Hello all,
This is an old thread but is exactly what I am looking for and a person with clear knowledge of what is required replied, so I think it is relevant to resume on this thread.
Question: Has any progress been made on this? A real world example:
I'm the "everything" administrator on my company but my day-to-day account is not a GA just to be on the safe side. I do have a separate very well protected Global Admin account which I use for administrative tasks.
Today there was a suspicion authentication attempt and I wanted to very quickly disable the possibly compromised account since I contacted all the actors and it wasn't any of us.
Quickly went to admin.microsoft.com and of course since my account is not an admin (just a viewer), whenever I would click "block logins" it would just reply that I don't have permission. Took me a few moments to realize that this account was not authorized for that.
All of this while I am on a crowded bus and with very spotty connectivity.
So, the next step is to open a new InPrivate browser window on the phone, login with the new account, had to retry more than once because of bad signal, then trying to get the FIDO key work on my cell (NFC didn't work, USB was glitchy).... All in all, took me like 5 minutes to be able to login with this GA account (blushing-emoticon-here) in order to be able to disable the suspicious account while I got to the office to check what was going on (false alarm it was some Microsoft service trying to login after I had invalidated all 2-factor sessions, or something along those lines).
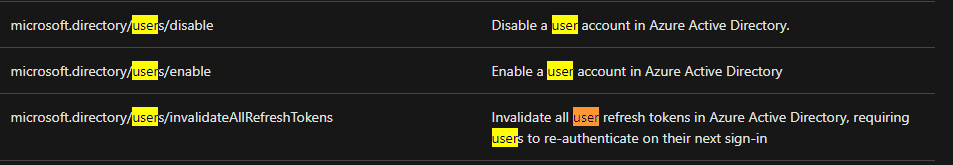
I would really like to give a permission to just "lock out" someone else to some regular accounts / trusted people. Not change passwords, groups or privileges. Simply block. That way if the admin is not able to notice, or act upon some security situation, someone else can quickly take [preemptive] action before the whole thing escalates.
A quick reaction during a suspected infiltration is key, before they create secondary accounts, assign privileges or perform some other activities that compromise the whole tenant.
So, any progress on this? Having it would really improve security across the AAD-verse.