Disable authentication as ARM template
Azure AD Tokens are used when registry users authenticate with ACR. By default, Azure Container Registry (ACR) accepts Azure AD Tokens with an audience scope set for Azure Resource Manager (ARM), a control plane management layer for managing Azure resources.
By disabling ARM Audience Tokens and enforcing ACR Audience Tokens, you can enhance the security of your container registries during the authentication process by narrowing the scope of accepted tokens.
With ACR Audience Token enforcement, only Azure AD Tokens with an audience scope specifically set for ACR will be accepted during the registry authentication and sign-in process. This means that the previously accepted ARM Audience Tokens will no longer be valid for registry authentication, thereby enhancing the security of your container registries.
In this tutorial, you learn how to:
- Disable authentication-as-arm in ACR - Azure CLI.
- Disable authentication-as-arm in the ACR - Azure portal.
Prerequisites
- Install or upgrade Azure CLI version 2.40.0 or later. To find the version, run
az --version. - Sign in to the Azure portal.
Disable authentication-as-arm in ACR - Azure CLI
Disabling azureADAuthenticationAsArmPolicy will force the registry to use ACR audience token. You can use Azure CLI version 2.40.0 or later, run az --version to find the version.
Run the command to show the current configuration of the registry's policy for authentication using ARM tokens with the registry. If the status is
enabled, then both ACRs and ARM audience tokens can be used for authentication. If the status isdisabledit means only ACR's audience tokens can be used for authentication.az acr config authentication-as-arm show -r <registry>Run the command to update the status of the registry's policy.
az acr config authentication-as-arm update -r <registry> --status [enabled/disabled]
Disable authentication-as-arm in the ACR - Azure portal
Disabling authentication-as-arm property by assigning a built-in policy will automatically disable the registry property for the current and the future registries. This automatic behavior is for registries created within the policy scope. The possible policy scopes include either Resource Group level scope or Subscription ID level scope within the tenant.
You can disable authentication-as-arm in the ACR, by following below steps:
Sign in to the Azure portal.
Refer to the ACR's built-in policy definitions in the azure-container-registry-built-in-policy definition's.
Assign a built-in policy to disable authentication-as-arm definition - Azure portal.
Assign a built-in policy definition to disable ARM audience token authentication - Azure portal.
You can enable registry's Conditional Access policy in the Azure portal.
Azure Container Registry has two built-in policy definitions to disable authentication-as-arm, as below:
Container registries should have ARM audience token authentication disabled.- This policy will report, block any non-compliant resources, and also sends a request to update non-compliant to compliant.Configure container registries to disable ARM audience token authentication.- This policy offers remediation and updates non-compliant to compliant resources.Sign in to the Azure portal.
Navigate to your Azure Container Registry > Resource Group > Settings > Policies .
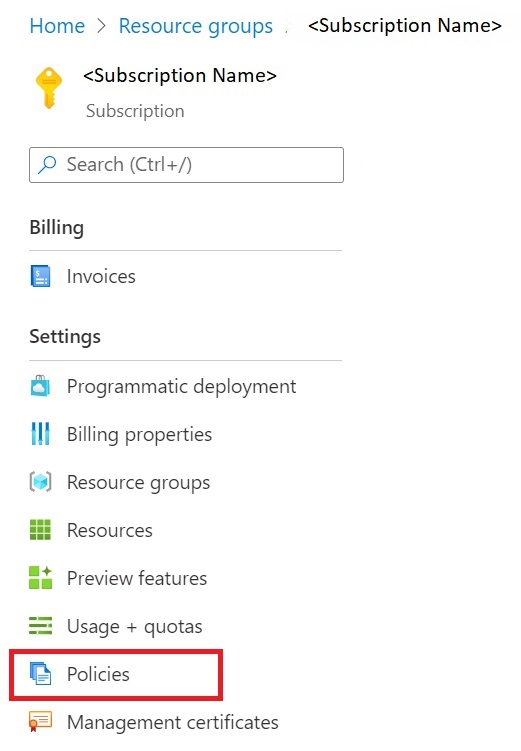
Navigate to Azure Policy, On the Assignments, select Assign policy.
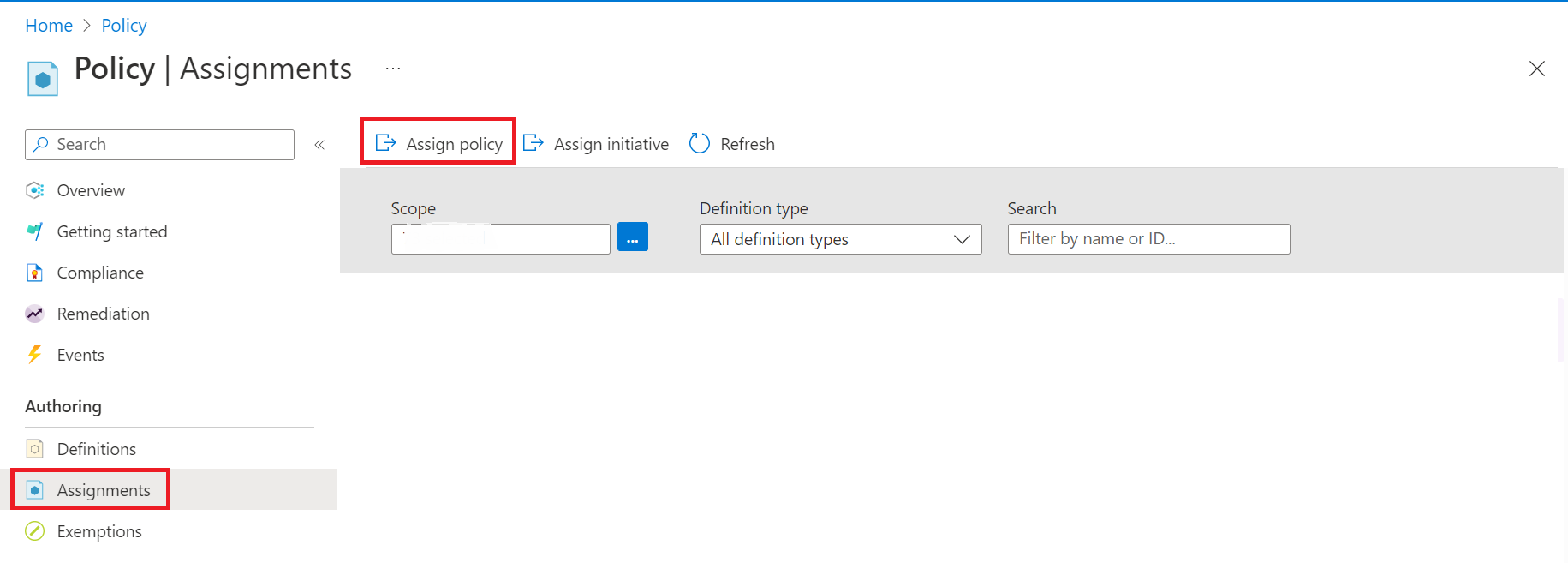
Under the Assign policy , use filters to search and find the Scope, Policy definition, Assignment name.

Select Scope to filter and search for the Subscription and ResourceGroup and choose Select.

Select Policy definition to filter and search the built-in policy definitions for the Conditional Access policy.

Use filters to select and confirm Scope, Policy definition, and Assignment name.
Use the filters to limit compliance states or to search for policies.
Confirm your settings and set policy enforcement as enabled.
Select Review+Create.
