Introduction to malware scanning
Malware scanning in Microsoft Defender for Storage improves the security of your Azure Storage accounts by detecting and mitigating malware threats. It uses Microsoft Defender Antivirus to scan your storage content, ensuring security and compliance.
Defender for Storage offers two types of malware scanning:
On-upload malware scanning: Scans blobs automatically when they're uploaded or modified, providing near real-time detection. This type of scanning is ideal for applications that involve frequent user uploads, such as web applications or collaborative platforms. Scanning content as it is uploaded helps prevent malicious files from entering your storage environment and propagated downstream.
On-demand malware scanning: Lets you scan existing blobs whenever necessary, making it ideal for incident response, compliance, and proactive security. This scanning type is ideal for establishing a security baseline by scanning all existing data, reacting to security alerts, or preparing for audits.
These options help you protect your storage accounts, meet compliance needs, and maintain data integrity.
Why malware scanning is important
Content uploaded to cloud storage can introduce malware, posing risks to your organization. Scanning content for malware helps prevent malicious files from entering or spreading within your environment.
Malware scanning in Defender for Storage helps by:
Detecting malicious content: Identifies and mitigates malware threats.
Enhancing security posture: Adds a security layer to prevent malware spread.
Supporting compliance: Helps meet regulatory requirements.
Simplifying security management: Offers a cloud-native, low-maintenance solution configurable at scale.
Key features
- A built-in SaaS solution: Allows simple enabling at scale with zero maintenance.
- Comprehensive antimalware capabilities: Scanning with Microsoft Defender Antivirus (MDAV), catching polymorphic and metamorphic malware.
- Comprehensive detection: Scans all file types, including archives like ZIP and RAR files, up to 2 GB per blob.
- Flexible scanning options: Offers on-upload and on-demand scanning based on your needs.
- Integration with security alerts: Generates detailed alerts in Microsoft Defender for Cloud.
- Support for automation: Enables automated responses using Azure services like Logic Apps and Function Apps.
- Compliance and auditing: Logs scan results for compliance and auditing.
- Private endpoint support: Malware scanning supports private endpoints, ensuring data privacy by eliminating public internet exposure.
What kind of malware scanning works for your needs?
If you want immediate protection for frequent uploads, then on-upload malware scanning is the right choice. It works best for scanning user-uploaded content in web apps, protecting shared multimedia assets, and ensuring compliance in regulated sectors. On-upload scanning is also effective if you need to integrate third-party data, safeguard collaborative platforms, or secure data pipelines and machine learning datasets. For more information, see On-upload malware scanning.
If you want to establish security baselines, on-demand malware scanning is a great choice. It also offers flexibility to run scans based on specific needs. On-demand scanning fits well into incident response, compliance, and proactive security practices. You can use it to automate scans in response to security triggers, prepare for audits with scheduled scans, or proactively check stored data for malware. Additionally, on-demand scanning helps provide customer assurance and verify data before archiving or exchange. For more information, see On-demand malware scanning.
Provide scan results
Malware scanning scan results are available through four methods. After setup, you'll see scan results as blob index tags for every scanned file in the storage account, and as Microsoft Defender for Cloud security alerts when a file is identified as malicious.
You might choose to configure extra scan result methods, such as Event Grid and Log Analytics; these methods require extra configuration. In the next section, you'll learn about the different scan result methods.
