Hi Doc-4663
Ok so I have done the following :
1.Decrypted the drive on 2 machines
2.Removed all McAfee product's using their product removal tool , which has removed the antivirus and firewall as well as the agent.
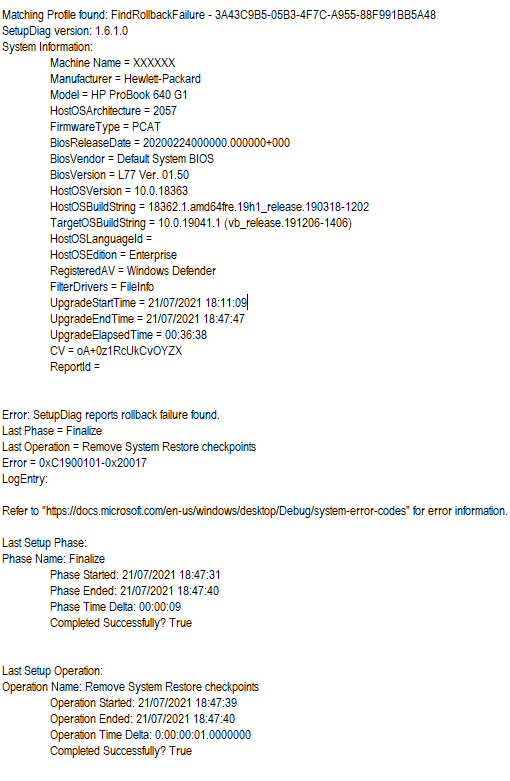
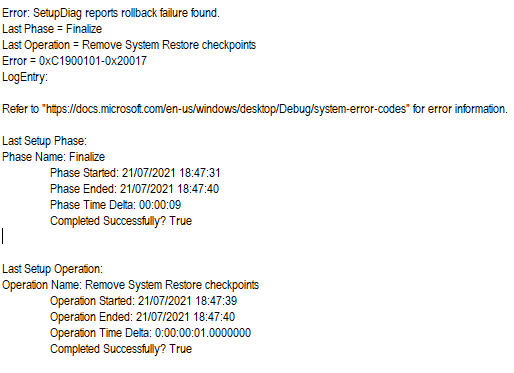
With regards to this error : 0xC1900101-20017 , I have updated all the drivers in the device manager , if I may ask what is the best way to identify the driver causing the issue other then the steps I've taken in my first post ?
3.I have run through all your troubleshooting steps 1-12 , the logs are below.
XX-170390 - 1st Machine
Microsoft Windows [Version 10.0.17763.1935]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\windows\system32>sfc/scannow
Beginning system scan. This process will take some time.
Beginning verification phase of system scan.
Verification 100% complete.
Windows Resource Protection found corrupt files and successfully repaired them.
For online repairs, details are included in the CBS log file located at
windir\Logs\CBS\CBS.log. For example C:\Windows\Logs\CBS\CBS.log. For offline
repairs, details are included in the log file provided by the /OFFLOGFILE flag.
C:\windows\system32>dism /online /cleanup-image /scanhealth
Deployment Image Servicing and Management tool
Version: 10.0.17763.1697
Image Version: 10.0.17763.1935
[==========================100.0%==========================] No component store corruption detected.
The operation completed successfully.
C:\windows\system32>dism /online /cleanup-image /restorehealth
Deployment Image Servicing and Management tool
Version: 10.0.17763.1697
Image Version: 10.0.17763.1935
[==========================100.0%==========================] The restore operation completed successfully.
The operation completed successfully.
C:\windows\system32>sfc/scannow
Beginning system scan. This process will take some time.
Beginning verification phase of system scan.
Verification 100% complete.
Windows Resource Protection did not find any integrity violations.
C:\windows\system32>chkdsk /scan
The type of the file system is NTFS.
Volume label is Windows.
Stage 1: Examining basic file system structure ...
1029888 file records processed.
File verification completed.
20888 large file records processed.
0 bad file records processed.
Stage 2: Examining file name linkage ...
197 reparse records processed.
1208676 index entries processed.
Index verification completed.
0 unindexed files scanned.
0 unindexed files recovered to lost and found.
197 reparse records processed.
Stage 3: Examining security descriptors ...
Security descriptor verification completed.
89395 data files processed.
CHKDSK is verifying Usn Journal...
38956232 USN bytes processed.
Usn Journal verification completed.
Windows has scanned the file system and found no problems.
No further action is required.
226326527 KB total disk space.
51966368 KB in 402147 files.
278024 KB in 89396 indexes.
0 KB in bad sectors.
1149707 KB in use by the system.
65536 KB occupied by the log file.
172932428 KB available on disk.
4096 bytes in each allocation unit.
56581631 total allocation units on disk.
43233107 allocation units available on disk.
C:\windows\system32>wmic recoveros set autoreboot = false
Updating property(s) of '\XX-170390\ROOT\CIMV2:Win32_OSRecoveryConfiguration.Name="Microsoft Windows 10 Enterprise|C:\windows|\Device\Harddisk0\Partition2"'
Property(s) update successful.
