Configure Azure VPN Client – Microsoft Entra ID authentication – macOS
This article helps you configure your macOS client computer to connect to an Azure virtual network using a VPN Gateway point-to-site (P2S) connection. These steps apply to Azure VPN gateways configured for Microsoft Entra ID authentication. Microsoft Entra ID authentication only supports OpenVPN® protocol connections and requires the Azure VPN Client. The Azure VPN client for macOS is currently not available in France and China due to local regulations and requirements.
Prerequisites
Configure your VPN gateway for point-to-site VPN connections that specify Microsoft Entra ID authentication. See Configure a P2S VPN gateway for Microsoft Entra ID authentication.
Workflow
This article continues on from the Configure a P2S VPN gateway for Microsoft Entra ID authentication steps. This article helps you:
- Download and install the Azure VPN Client for macOS.
- Extract the VPN client profile configuration files.
- Import the client profile settings to the VPN client.
- Create a connection and connect to Azure.
Download the Azure VPN Client
- Download the latest Azure VPN Client from the Apple Store.
- Install the client on your computer.
Extract client profile configuration files
To configure your Azure VPN Client profile, you download a VPN client profile configuration package from the Azure P2S gateway. This package contains the necessary settings to configure the VPN client.
If you used the P2S server configuration steps as mentioned in the Prerequisites section, you've already generated and downloaded the VPN client profile configuration package that contains the VPN profile configuration files. If you need to generate configuration files, see Download the VPN client profile configuration package.
After you obtain the VPN client profile configuration package, extract the files.
Import VPN client profile configuration files
Note
We're in the process of changing the Azure VPN Client fields for Azure Active Directory to Microsoft Entra ID. If you see Microsoft Entra ID fields referenced in this article, but don't yet see those values reflected in the client, select the comparable Azure Active Directory values.
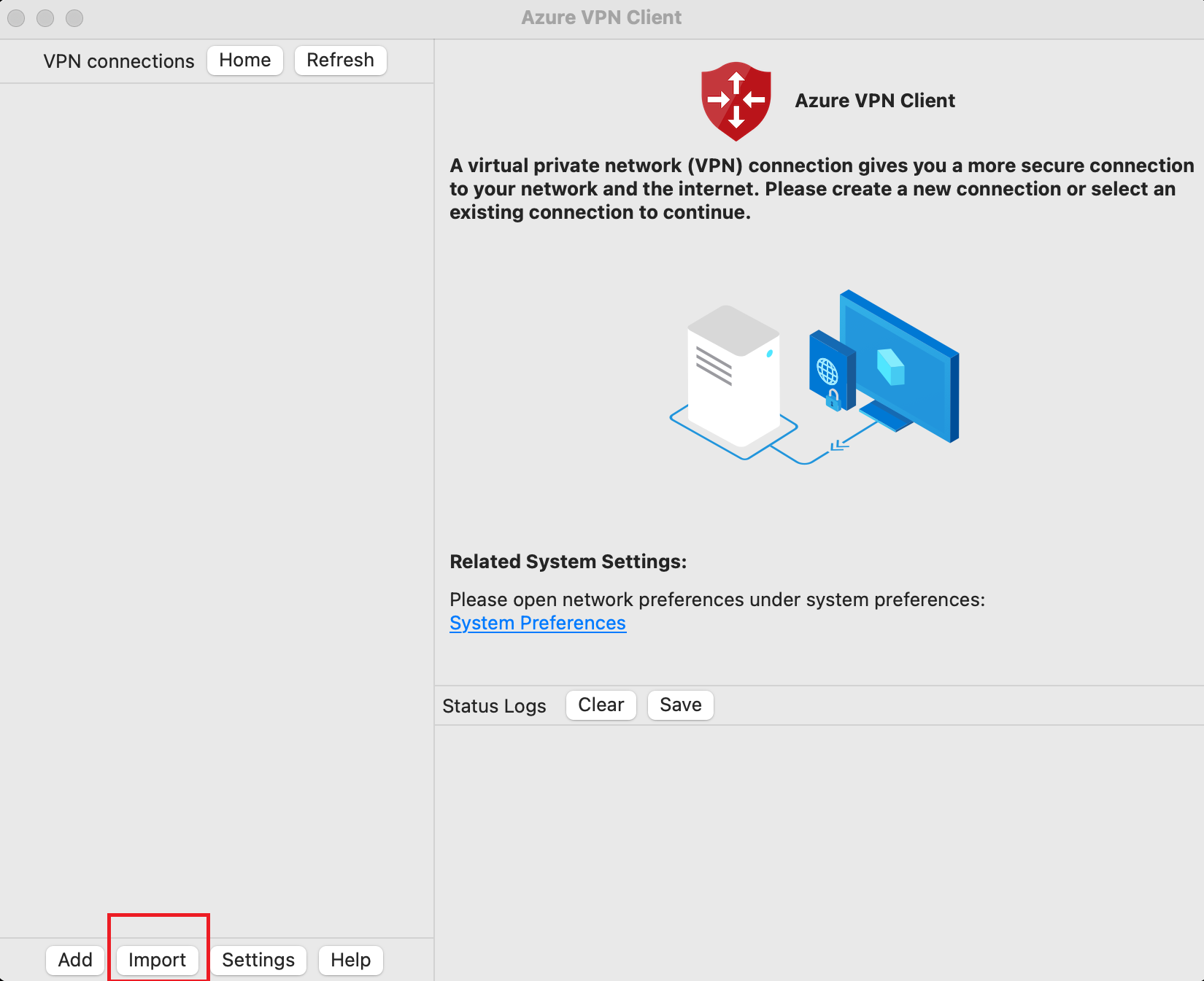
On the Azure VPN Client page, select Import.
Navigate to the folder containing the file that you want to import, select it, then click Open.
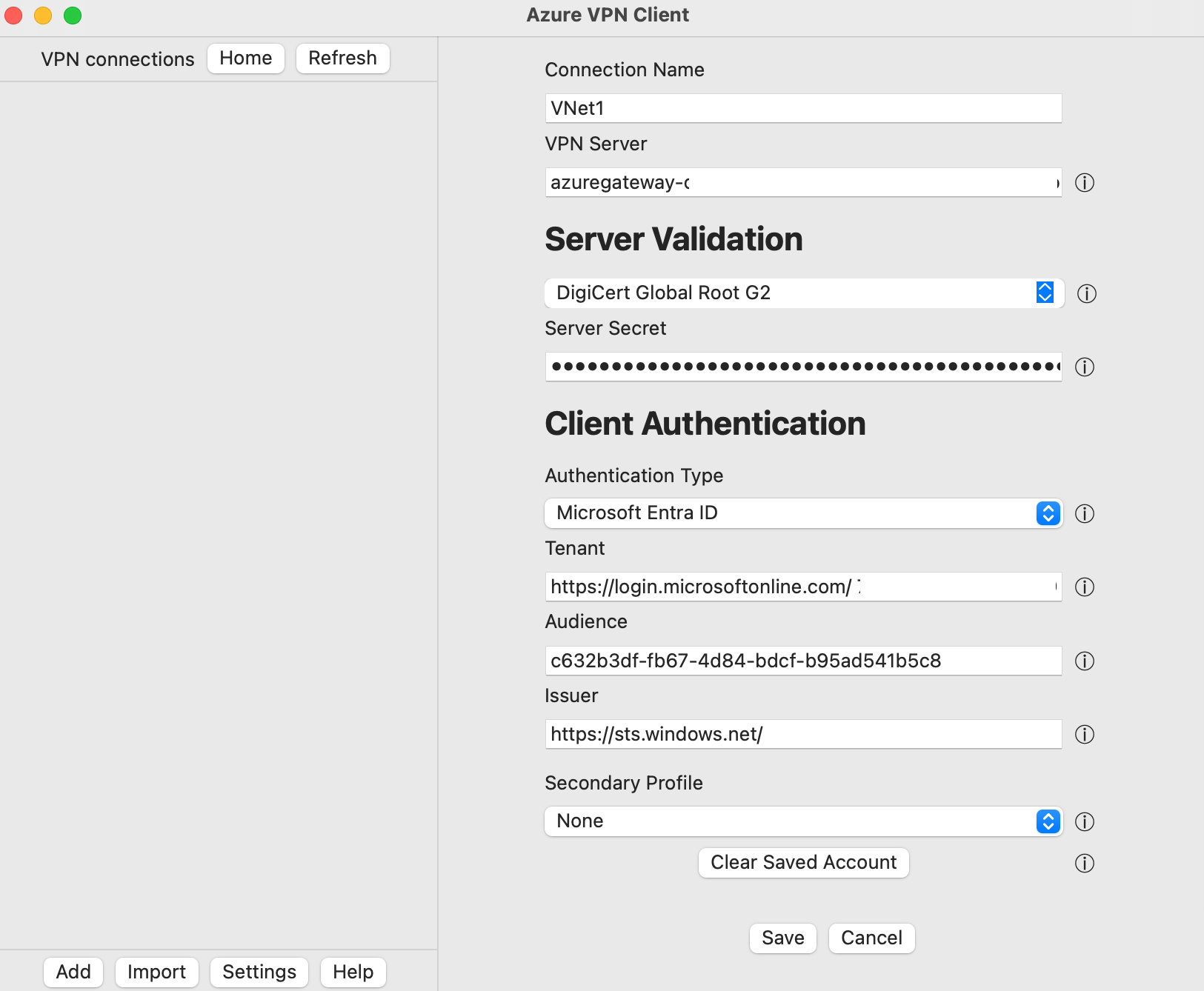
On this screen, notice the connection values are populated using the values in the imported VPN client configuration file.
