
Hello @czql5v ,
Thank you so much for posting here.
We could follow the below steps to track and audit changes made to Group Policy Objects:
Step 1: Enable Audit
- Launch “Group Policy Management Console”, create a new GPO and link to Domain Controllers OU.
- From the context menu, click on “Edit” to open the “Group Policy Management Editor” window.
Navigate to “Computer Configuration” -> “Policies” -> “Windows Settings” -> “Security Settings” -> “Advanced Audit Policy Configuration” -> “Audit Policies” -> “DS Access”. - Click “Audit Directory Service changes”, click “Configure the following audit events” and choose “Success”.
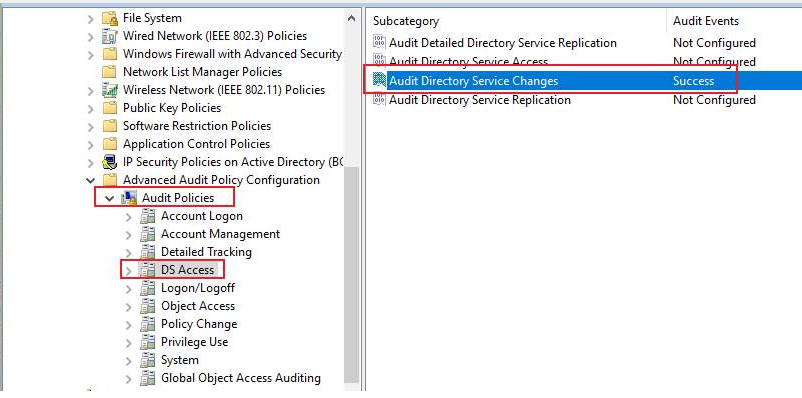
- To force Group Policy Update, we could run “gpupdate /force” on the domain controllers.
Step 2: Configuring Group Policy Container Objects auditing
- Launch the ADSIEdit.msc and Connect to the Default naming context.
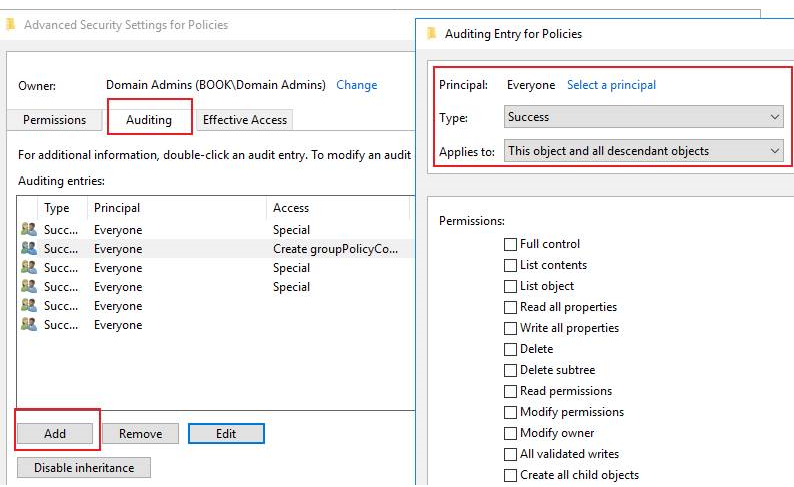
- Navigate to CN=Policies,CN=System,DC=domain -> Open the “Properties of Policies” object -> Go to the Security tab -> Click the Advanced button.
- Go to the Auditing tab -> Add the Principal Everyone -> Choose the Type Success -> For Applies to, click This object and Descendant objects -> Under Permissions, select following checkboxes: “Create groupPolicyContainer objects”, “Delete”, “Modify Permissions” -> Click OK.
