Hello @jaybird283 ,
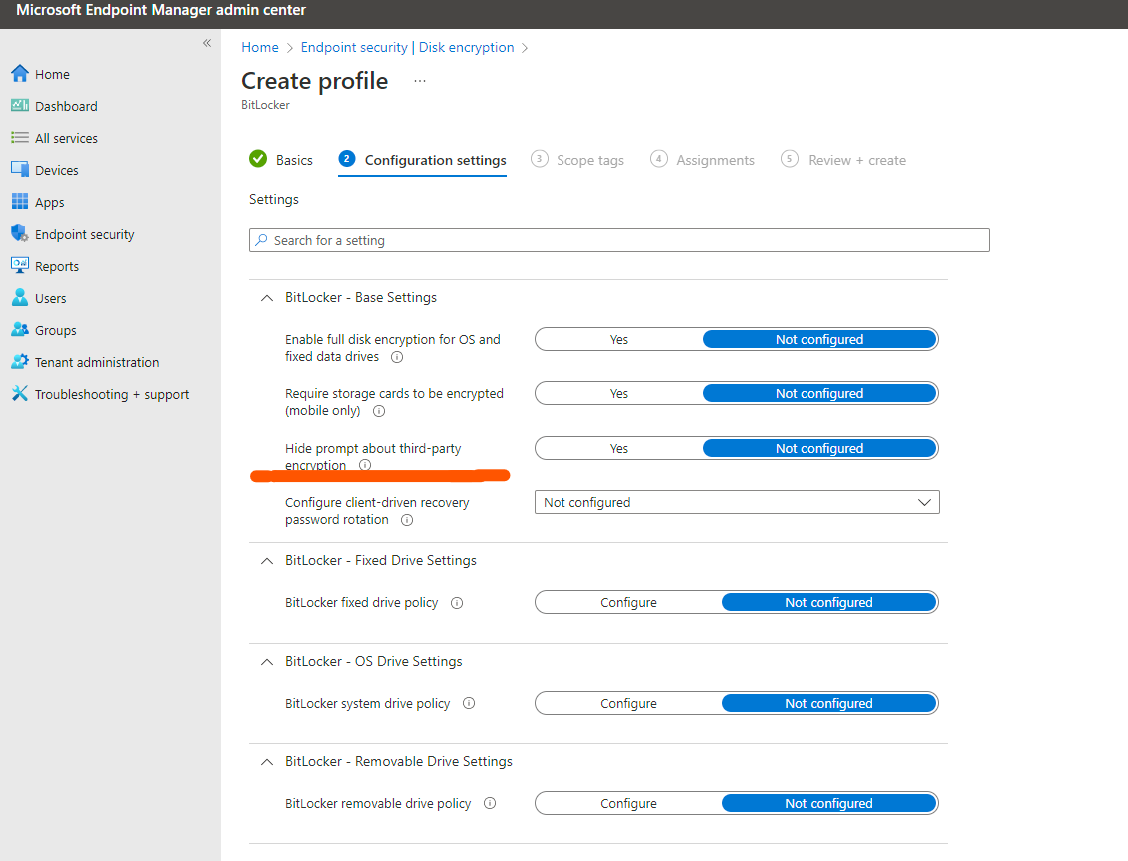
Thanks for your response. In order to scope the devices which are encrypted with 3rd party encryption via registry path you could use the following PowerShell script.
$KeyPath = "HKCU:\Registry\Key\Path"
$ValueName = "name"
$ValueData = "data"
try{
Get-ItemProperty -Path $KeyPath -Name $valueName -ErrorAction Stop
}
catch [System.Management.Automation.ItemNotFoundException] {
New-Item -Path $KeyPath -Force
New-ItemProperty -Path $KeyPath -Name $ValueName -Value $ValueData -Force
}
catch {
New-ItemProperty -Path $KeyPath -Name $ValueName -Value $ValueData -Type String -Force
}
OR
