Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Most operations, support, and troubleshooting performed by Microsoft personnel (including subprocessors) don't require access to customer data. By using Power Platform Customer Lockbox, customers can review and approve (or reject) data access requests in the rare occasion when Microsoft needs access to customer data. Use it in cases where a Microsoft engineer needs to access customer data, whether in response to a customer-initiated support ticket or a problem identified by Microsoft.
This article covers how to enable Customer Lockbox and how lockbox requests are initiated, tracked, and stored for later reviews and audits.
Note
Customer Lockbox is available in public clouds and US Government Community Cloud (GCC), GCC High, and Department of Defense (DoD) regions.
Summary
You can enable Customer Lockbox for your data sources within your tenant. Enabling Customer Lockbox enforces the policy only for environments that are activated for Managed Environments. Power Platform administrators can enable the lockbox policy.
For more information, see Enable the lockbox policy.
In the rare occasion when Microsoft attempts to access customer data that's stored within Power Platform (for example, Dataverse), a lockbox request is sent to the Power Platform administrators for approval. For more information, see Review a lockbox request.
All updates to a lockbox request are recorded and made available to your organization as audit logs. For more information, see Audit lockbox requests.
Power Platform and Dynamics 365 applications and services store customer data in several Azure storage technologies. When you turn on Customer Lockbox for an environment, customer data associated with the respective environment is protected by the lockbox policy, irrespective of the storage type.
Note
- Currently, the applications and services where lockbox policy is enforced once enabled are Power Apps (excluding Cards for Power Apps), AI Builder, Power Pages, Power Automate, Microsoft Copilot Studio, Dataverse, Customer Insights, Customer Service, Sales (except conversation intelligence), Communities, Guides, Connected Spaces, Finance (except Lifecycle Services), Project Operations (except Lifecycle Services), Supply Chain Management (except Lifecycle Services), and the real-time marketing feature area of the Marketing app.
- Features powered by Azure OpenAI Service are excluded from Lockbox policy enforcement unless product documentation for a given feature states that Lockbox applies.
- Nuance Conversational IVR is excluded from Lockbox policy enforcement unless product documentation for a given feature states that Lockbox applies.
- Maker Welcome Content is excluded from Lockbox policy enforcement.
- You must disable Lucene.NET search from your website and move to Dataverse Search to be able to use Customer Lockbox. For more information, see Portals search using Lucene.NET search is deprecated.
Workflow
Your organization has an issue with Microsoft Power Platform and opens a support request with Microsoft Support. Alternatively, Microsoft proactively identifies a problem (for example, a proactive notification is triggered), and a Microsoft-initiated event is opened to investigate and mitigate or fix the root cause.
A Microsoft operator reviews the support request or event and attempts to troubleshoot the issue by using standard tools and telemetry. If the operator needs access to customer data for further troubleshooting, a Microsoft engineer starts an internal approval process for access to customer data, regardless of whether the lockbox policy is enabled.
If the respective data store is associated with an environment protected according to the lockbox policy enablement, the process also generates a lockbox request. The designated approvers (Power Platform administrators) receive an email notification about the pending data access request from Microsoft.
Important
The Microsoft engineer can't proceed with their investigation until the customer approves the lockbox request. This approval step could cause delays in addressing the support ticket or prolonged outages. Make sure you monitor email notifications and lockbox requests in the Power Platform admin center. Respond in a timely manner to avoid service interruptions.
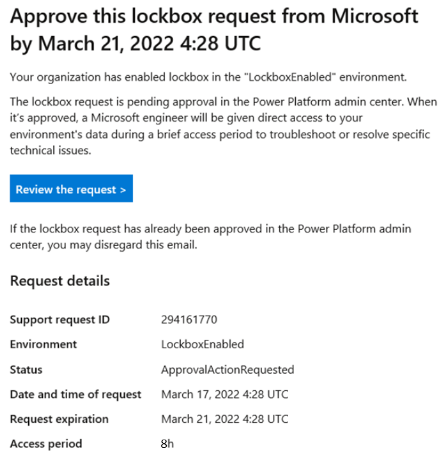
The approver signs into the Power Platform admin center and approves the request. If the approver rejects the request or doesn't approve it within four days, the request expires and the Microsoft engineer gets no access.
After the approver from your organization approves the request, the Microsoft engineer gets the elevated permissions that they initially requested and fixes your issue. Microsoft engineers have a set amount of time - eight hours - to fix the issue, after which, access is automatically revoked.
Enable the lockbox policy
Power Platform administrators can create or update the lockbox policy in the Power Platform admin center. Enabling the tenant level policy applies only to environments that are activated for Managed Environments. It can take up to 24 hours for all data sources and all environments to implement Customer Lockbox.
- Sign in to the Power Platform admin center.
- In the navigation pane, select Manage.
- In the Manage pane, select Tenant settings.
- Select Customer Lockbox, and then select Enable.
Review a lockbox request
Sign in to the Power Platform admin center.
In the navigation pane, select Security.
In the Security pane, select Compliance.
On the Compliance page, select Customer Lockbox.
Review the request details.
Field Description Support request ID The ID of the support ticket associated with the lockbox request. If the request is a result of Microsoft-initiated internal alert, the value is "Microsoft initiated". Environment The display name of the environment in which data access is being requested. Status The status of the lockbox request.
