Followed “Setting up a Source Initiated Subscription”( Setting up a Source Initiated Subscription - Win32 apps | Microsoft Learn), “Creating a Source Initiated Subscription”( Creating a Source Initiated Subscription - Win32 apps | Microsoft Learn) and “Spotting the Adversary with Windows Event Log Monitoring”( Spotting the Adversary with Windows Event Log Monitoring (nsa.gov))
Collector: Windows Server 2016 1607 Standard
Source: Windows 10 1809
Environment: Active Directory
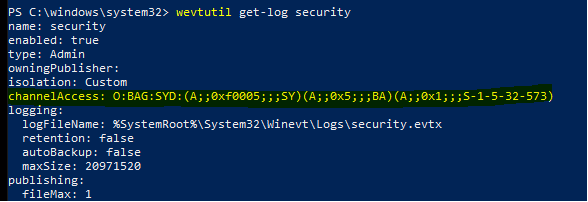
Appended (A;;0x1;;;S-1-5-20) to Application and System logs and (A;;0x1;;;NS)(A;;0x1;;;S-1-5-20) to Security log
Collected events are forward to third-party application for analysis. Vendor requested all events in Application, Security and System logs be forwarded.
Eventlog-ForwardingPlugin/Operational
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-Forwarding" Guid="{699e309c-e782-4400-98c8-e21d162d7b7b}" />
<EventID>105</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x8000000000000000</Keywords>
<TimeCreated SystemTime="2020-12-15T15:56:39.653090300Z" />
<EventRecordID>2764</EventRecordID>
<Correlation ActivityID="{a4919054-d2f0-0004-f890-91a4f0d2d601}" />
<Execution ProcessID="5872" ThreadID="620" />
<Channel>Microsoft-Windows-Forwarding/Operational</Channel>
<Computer>SOURCE</Computer>
<Security UserID="S-1-5-20" />
</System>
- <EventData Name="SubscriptionManagerStatus">
<Data Name="SubscriptionManagerAddress">http://collector/wsman/SubscriptionManager/WEC</Data>
<Data Name="ErrorCode">5</Data>
<Data Name="ErrorMessage"><f:WSManFault xmlns:f="http://schemas.microsoft.com/wbem/wsman/1/wsmanfault" Code="5" Machine="SOURCE"><f:Message>Access is denied. </f:Message></f:WSManFault></Data>
</EventData>
</Event>
Windows Remote Management\Operational
User authentication
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-WinRM" Guid="{a7975c8f-ac13-49f1-87da-5a984a4ab417}" />
<EventID>162</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>7</Task>
<Opcode>0</Opcode>
<Keywords>0x400000000000000a</Keywords>
<TimeCreated SystemTime="2020-12-15T17:34:17.343906000Z" />
<EventRecordID>63155</EventRecordID>
<Correlation ActivityID="{a4919054-d2f0-0003-15db-91a4f0d2d601}" />
<Execution ProcessID="5872" ThreadID="15732" />
<Channel>Microsoft-Windows-WinRM/Operational</Channel>
<Computer>SOURCE</Computer>
<Security UserID="S-1-5-20" />
</System>
<EventData />
</Event>
Response handling
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-WinRM" Guid="{a7975c8f-ac13-49f1-87da-5a984a4ab417}" />
<EventID>142</EventID>
<Version>0</Version>
<Level>2</Level>
<Task>10</Task>
<Opcode>2</Opcode>
<Keywords>0x4000000000000002</Keywords>
<TimeCreated SystemTime="2020-12-15T17:34:17.344070800Z" />
<EventRecordID>63156</EventRecordID>
<Correlation ActivityID="{a4919054-d2f0-0004-f890-91a4f0d2d601}" />
<Execution ProcessID="5872" ThreadID="15732" />
<Channel>Microsoft-Windows-WinRM/Operational</Channel>
<Computer>SOURCE</Computer>
<Security UserID="S-1-5-20" />
</System>
- <EventData>
<Data Name="operationName">Enumeration</Data>
<Data Name="errorCode">5</Data>
</EventData>
</Event>
Subscription Configuration
Subscription Id: LogRythem-SM004
SubscriptionType: SourceInitiated
Description:
Enabled: true
Uri: http://schemas.microsoft.com/wbem/wsman/1/windows/EventLog
ConfigurationMode: MinLatency
DeliveryMode: Push
DeliveryMaxLatencyTime: 30000
HeartbeatInterval: 3600000
Query: <QueryList><Query Id="0"><Select Path="Application">[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]]</Select><Select Path="Security">[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]]</Select><Select Path="System">*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]]</Select></Query></QueryList>
ReadExistingEvents: false
TransportName: HTTP
ContentFormat: RenderedText
Locale: en-US
LogFile: ForwardedEvents
PublisherName: Microsoft-Windows-EventCollector
AllowedIssuerCAList:
AllowedSubjectList:
DeniedSubjectList:
AllowedSourceDomainComputers: O:NSG:BAD:P(A;;GA;;;S-1-5-21-3697291689-1161744426-439199626-114941)(A;;GA;;;S-1-5-21-3697291689-1161744426-439199626-347877)S:
From Collector to Source
winrm id -r:<source computer>
IdentifyResponse
ProtocolVersion = http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd
ProductVendor = Microsoft Corporation
ProductVersion = OS: 10.0.17763 SP: 0.0 Stack: 3.0
SecurityProfiles
SecurityProfileName = http://schemas.dmtf.org/wbem/wsman/1/wsman/secprofile/http/spnego-kerberos
From Source to Collector
winrm id r:<collector computer>
IdentifyResponse
ProtocolVersion = http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd
ProductVendor = Microsoft Corporation
ProductVersion = OS: 10.0.14393 SP: 0.0 Stack: 3.0
SecurityProfiles
SecurityProfileName = http://schemas.dmtf.org/wbem/wsman/1/wsman/secprofile/http/spnego-kerberos
wecutil gr LogRythem-SM004
Subscription: LogRythem-SM004
Failed to get RunTimeStatusActive property. Error = 0x2.
The system cannot find the file specified.
If additional information is need please let me know
Thanks