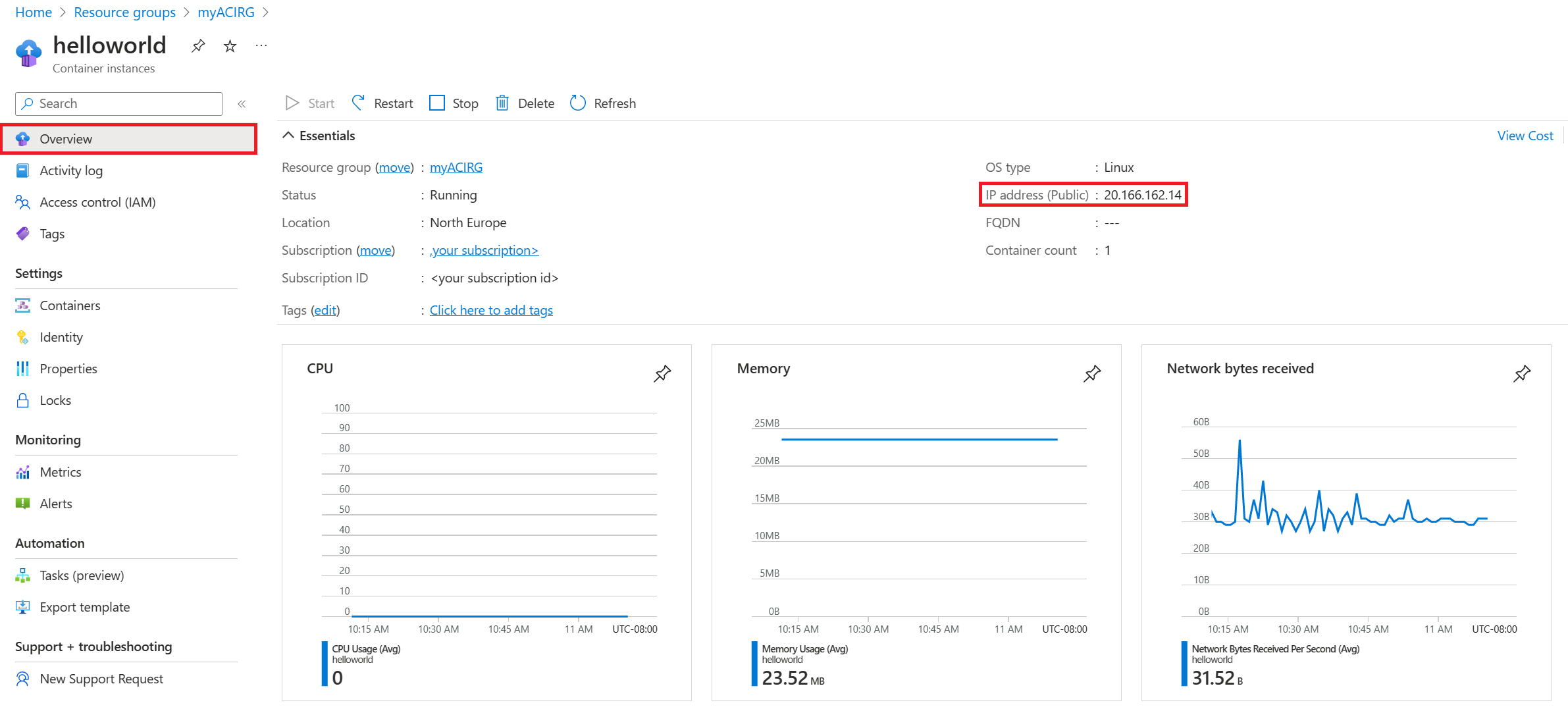
Once its status is Running, navigate to the IP address in your browser.

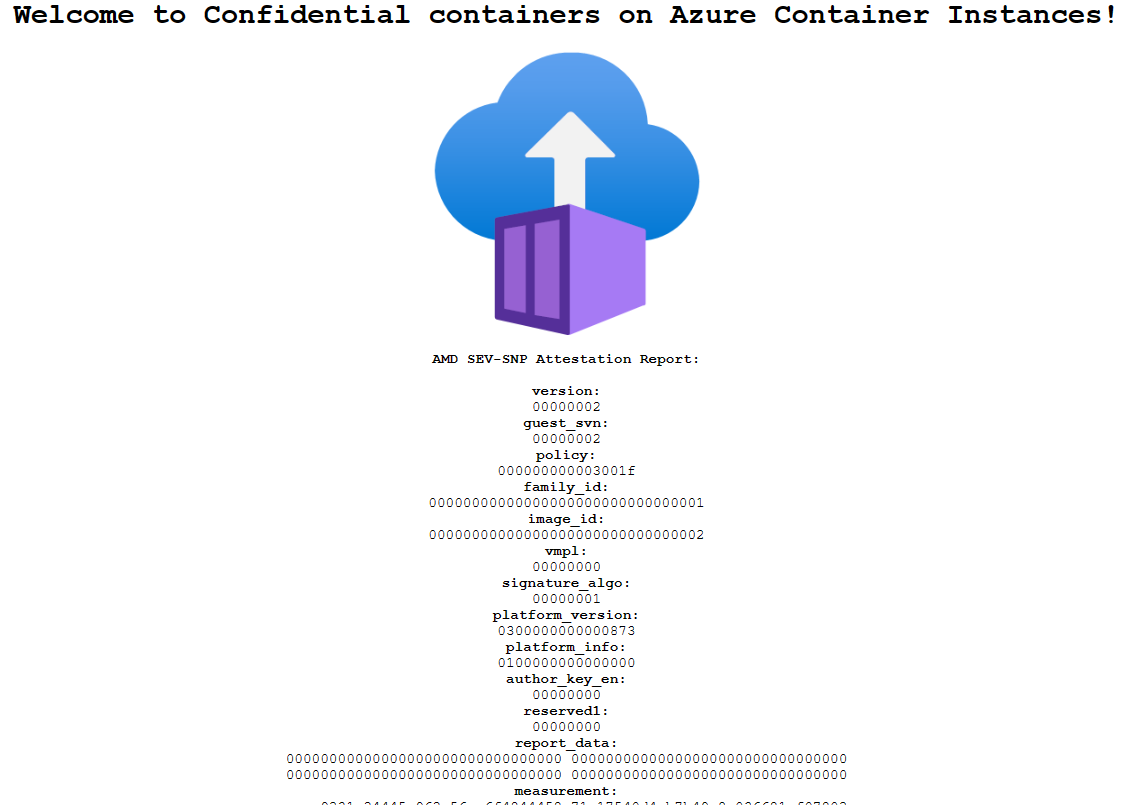
The presence of the attestation report below the Azure Container Instances logo confirms that the container is running on hardware that supports a hardware-based and attested trusted execution environment (TEE). If you deploy to hardware that doesn't support a TEE, for example by choosing a region where the ACI Confidential SKU isn't available, no attestation report is shown.
Congratulations! You deployed a confidential container on Azure Container Instances, which displays a hardware attestation report in your browser.
Clean up resources
When you're done with the container, select Overview for the helloworld container instance, then select Delete.
Next steps
In this tutorial, you created a confidential container on Azure Container instances with a development confidential computing enforcement policy. If you would like to deploy a confidential container group with a custom computing enforcement policy continue to the confidential containers on Azure Container Instances - deploy with Azure Resource Manager template tutorial.