- Verify that the Certificate Information value shows DigiCert Global Root G2, rather than the default or blank. Adjust the value if necessary.
- Notice the Client Authentication values align with the values that were used to configure the VPN gateway for Microsoft Entra ID authentication. The Audience value in this example aligns with the Microsoft-registered App ID for Azure Public. If your P2S gateway is configured for a different Audience value, this field must reflect that value.
Click Save to save the connection profile configuration.
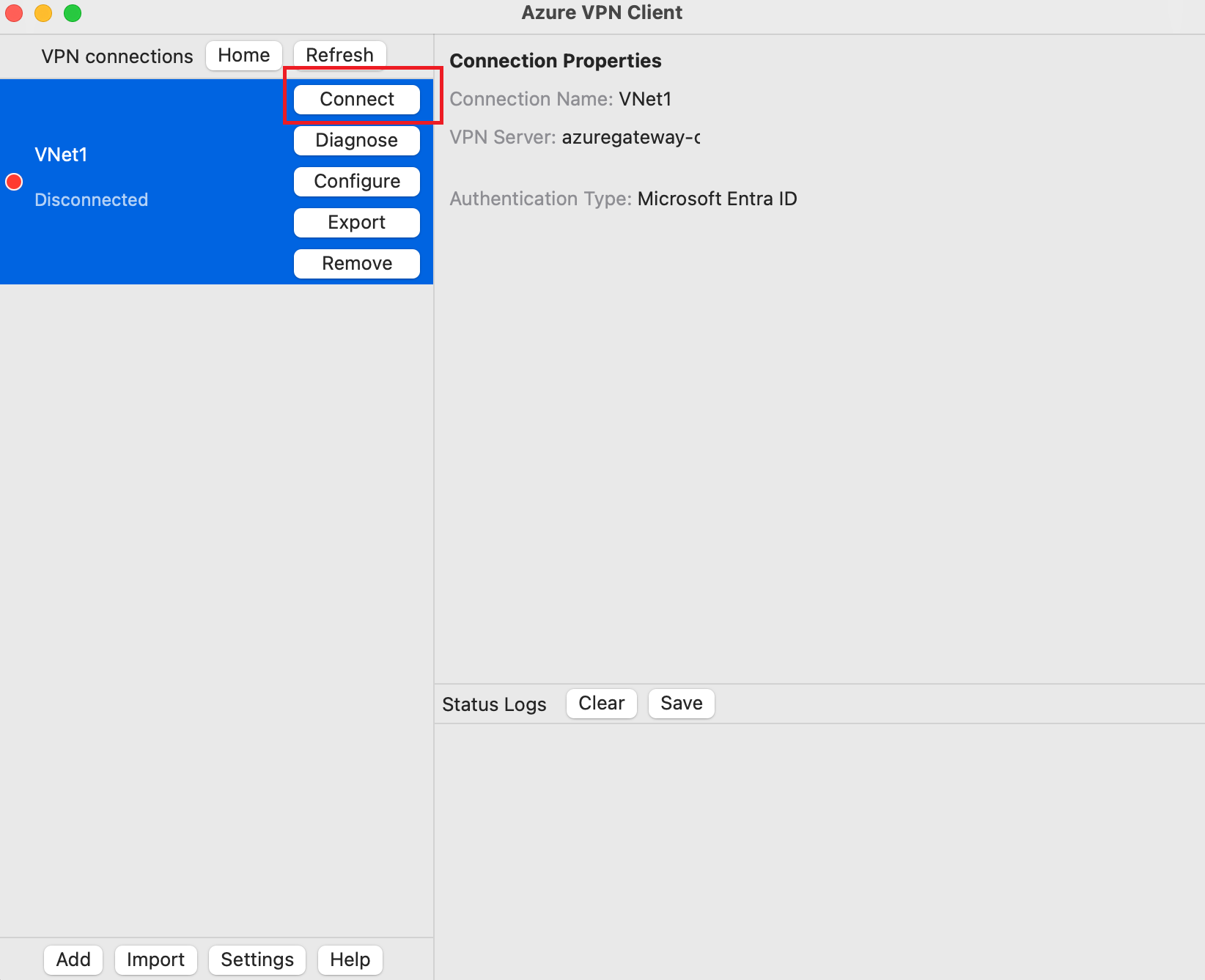
In the VPN connections pane, select the connection profile that you saved. Then, click Connect.
Once connected, the status changes to Connected. To disconnect from the session, click Disconnect.
Create a connection manually
Open the Azure VPN Client. At the bottom of the client, select Add to create a new connection.
On the Azure VPN Client page, you can configure the profile settings. Change the Certificate Information value to show DigiCert Global Root G2, rather than the default or blank, then click Save.
Configure the following settings:
- Connection Name: The name by which you want to refer to the connection profile.
- VPN Server: This name is the name that you want to use to refer to the server. The name you choose here doesn't need to be the formal name of a server.
- Server Validation
- Certificate Information: DigiCert Global Root G2
- Server Secret: The server secret.
- Client Authentication
- Authentication Type: Microsoft Entra ID
- Tenant: Name of the tenant.
- Audience: The Audience value must match the value that your P2S gateway is configured to use.
- Issuer: Name of the issuer.
After filling in the fields, click Save.
In the VPN connections pane, select the connection profile that you configured. Then, click Connect.
Remove a VPN connection profile
You can remove the VPN connection profile from your computer.
- Open the Azure VPN Client.
- Select the VPN connection that you want to remove, then click Remove.
Optional Azure VPN Client configuration settings
You can configure the Azure VPN Client with optional configuration settings such as additional DNS servers, custom DNS, forced tunneling, custom routes, and other additional settings. For a description of the available optional settings and configuration steps, see Azure VPN Client optional settings.
Next steps
For more information, see Create a Microsoft Entra tenant for P2S Open VPN connections that use Microsoft Entra authentication.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for