Hi,
I would like to confirm that the steps I have taken in this case have worked, at least in my case. After being unable to find a suitable solution on various forums and sites, I've spend 3 days troubleshooting only to accidentally find the solution.
Error:
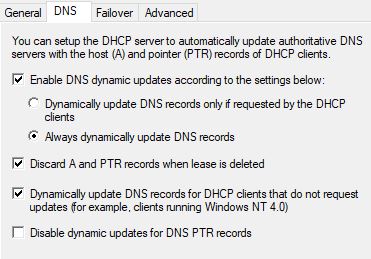
- Forward record registration for IPv4 address [[192.168.0.69]] and FQDN machinename.domain.local failed with error 9005 (DNS operation refused.).
- PTR record registration for IPv4 address [[192.168.0.69]] and FQDN machinename.domain.local failed with error 9005 (DNS operation refused.).
Solution:
- In DNS Manager, got to properties of the zone you are going to delete, note all settings for the zone, delete the zone in Reverse Lookup Zones which shows errors:
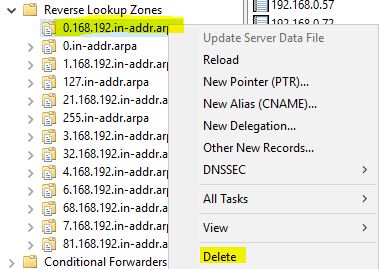
- Depending on the size of your infrastructure/how many DCs you have, let this change propagate to all DCs.
- Recreate the deleted zone with the values you noted before deletion.
- Check event viewer log under Application and services->Microsoft->Windows->DHCP-Server->Microsoft-Windows-DHCP Server Events/Admin There should be no more errors.
If you want to know more:
Upon further investigation, I simply compared the "security" Tab of the zone which didn't had any problems with the problematic one, and the difference was that the problematic zone did not have "DnsAdmins" Group. In my DnsAdmins Group there is currently only a service account which is used for dns dynamic updates (https://www.serverbrain.org/network-infrastructure-2003/using-dns-dynamic-update-credentials.html). At first, I tried to solve the problem without deleting a zone, and this also worked (not 100% sure). I added ALL the rights and "subrights" to the "DnsAdmins" group:
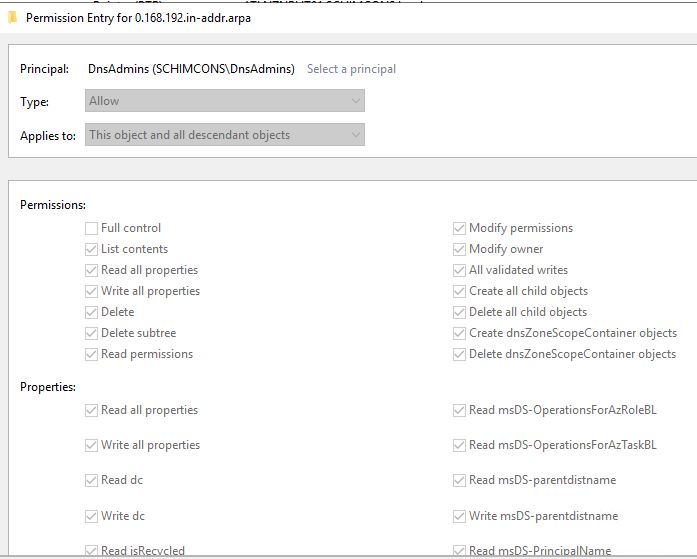
So everything must be enabled except "full control".
Cheers