Configure a cross-tenant connection in Azure Virtual Network Manager - portal
In this article, you'll learn how to create cross-tenant connections in Azure Virtual Network Manager by using the Azure portal. Cross-tenant support allows organizations to use a central network manager for managing virtual networks across tenants and subscriptions.
First, you'll create the scope connection on the central network manager. Then, you'll create the network manager connection on the connecting tenant and verify the connection. Last, you'll add virtual networks from different tenants to your network group and verify. After you complete all the tasks, you can centrally manage the resources of other tenants from a single network manager.
Prerequisites
- Two Azure tenants with virtual networks that you want to manage through Azure Virtual Network Manager. This article refers to the tenants as follows:
- Central management tenant: The tenant where an Azure Virtual Network Manager instance is installed, and where you'll centrally manage network groups from cross-tenant connections.
- Target managed tenant: The tenant that contains virtual networks to be managed. This tenant will be connected to the central management tenant.
- Azure Virtual Network Manager deployed in the central management tenant.
- These permissions:
- The administrator of the central management tenant has a guest account in the target managed tenant.
- The administrator guest account has Network Contributor permissions applied at the appropriate scope level (management group, subscription, or virtual network).
Need help with setting up permissions? Check out how to add guest users in the Azure portal and how to assign user roles to resources in the Azure portal.
Create a scope connection within a network manager
Creation of the scope connection begins on the central management tenant with a network manager deployed. This is the network manager where you plan to manage all of your resources across tenants.
In this task, you set up a scope connection to add a subscription from a target tenant:
Log in to the Azure portal on the central management tenant.
Search for Virtual network managers and select your network manager from the list.
Under Settings, select Cross-tenant connections, and then select Create cross-tenant connection.

On the Create a connection page, enter the connection name and target tenant information, and then select Create.

Verify that the scope connection is listed under Cross-tenant connections and the status is Pending.
Create a network manager connection on a subscription in another tenant
After you create the scope connection, switch to the target managed tenant. Connect to the target managed tenant by creating another cross-tenant connection in the Virtual Network Manager hub:
In the target tenant, search for Virtual network manager and select Virtual Network Managers.
Under Virtual Network Manager, select Cross-tenant connections.

Select + Create or Create a connection.

On the Create a connection page, enter the information for your central management tenant, and then select Create.

Verify the connection status
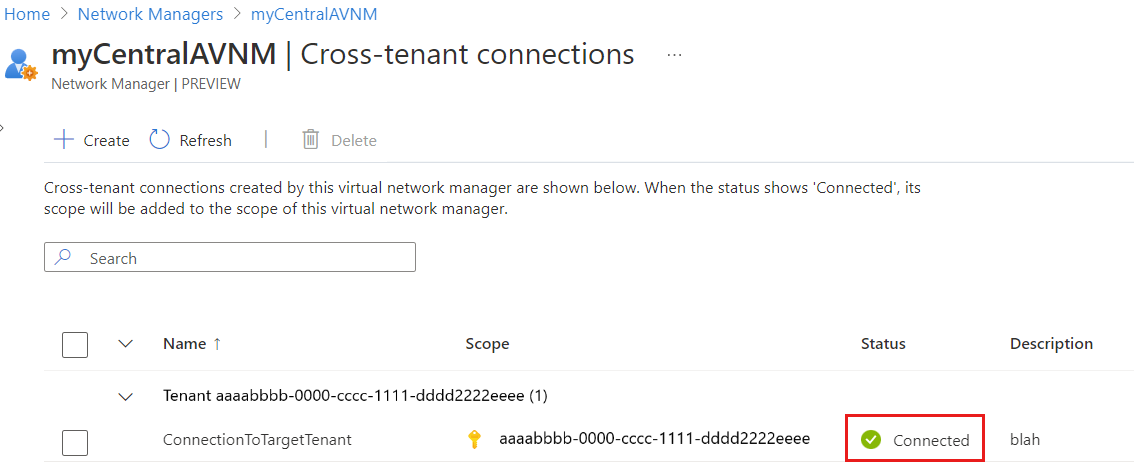
After you create both connections, it's time to verify the connection on the central management tenant:
On your central management tenant, select your network manager.
Select Cross-tenant connections under Settings, and verify that your cross-tenant connection is listed as Connected.
Add static members to a network group
Now, add virtual networks from both tenants into a network group for static members.
Note
Currently, cross-tenant connections support only static memberships within a network group. Dynamic membership with Azure Policy is not supported.
From your network manager, add a network group if needed.
Select your network group, and then select Add virtual networks under Manually add members.
On the Manually add members page, select Tenant:... next to the search box, select the linked tenant from the list, and then select Apply.

To view the available virtual networks from the target managed tenant, select Authenticate and proceed through the authentication process. If you have multiple Azure accounts, select the one you're currently signed in with that has permissions to the target managed tenant.
Select the virtual networks to include in the network group, and then select Add.
Verify group members
In the final step, you verify the virtual networks that are now members of the network group.
On the Overview page of the network group, select View group members. Verify that the virtual networks that you added manually are listed.
Next steps
In this article, you deployed a cross-tenant connection between two Azure subscriptions. To learn more about using Azure Virtual Network Manager, see:
