Install ATA - Step 8
Applies to: Advanced Threat Analytics version 1.9
Step 8: Configure IP address exclusions and Honeytoken user
ATA enables the exclusion of specific IP addresses or users from a number of detections.
For example, a DNS Reconnaissance exclusion could be a security scanner that uses DNS as a scanning mechanism. The exclusion helps ATA ignore such scanners. An example of a Pass-the-Ticket exclusion is a NAT device.
ATA also enables the configuration of a Honeytoken user, which is used as a trap for malicious actors - any authentication associated with this (normally dormant) account triggers an alert.
To configure this, follow these steps:
From the ATA Console, click on the settings icon and select Configuration.
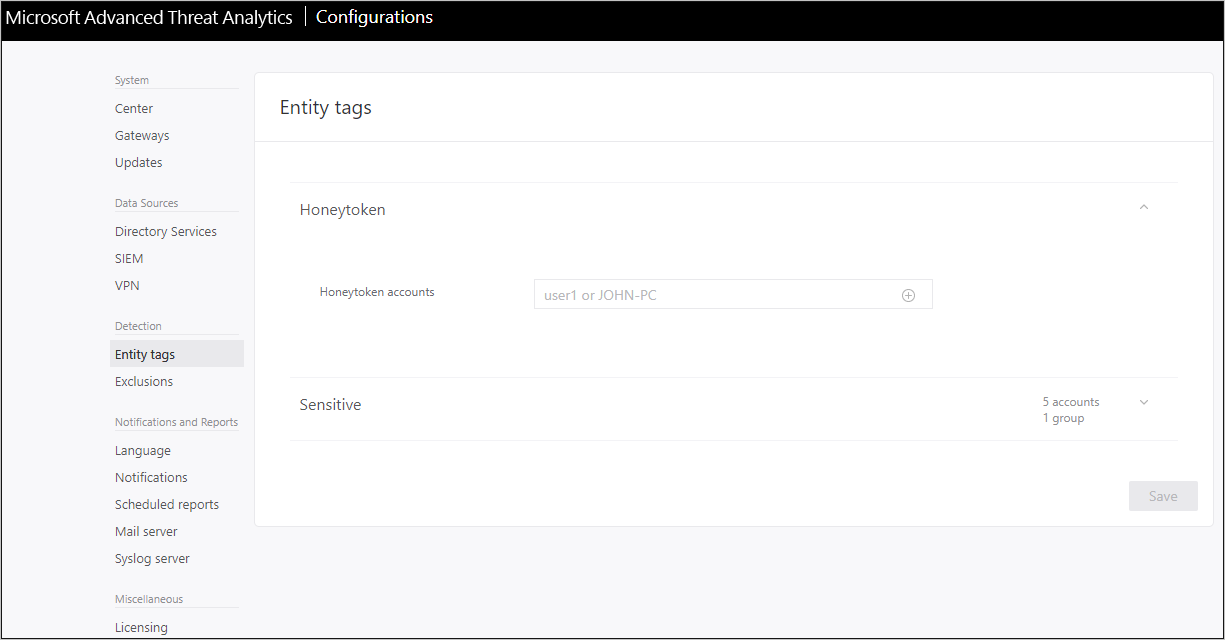
Under Detection, click Entity tags.
Under Honeytoken accounts enter the Honeytoken account name. The Honeytoken accounts field is searchable and automatically displays entities in your network.
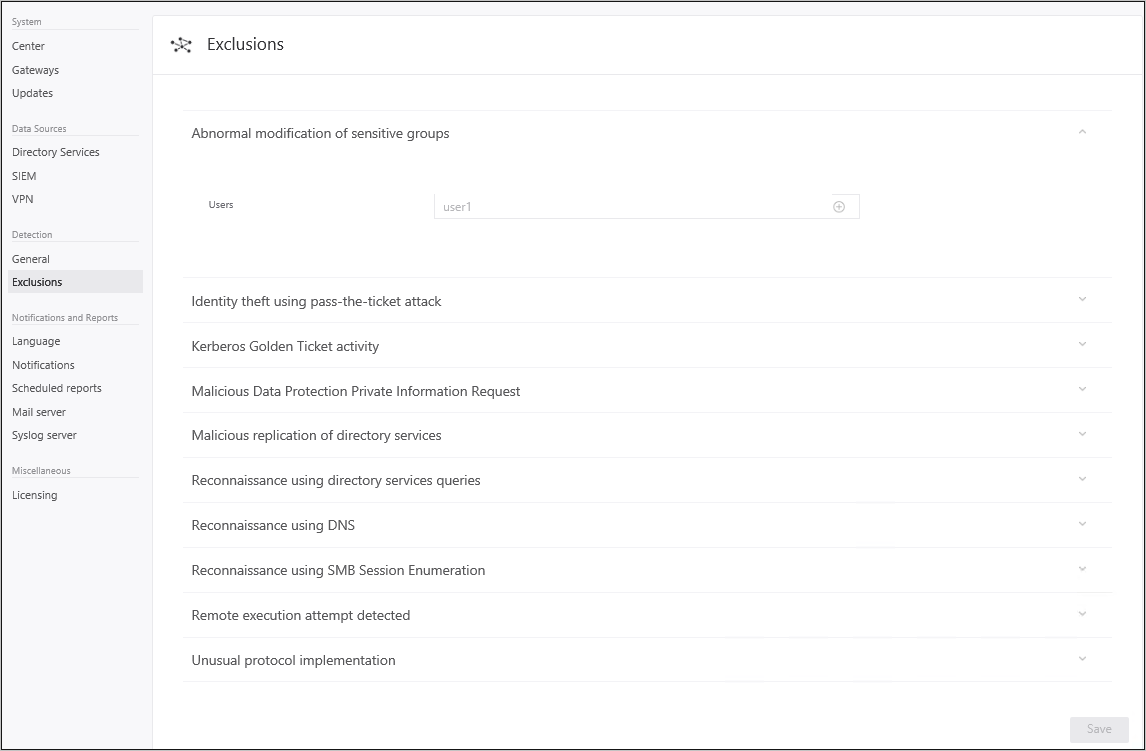
Click Exclusions. For each type of threat, enter a user account or IP address to be excluded from the detection of these threats and click the plus sign. The Add entity (user or computer) field is searchable and will autofill with entities in your network. For more information, see Excluding entities from detections
Click Save.
Congratulations, you have successfully deployed Microsoft Advanced Threat Analytics!
Check the attack time line to view detected suspicious activities and search for users or computers and view their profiles.
ATA starts scanning for suspicious activities immediately. Some activities, such as some of the suspicious behavior activities, is not available until ATA has had time to build behavioral profiles (minimum of three weeks).
To check that ATA is up and running and catching breaches in your network, you can check out the ATA attack simulation playbook.