C:\windows\system32>wmic recoveros set DebugInfoType = 7
Updating property(s) of '\XX-170390\ROOT\CIMV2:Win32_OSRecoveryConfiguration.Name="Microsoft Windows 10 Enterprise|C:\windows|\Device\Harddisk0\Partition2"'
Property(s) update successful.
C:\windows\system32>wmic recoveros get autoreboot
AutoReboot
FALSE
C:\windows\system32>wmic recoveros get DebugInfoType
DebugInfoType
7
C:\windows\system32>wmic Computersystem where name="%computername%" set AutomaticManagedPagefile=^Z
C:\windows\system32>wmic Computersystem where name="XX-170390" set AutomaticManagedPagefile=True
Updating property(s) of '\XX-170390\ROOT\CIMV2:Win32_ComputerSystem.Name="XX-170390"'
Property(s) update successful.
C:\windows\system32>wmic Computersystem where name="XX-170390" get AutomaticManagedPagefile
AutomaticManagedPagefile
TRUE
C:\windows\system32>bcdedit /enum {badmemory}
RAM Defects
identifier {badmemory}
C:\windows\system32>
XX-180807X - 2nd Machine
Microsoft Windows [Version 10.0.17763.1935]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\windows\system32>sfc /scannow
Beginning system scan. This process will take some time.
Beginning verification phase of system scan.
Verification 100% complete.
Windows Resource Protection found corrupt files and successfully repaired them.
For online repairs, details are included in the CBS log file located at
windir\Logs\CBS\CBS.log. For example C:\Windows\Logs\CBS\CBS.log. For offline
repairs, details are included in the log file provided by the /OFFLOGFILE flag.
C:\windows\system32>dism /online /cleanup-image /scanhealth
Deployment Image Servicing and Management tool
Version: 10.0.17763.1697
Image Version: 10.0.17763.1935
[==========================100.0%==========================] No component store corruption detected.
The operation completed successfully.
C:\windows\system32>dism /online /cleanup-image /restorehealth
Deployment Image Servicing and Management tool
Version: 10.0.17763.1697
Image Version: 10.0.17763.1935
[==========================100.0%==========================] The restore operation completed successfully.
The operation completed successfully.
C:\windows\system32>sfc /scannow
Beginning system scan. This process will take some time.
Beginning verification phase of system scan.
Verification 100% complete.
Windows Resource Protection did not find any integrity violations.
C:\windows\system32>chkdsk /scan
The type of the file system is NTFS.
Volume label is Windows.
Stage 1: Examining basic file system structure ...
826880 file records processed.
File verification completed.
27436 large file records processed.
0 bad file records processed.
Stage 2: Examining file name linkage ...
476 reparse records processed.
1038116 index entries processed.
Index verification completed.
0 unindexed files scanned.
0 unindexed files recovered to lost and found.
476 reparse records processed.
Stage 3: Examining security descriptors ...
Security descriptor verification completed.
105619 data files processed.
CHKDSK is verifying Usn Journal...
37172008 USN bytes processed.
Usn Journal verification completed.
Windows has scanned the file system and found no problems.
No further action is required.
231577599 KB total disk space.
63700524 KB in 364104 files.
267312 KB in 105620 indexes.
0 KB in bad sectors.
949195 KB in use by the system.
65536 KB occupied by the log file.
166660568 KB available on disk.
4096 bytes in each allocation unit.
57894399 total allocation units on disk.
41665142 allocation units available on disk.
C:\windows\system32>wmic recoveros set autoreboot = false
Updating property(s) of '\XX-180807X\ROOT\CIMV2:Win32_OSRecoveryConfiguration.Name="Microsoft Windows 10 Enterprise|C:\windows|\Device\Harddisk0\Partition2"'
Property(s) update successful.
C:\windows\system32>wmic recoveros set DebugInfoType = 7
Updating property(s) of '\XX-180807X\ROOT\CIMV2:Win32_OSRecoveryConfiguration.Name="Microsoft Windows 10 Enterprise|C:\windows|\Device\Harddisk0\Partition2"'
Property(s) update successful.
C:\windows\system32>wmic recoveros get autoreboot
AutoReboot
FALSE
C:\windows\system32>wmic recoveros get DebugInfoType
DebugInfoType
7
C:\windows\system32>wmic Computersystem where name="XX-180807X" set AutomaticManagedPagefile=True
Updating property(s) of '\XX-180807X\ROOT\CIMV2:Win32_ComputerSystem.Name="XX-180807X"'
Property(s) update successful.
C:\windows\system32>wmic Computersystem where name="XX-180807X" get AutomaticManagedPagefile
AutomaticManagedPagefile
TRUE
C:\windows\system32>bcdedit /enum {badmemory}
RAM Defects
identifier {badmemory}
C:\windows\system32>
I'm currently redeploying the 2004 ISO now to these 2 machines , and will update you further on my progress.
Thank - you