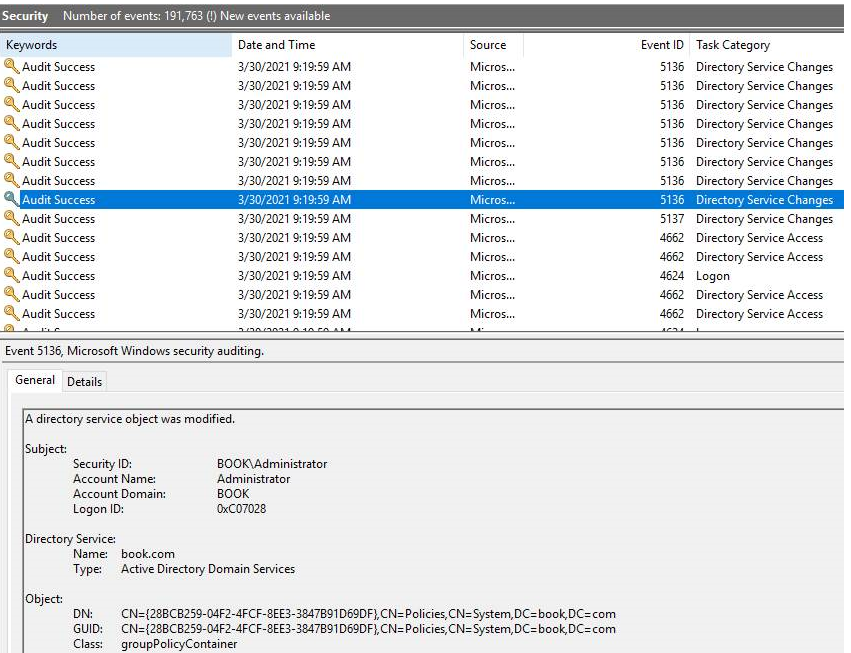
Step 3: Review changes in the security Event Log
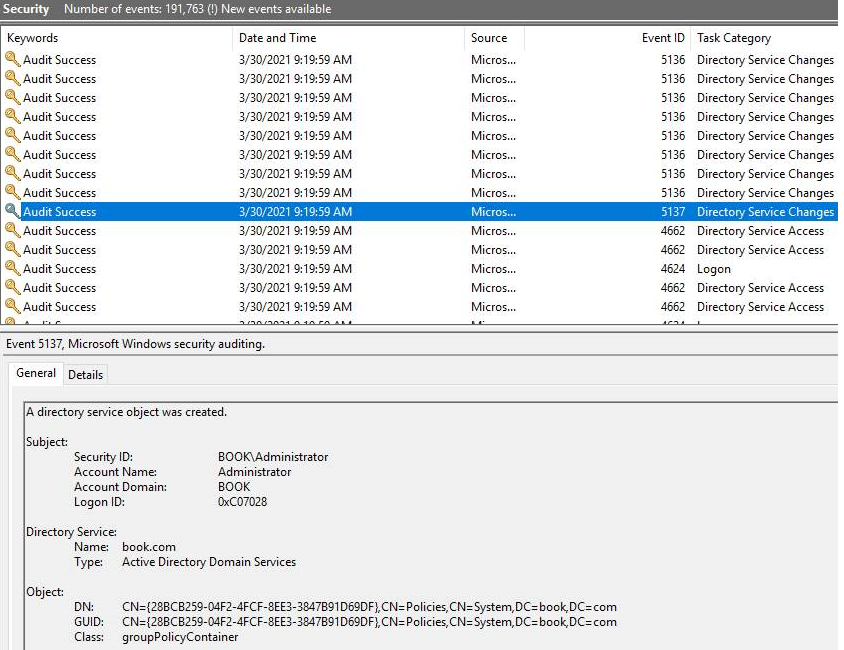
- When a Group Policy object is created. Event ID 5137 is logged containing details of who created the Group Policy object and the fact an object was created.
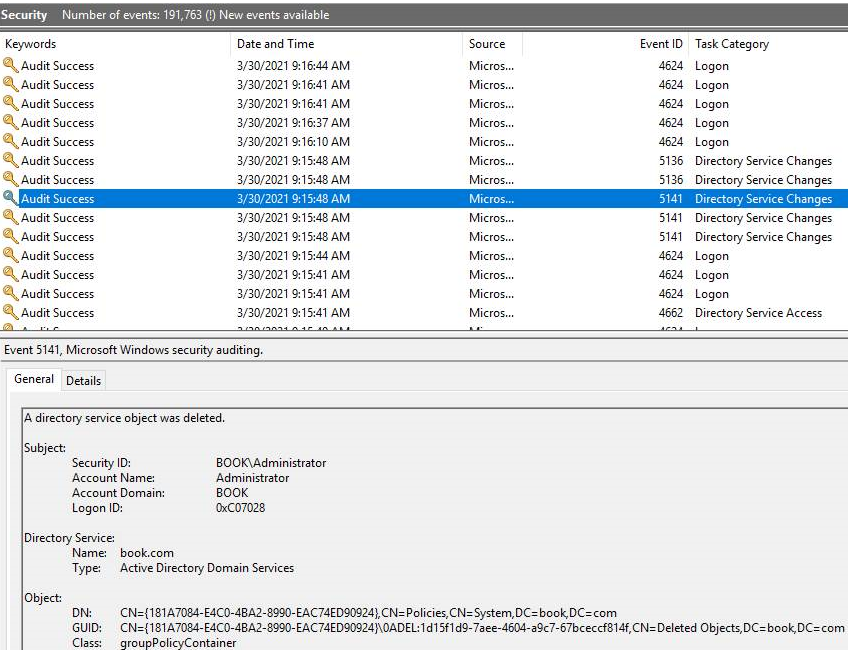
- When a GPO is deleted, an Event ID 5141 is logged with the Unique ID of the GPO that was deleted and the user who performed the deletion.
- When a GPO is modified, an Event ID 5136 is logged.
Best regards,
Hannah Xiong