Hello @bcb44 thank you for asking very good questions :).
Going directly to your main question "Is it possible to implement it without needing the workload cert? Or ideally to not even need the edgeHub cert and only have one certificate on the device?" the short answer is no. Nevertheless Microsoft maintains the main code base for the IoT Edge security daemon on GitHub and you are free to customize the code for your scenario. But let me first try to bring some clarity on why you need a (1) workload CA, a (2) Device CA and a (3) Root CA certificates even when being the "operator" and the "manufacturer" of the device.

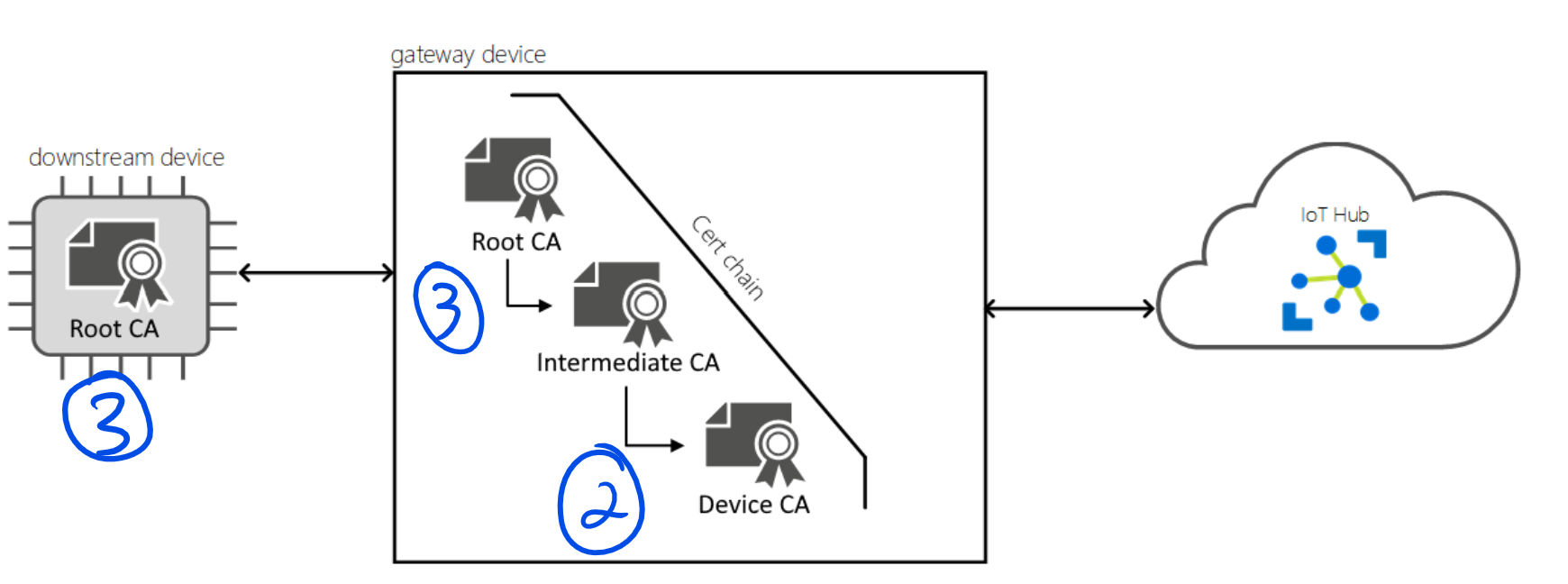
- The workload CA is generated by the IoT Edge security manager when IoT Edge first starts - you don't need to care about having it on your private PKI. Leaf devices do not need to know anything about the workload CA as the chain goes all back to the Root CA used to sign the Device CA (stored securily in your iot edge gateway). As for the modules deployed by the iot edge, they will access the Workload API that provides proof of identity and the corresponding trust bundle to a module - you also don't need to worry about having the module's certificates in your private PKI as all is managed by the IoT Edge security manager.
- The Device CA needs to be secured in your IoT Edge Gateway, preferably in secure storage such as a hardware security module (HSM) because it contains a private key. If you want to leverage it, your PKI should be able to move the Device CA file to the IoT Edge Gateway.
- The server certificate chain that comprises your root certificate authority (CA) certificate and the intermediate CA certificate need also to be deployed on your IoT Edge Gateway. The only CA
*that your leaf device needs to have is the Root CA used to generate the Device CA in the gateway - Your downstream device uses this certificate to validate the identity of the gateway device.
* If you want your Leaf Device to connect to IoTHub (authenticated with X509) when iot edge is acting as a transparent gateway, then your leaf device needs also to access the X509 Leaf Device cert generated by the same Root CA of your IoT Edge Gateway Device CA.
Please understand that all we are trying to achieve is that we have a client validation of the server certificate chain, also called server chain validation, where the IoT Edge Gateway is the server and the leaf device or modules are the clients. That is needed to enable a TLS (transport layer security) secure connection between the runtime, the modules, and the IoT devices. To maintain reasonable security, the downstream device should confirm the identity of the gateway device. This identity check prevents your devices from connecting to potentially malicious gateways. See as well TLS and certificate fundamentals
Hope I could help and thanks @Alberto Gorni for bringing the very relevant docs on your comment as well.
Remember:
- Please accept an answer if correct. Original posters help the community find answers faster by identifying the correct answer. Here is how.
- Want a reminder to come back and check responses? Here is how to subscribe to a notification.
