Consider using a Cond Access Policy to block uses to the Azure portal - excluding users who need access to the apps they own.
https://osddeployment.dk/2017/06/24/a-standard-azuread-user-have-access-to-browse-the-admin-portal/
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
We have recently restricted access to the Azure AD admin portal for none-admins.
App owners are now greeted by the following message: "Your administrator has disabled the App registrations experience in the Azure portal. You can still register or manage applications using PowerShell or another client such as Visual Studio."
How do we let owners manage their apps through the portal, instead of Powershell or VS, which is not the most desired solution?
I understand that they can be temporarily assigned the 'Application Administrator'-role by utilizing access reviews. However, this would let them manage all the other enterprise applications in our tenant as well, which is not applicable.
Surely there must be some other alternatives? Any ideas? Thanks!

Consider using a Cond Access Policy to block uses to the Azure portal - excluding users who need access to the apps they own.
https://osddeployment.dk/2017/06/24/a-standard-azuread-user-have-access-to-browse-the-admin-portal/

Hello @Thijs1,
As @Andy David - MVP mentioned Azure AD CA way would be helpful in this situation.
So when you choose the "Microsoft Azure Management" cloud app through Conditional Access (AAD CA) which includes multiple services, but this doesn't enable any additional control to users at resource level like creating resource groups in subscription because it is only portal entry level allow/deny access.
Azure resources access are controlled through RBAC role by default so without right RBAC role, user access would be denied. For example, I built an AAD CA policy that restricts access to all users except a few who are application owners, so that when normal users try to access Azure Portal, their access is restricted, but owners can continue to access portal.azure.com to manage their owned AAD apps.
However, if the application owner attempts to create a Resource Group or Manage resources from the Azure portal, they will receive the following error because the ARM (Azure resource manager) validates whether that particular user has RBAC role access to the given subscription; if not, they receive an error while creating any resources.
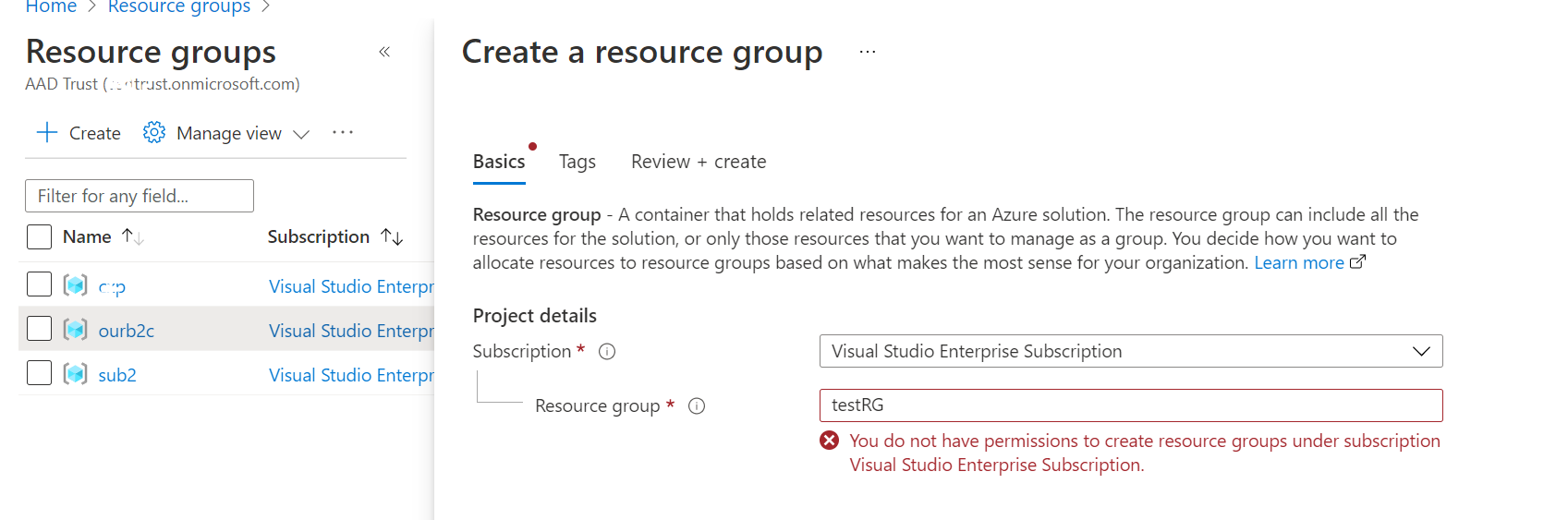
I'd request you to check if those user in your scenario has any RBAC role access at the subscription level? which could have enabled them to create a resource group. Please help me in better understanding if I have missed something. Thanks
Hope this was helpful.