@Alvin Leung
Thank you for your post!
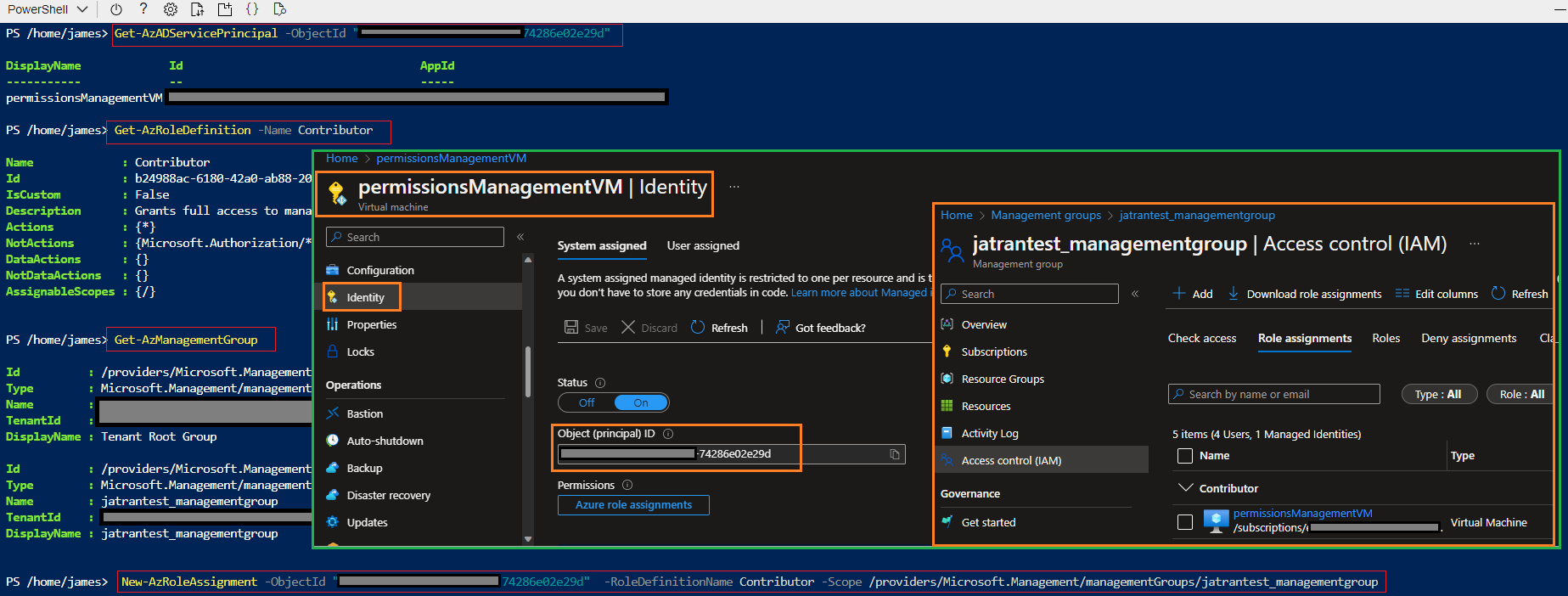
When it comes to assigning a system-managed identity at the Management Group scope, you should be able to reference our Assign Azure roles using Azure PowerShell documentation to accomplish this.
To assign roles, you must have:
-
Microsoft.Authorization/roleAssignments/write permissions, such as User Access Administrator or Owner. - PowerShell in Azure Cloud Shell or Azure PowerShell.
- The account you use to run the PowerShell command must have the Azure Active Directory Graph
Directory.Read.Alland Microsoft GraphDirectory.Read.Allpermissions. -
Microsoft.Authorization/roleAssignments/write permissions, such as User Access Administrator or Owner.
#Get the system-managed identity Object (principal) ID
#You can also find the Object ID by navigating to the resource with the system-assigned identity (i.e. VM).
Get-AzADServicePrincipal -ObjectId <String>
#Select the appropriate role - List the details of a particular role.
Get-AzRoleDefinition -Name <roleName>
#Identify the needed scope - Management group scope
Get-AzManagementGroup
#Assign role
New-AzRoleAssignment -ObjectId <String> -RoleDefinitionName <roleName> -Scope /providers/Microsoft.Management/managementGroups/<groupName>
Additional Links:
Assign a role for a user at a management group scope - Example
Get-AzADServicePrincipal
New-AzRoleAssignment
Scope examples
Scope and ARM templates
I hope this helps!
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.

