Make indexer connections to Azure Storage as a trusted service
In Azure AI Search, indexers that access Azure blobs can use the trusted service exception to securely access blobs. This mechanism offers customers who are unable to grant indexer access using IP firewall rules a simple, secure, and free alternative for accessing data in storage accounts.
Note
If Azure Storage is behind a firewall and in the same region as Azure AI Search, you won't be able to create an inbound rule that admits requests from your search service. The solution for this scenario is for search to connect as a trusted service, as described in this article.
Prerequisites
A search service with a system-assigned managed identity (see check service identity).
A storage account with the Allow trusted Microsoft services to access this storage account network option (see check network settings).
An Azure role assignment in Azure Storage that grants permissions to the search service system-assigned managed identity (see check permissions).
Note
In Azure AI Search, a trusted service connection is limited to blobs and ADLS Gen2 on Azure Storage. It's unsupported for indexer connections to Azure Table Storage and Azure Files.
A trusted service connection must use a system managed identity. A user-assigned managed identity isn't currently supported for this scenario.
Check service identity
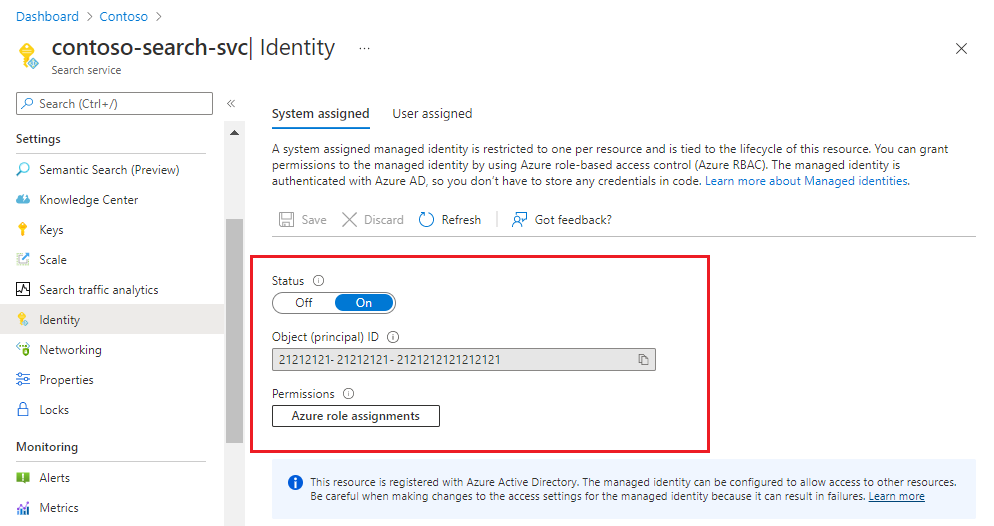
Sign in to the Azure portal and find your search service.
On the Identity page, make sure that a system assigned identity is enabled. Remember that user-assigned managed identities, currently in preview, won't work for a trusted service connection.
Check network settings
Sign in to the Azure portal and find your storage account.
In the left navigation pane under Security + networking, select Networking.
On the Firewalls and virtual networks tab, allow access from Selected networks.
Scroll down to the Exceptions section.