- Action needed: Pending approval from the customer
- Expired: No approval received from the customer
- Approved: Approved by the customer
- Denied: Denied by the customer
Requested The time at which the Microsoft engineer requested access to customer data in customer's environment. Request expiration The time by which the customer needs to approve the lockbox request. The status of the request change to Expired if no approval is given by this time. Access period The length of time the requestor wants to access customer data. This value is by default 8 hours and can't be changed. Access expiration If access is granted, this is the time until which the Microsoft engineer has access to customer data. Select a lockbox request, and then select Approve or Deny.
Note
The lockbox requests that have occurred in the past 28 days are displayed in the Recent table.
Once a request is approved, it can't be revoked for the entire duration of the access period of 8 hours.
Audit lockbox requests
Warning
The schema documented in this section for the lockbox audit events is deprecated and won't be available starting in July 2024. You can audit Customer Lockbox events using the new schema available at Activity category: Lockbox operations.
Actions related to accepting, denying, or expiration of a lockbox request are recorded automatically in Microsoft 365 Defender.
Audit traces include these and other fields for each lockbox request:
- Unique identifier for the request
- Request creation time
- Organization ID
- User ID (unique identifier for the Microsoft operator performing the request)
- Request status
- Associated support ticket ID
- Request expiration time
- Data access expiration time
- Environment ID
- Request justification
The Microsoft 365 Audit tab allows admins to search for events associated with lockbox sessions. View the Power Platform Lockbox category for Power Platform related lockbox events.
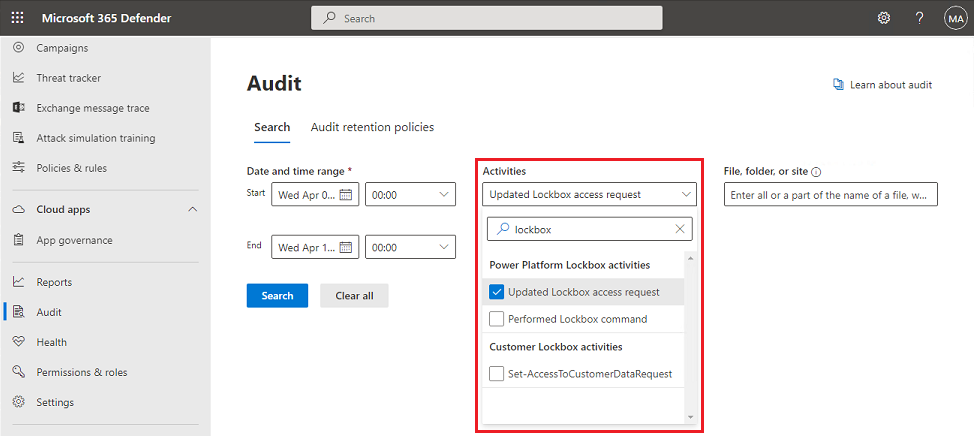
Admins can directly export the result set based on the filter criteria.
Customer Lockbox produces two types of audit logs:
- Logs that are initiated by Microsoft and correspond to lockbox request being created, expired, or when access sessions end. This set of audit logs don't correspond to a specific user ID since the actions are initiated by Microsoft.
- Logs that are initiated by end user actions, such as when a user approves or denies a lockbox request. If the user that performs these operations doesn't have an E5 license assigned, the logs are filtered out and won't show up in the audit logs.
By default, the audit logs are preserved for a duration of one year. You need a 10-Year Audit Log Retention add-on license to retain audit records for 10 years. See Audit (Premium) for more details on audit log retention.
Licensing requirements for Customer Lockbox
Customer Lockbox policy is enforced only on environments that are activated for Managed Environments. Managed Environments is included as an entitlement in standalone Power Apps, Power Automate, Microsoft Copilot Studio, Power Pages, and Dynamics 365 licenses that give premium usage rights. To learn more about Managed Environment licensing, see Licensing and Licensing overview for Microsoft Power Platform.
In addition, access to Customer Lockbox for Microsoft Power Platform and Dynamics 365 requires users in the environments where the Lockbox policy is enforced to have any of these subscriptions:
- Microsoft 365 or Office 365 A5/E5/G5
- Microsoft 365 A5/E5/F5/G5 Compliance
- Microsoft 365 F5 Security & Compliance
- Microsoft 365 A5/E5/F5/G5 Insider Risk Management
- Microsoft 365 A5/E5/F5/G5 Information Protection and Governance Learn more about applicable licenses.
Exclusions
Lockbox requests aren't triggered in the following engineering support scenarios:
Emergency scenarios that fall outside of standard operating procedures, such as a major service outage that requires immediate attention to recover or restore services in unexpected or unpredictable cases. These "break glass" events are rare and, in most instances, don't require any access to customer data to resolve.
A Microsoft engineer accesses the underlying platform as part of troubleshooting and is inadvertently exposed to customer data. It's rare that such scenarios would result in access to meaningful quantities of customer data.
Customer Lockbox requests are also not triggered by external legal demands for data. For details, refer to the discussion of government requests for data in the Microsoft Trust Center.
Customer Lockbox won't apply to the access and manual review of customer data shared for Copilot AI features. Customer Lockbox remains enabled for all in-scope data.
Known issues
- Tenant-to-tenant migration isn't supported when Customer Lockbox is enabled. You must disable Customer Lockbox to move an environment to another tenant. You can re-enable Customer Lockbox once the migration is completed.