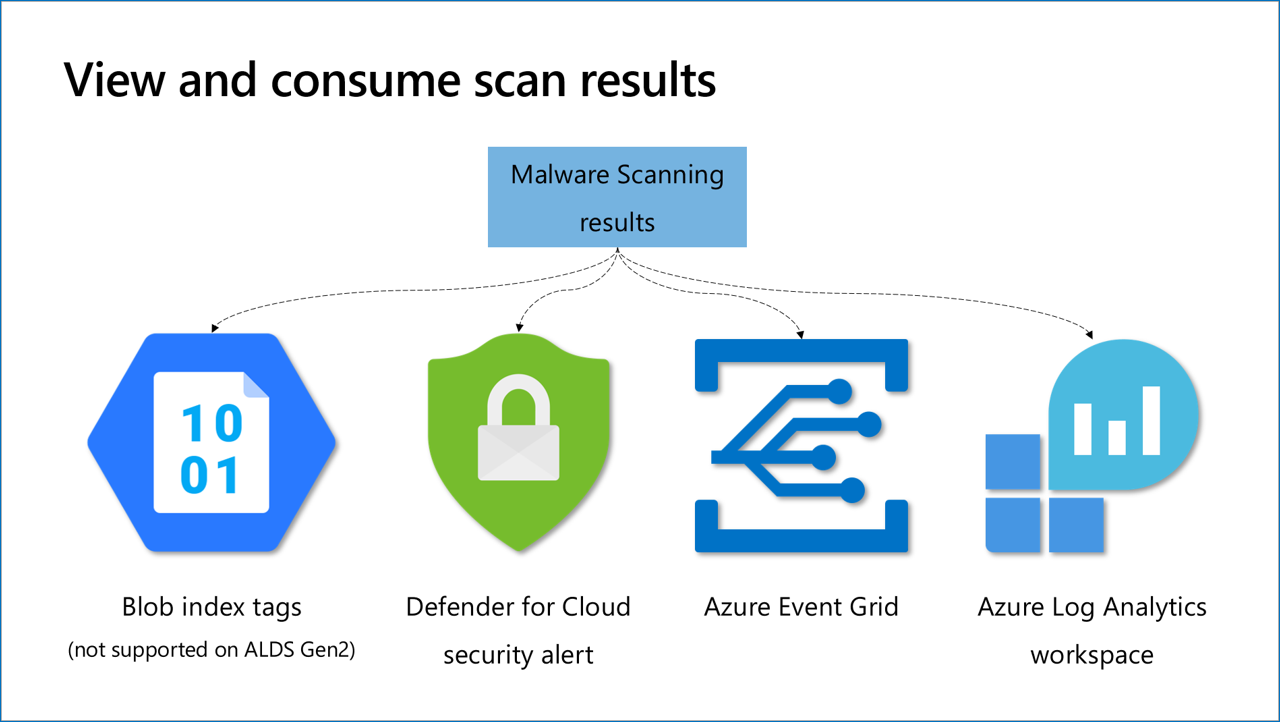
Scan results
Blob index tags
Blob index tags are metadata fields on a blob. They categorize data in your storage account using key-value tag attributes. These tags are automatically indexed and exposed as a searchable multi-dimensional index to easily find data. The scan results are concise, displaying malware scanning scan result and malware scanning scan time UTC in the blob metadata. Other result types (alerts, events, logs) provide more information.

Applications can use blob index tags to automate workflows, but they aren't tamper-resistant. Read more on setting up response.
Note
Access to index tags requires permissions. For more information, see Get, set, and update blob index tags.
Defender for Cloud security alerts
When a malicious file is detected, Microsoft Defender for Cloud generates a Microsoft Defender for Cloud security alert. To see the alert, go to Microsoft Defender for Cloud security alerts. The security alert contains details and context on the file, the malware type, and recommended investigation and remediation steps. To use these alerts for remediation, you can:
- View security alerts in the Azure portal by navigating to Microsoft Defender for Cloud > Security alerts.
- Configure automations based on these alerts.
- Export security alerts to a SIEM. You can continuously export security alerts Microsoft Sentinel (Microsoft’s SIEM) using Microsoft Sentinel connector, or another SIEM of your choice.
Learn more about responding to security alerts.
Event Grid event
Event Grid is useful for event-driven automation. It's the fastest method to get results with minimum latency in a form of events that you can use for automating response.
Events from Event Grid custom topics can be consumed by multiple endpoint types. The most useful for malware scanning scenarios are:
- Function App (previously called Azure Function) – use a serverless function to run code for automated response like move, delete, or quarantine.
- Webhook – to connect an application.
