Hi @AdamTyler-3751 ,
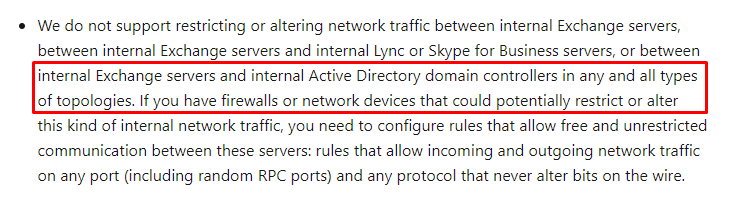
Its really about support versus what works. You can certainly block those remote DCs with firewall rules and set the Exchange Servers to only use local DCs:
(Exluding the remote DCs)
-StaticExcludedDomainControllers
https://learn.microsoft.com/en-us/powershell/module/exchange/set-exchangeserver?view=exchange-ps
set-exchangeServer <ex01> -StaticExcludedDomainControllers <RemoteDC1>, <RemoteDC2>
If that works and Exchange is fine, do that. If you find it doesn't work , undo it.
The support issue comes if you open a ticket and then support determines the issue is because Exch is trying to contact a Remote DC , then they will tell you what you are doing is not suported. :)