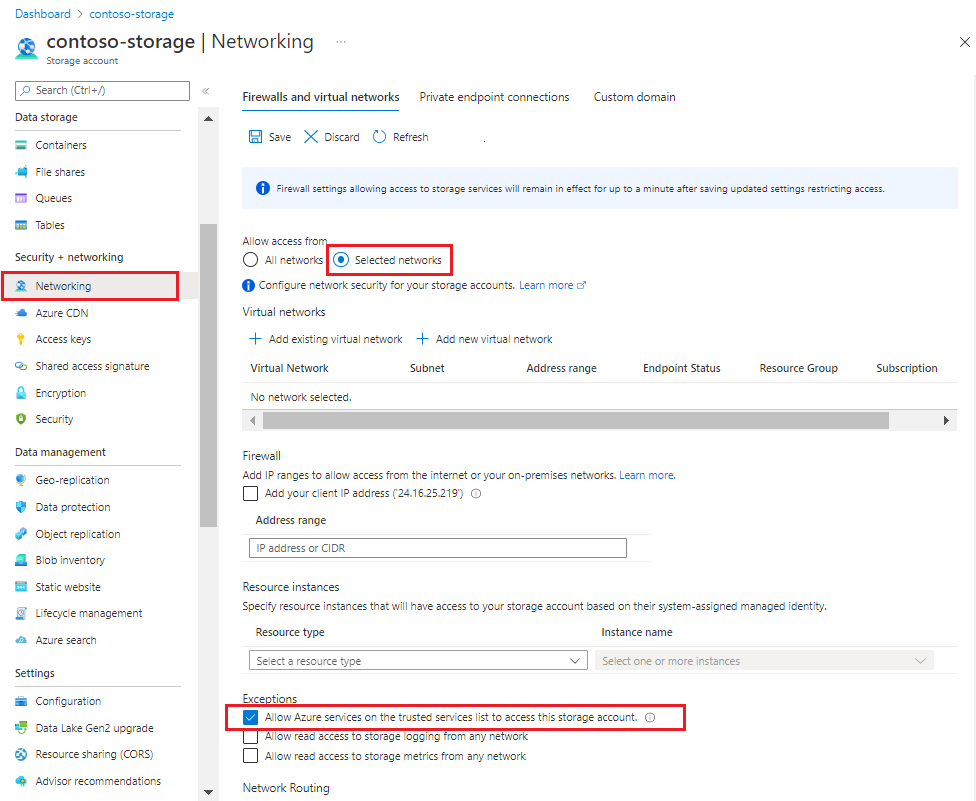
Make sure the checkbox is selected for Allow Azure services on the trusted services list to access this storage account.
Assuming your search service has role-based access to the storage account, it can access data even when connections to Azure Storage are secured by IP firewall rules.
Check permissions
A system managed identity is a Microsoft Entra service principal. The assignment needs Storage Blob Data Reader at a minimum.
In the left navigation pane under Access Control, view all role assignments and make sure that Storage Blob Data Reader is assigned to the search service system identity.
Add Storage Blob Data Contributor if write access is required.
Features that require write access include enrichment caching, debug sessions, and knowledge store.
Set up and test the connection
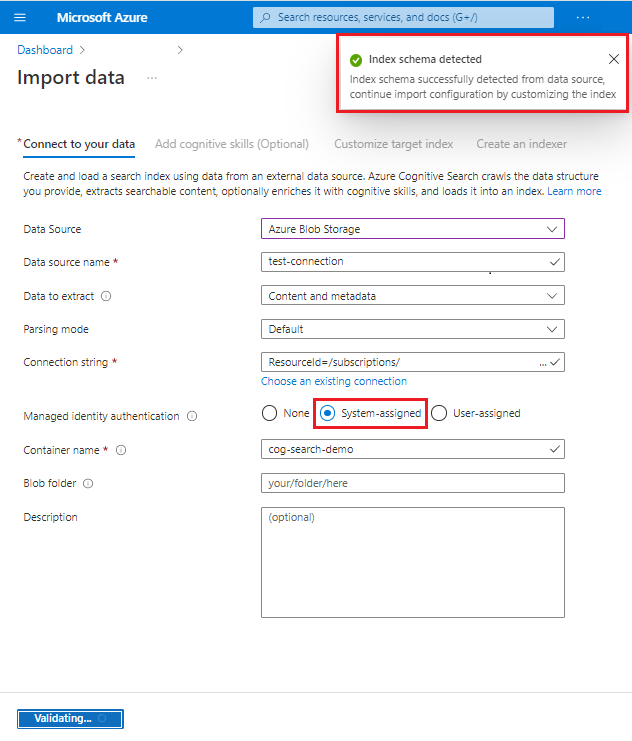
The easiest way to test the connection is by running the Import data wizard.
Start the Import data wizard, selecting the Azure Blob Storage or Azure Data Lake Storage Gen2.
Choose a connection to your storage account, and then select System-assigned. Select Next to invoke a connection. If the index schema is detected, the connection succeeded.