- Event Hubs & Service Bus Queue – to notify downstream consumers. Learn how to configure malware scanning so that every scan result is sent automatically to an Event Grid topic for automation purposes.
Logs analytics
You might want to log your scan results for compliance evidence or investigating scan results. By setting up a Log Analytics Workspace destination, you can store every scan result in a centralized log repository that is easy to query. You can view the results by navigating to the Log Analytics destination workspace and looking for the StorageMalwareScanningResults table.
Learn more about setting up logging for malware scanning.
Tip
We invite you to explore the malware scanning feature in Defender for Storage through our hands-on lab. Follow the Ninja training instructions for a detailed, step-by-step guide on how to set up and test malware scanning end-to-end, including configuring responses to scanning results. This is part of the 'labs' project that helps customers get ramped up with Microsoft Defender for Cloud and provide hands-on practical experience with its capabilities.
Response automation
Malware Scanning supports automated responses, such as deleting or quarantining suspicious files. This can be managed using blobs' index tags or by setting up Event Grid events for automation purposes. You can automate responses in the following ways:
- Block access to unscanned or malicious files using ABAC (Attribute-Based Access Control).
- Automatically delete or move malicious files to quarantine using Logic Apps (based on security alerts) or Event Grid with Function Apps (based on scan results).
- Forward clean files to a different location using Event Grid with Function Apps.
Learn more about setting up response for malware scanning results.
Malware scanning setup
When malware scanning is enabled, the following actions automatically take place in your environment:
- For each storage account you enable malware scanning on, an Event Grid System Topic resource is created in the same resource group of the storage account - used by the malware scanning service to listen on blob upload triggers. Removing this resource breaks the malware scanning functionality.
- To scan your data, the Malware Scanning service requires access to your data. During service enablement, a new Data Scanner resource called
StorageDataScanneris created in your Azure subscription and assigned with a system-assigned managed identity. This resource is granted with the Storage Blob Data Owner role assignment permitting it to access your data for purposes of Malware Scanning and Sensitive Data Discovery. If your storage account Networking configuration is set to Enable Public network access from selected virtual networks and IP addressed, theStorageDataScannerresource is added to the Resource instances section under storage account Networking configuration to allow access to scan your data. If you're enabling malware scanning at the subscription level, a new resource calledStorageAccounts/securityOperators/DefenderForStorageSecurityOperatoris created in your Azure subscription. This resource is assigned a system-managed identity. It's used to enable and repair Defender for Storage and Malware Scanning configurations on existing storage accounts. Additionally, it checks for new storage accounts created in the subscription to enable malware scanning. This resource has specific role assignments with the necessary permissions to enable malware scanning.
Note
Malware scanning depends on certain resources, identities, and networking settings to function properly. If you modify or delete any of these, malware scanning will stop working. To restore its normal operation, you can turn it off and on again.
Supported content and limitations
Supported content
File types: All file types, including archives like ZIP files.
File size: Blobs up to 2 GB in size.
Limitations
Unsupported storage accounts: Legacy v1 storage accounts aren't supported.
Unsupported service: Malware scanning doesn't support Azure Files.
Unsupported blob types: Append blobs and page blobs aren't supported.
Unsupported encryption: Client-side encrypted blobs can't be scanned, as the service can't decrypt them. Blobs encrypted at rest with Customer Managed Keys (CMK) are supported.
Unsupported protocols: Blobs uploaded via the Network File System (NFS) 3.0 protocol aren't scanned.
Blob index tags: Index tags aren't supported for storage accounts with hierarchical namespace enabled (Azure Data Lake Storage Gen2).
Unsupported regions: Some regions aren't yet supported for malware scanning. The service is continuously expanding to new regions. For the latest list of supported regions, see Defender for Cloud Availability.