- Have a dummy win32 application deployed https://learn.microsoft.com/en-us/mem/intune/apps/apps-win32-app-management
- Have encryption software registry path script file location as a dependency:
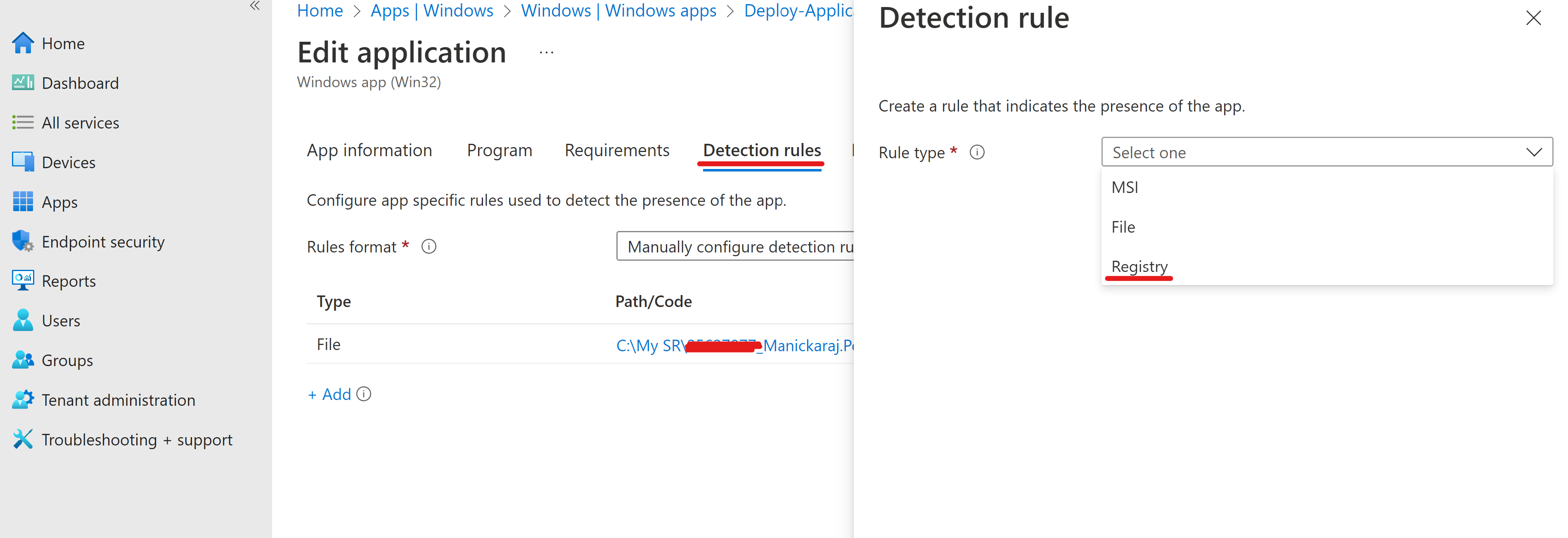
- Devices on which the detection logic is true will show successful status as the IME agent (Win32 agent) would check the registry path and give successful deployment status of the devices which have registry path for encryption software.
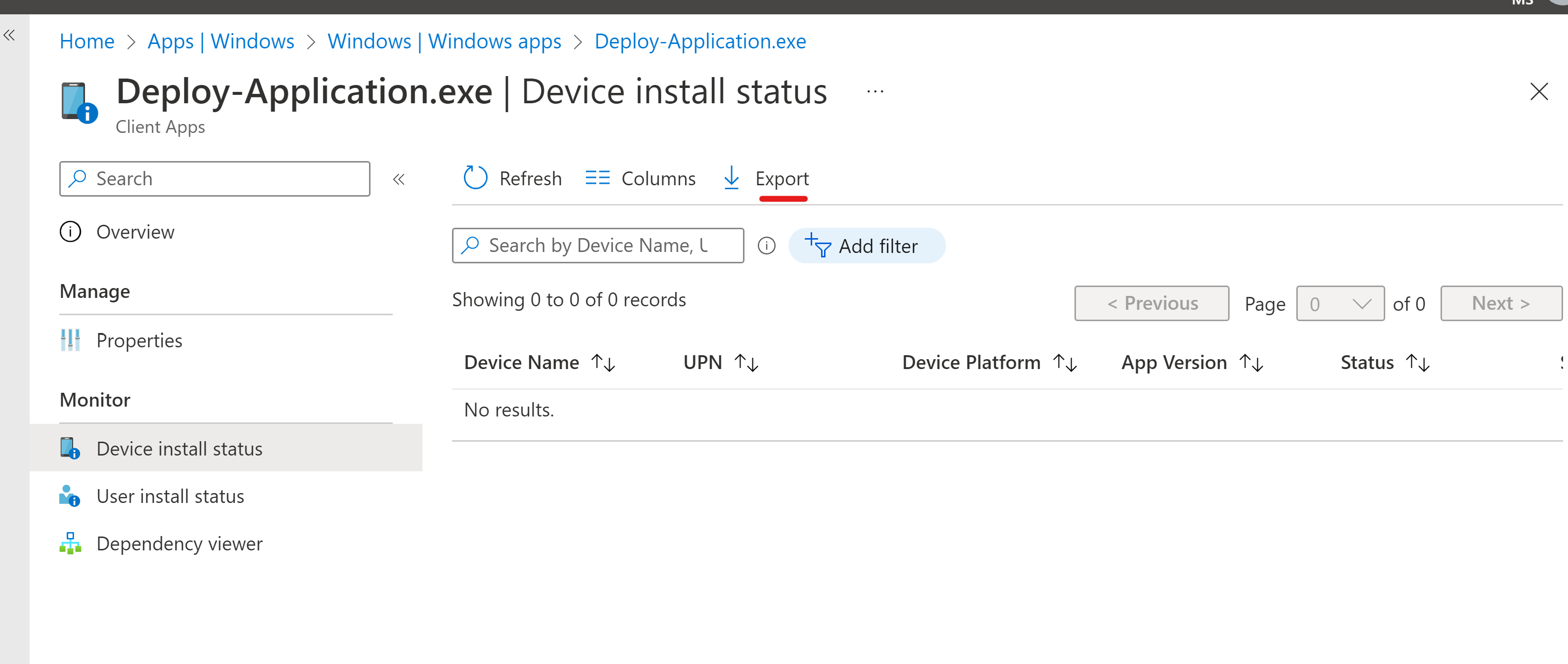
- Same could be exported and used to create a device group, which later could be excluded from encryption policy.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.