Other costs
Azure Services: Malware scanning uses other Azure services, which might incur further costs:
- Azure Storage read operations
- Azure Storage blob indexing
- Azure Event Grid events
Blob scans and impact on IOPS
Each time the malware scanning service scans a file, it triggers another read operation and updates the index tag. This applies to both on-upload scanning, which occurs after the blob is uploaded or modified, and on-demand scanning. Despite these operations, access to the scanned data remains unaffected. The impact on storage Input/Output Operations Per Second (IOPS) is minimal, ensuring these operations typically don't introduce significant load.
Scenarios where malware scanning is ineffective
While malware scanning provides comprehensive detection capabilities, there are specific scenarios where it becomes ineffective due to inherent limitations. It's important to evaluate these scenarios carefully before deciding to enable malware scanning on a storage account:
- Chunked data: Malware scanning doesn't effectively detect malware in blobs that contain chunked data, for example, files split into smaller parts. This issue is common in backup services that upload backup data in chunks to storage accounts. The scanning process might miss malicious content or incorrectly flag clean content, leading to false negatives and false positives. To mitigate this risk, consider implementing further security measures, such as scanning data, before it's chunked, or after it's been fully reassembled.
- Encrypted data: Malware scanning doesn't support client-side encrypted data. This data can't be decrypted by the service, meaning any malware within these encrypted blobs go undetected. If encryption is necessary, ensure that scanning occurs before the encryption process, or use supported encryption methods like Customer Managed Keys (CMK) for encryption at rest. When deciding to enable malware scanning, consider if other supported files are being uploaded to the storage account. Also, assess if attackers could exploit this upload stream to introduce malware.
Differences in malware detection between Azure Storage and endpoint environments
Defender for Storage utilizes the same antimalware engine and up-to-date signatures as Defender for Endpoint to scan for malware. However, when files are uploaded to Azure Storage, they lack certain metadata that the antimalware engine depends on. This lack of metadata can lead to a higher rate of missed detections, known as 'false negatives,' in Azure Storage compared to those detections identified by Defender for Endpoint.
The following are some examples of missing metadata:
Mark of the Web (MOTW): MOTW is a Windows security feature that tracks files downloaded from the internet. However, when files are uploaded to Azure Storage, this metadata isn't preserved.
File path context: On standard operating systems, the file path can provide more context for threat detection. For example, a file trying to modify system locations (for example,
C:\Windows\System32) would be flagged as suspicious and be subject to further analysis. In Azure Storage, the context of specific file paths within the blob can't be utilized in the same way.Behavioral data: Defender for Storage analyzes the contents of files without running them. It inspects the files and might emulate their execution to check for malware. However, this approach might not detect certain types of malware that reveal their malicious nature only during execution.
Access and data privacy
Data access requirements
The Malware Scanning service requires access to your data to scan for malware. During service enablement, a new Data Scanner resource called StorageDataScanner is created in your Azure subscription. This resource is assigned a system-assigned managed identity and given the Storage Blob Data Owner role assignment to access and scan your data.
If your storage account networking configuration is set to Enable Public network access from selected virtual networks and IP addresses, the StorageDataScanner resource is added to the Resource instances section under the storage account networking configuration to allow scanning access.
Data privacy and regional processing
Regional processing: Scanning occurs within the same Azure region as your storage account to comply with data residency requirements.
Data handling: Scanned files aren't stored. In some cases, file metadata (for example, SHA-256 hash) might be shared with Microsoft Defender for Endpoint for further analysis.
Handle possible false positives and false negatives
False positives
False positives occur when the system incorrectly identifies a benign file as malicious. To address these issues:
Submit for analysis
Use the Sample Submission Portal to report false positives.
Select "Microsoft Defender for Storage" as the source when submitting.
Suppress alerts
- Create suppression rules in Defender for Cloud to prevent specific recurring false positive alerts.
Address undetected malware (false negatives)
False negatives occur when the system fails to detect a malicious file. If you suspect this happened, you can report the undetected malware by submitting the file for analysis through the Sample Submission Portal. Be sure to include as much context as possible to explain why you believe the file is malicious.
Note
Regularly reporting false positives and negatives helps improve the accuracy of the malware detection system over time.