Changing the display order would explain the order in the screenshot.
You are correct this doesn't change the order in which they are applied. The permissions in the ACL are ordered based on the following rule:
Explicit Deny
Explicit Allow
Inherited Deny
Inherited Allow
The inherited permissions are also sorted based DN path, with the closest OU first, then the next OU and so on. The permissions at the top of the list take precedence over the lower permissions. You can think of it as the permissions are applied from the bottom up.
The dsacls command is correct and will assign a deny permission to the user object. I would reconsider the use of the Domain User group, as this will block all users including Domain Admins from reading the attribute, unless you change the default PrimaryGroupID for users that you want to read the attribute.
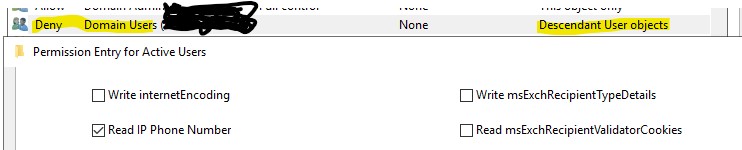
With your command the following permission will be applied, I've used the Deny-Enum group here:
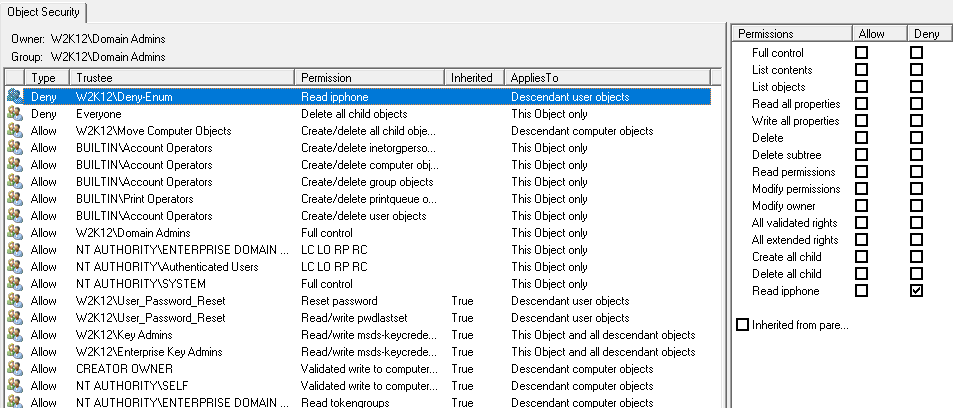
When you look at the permissions that are applied to the a user account in the OU, the user has these permissions:
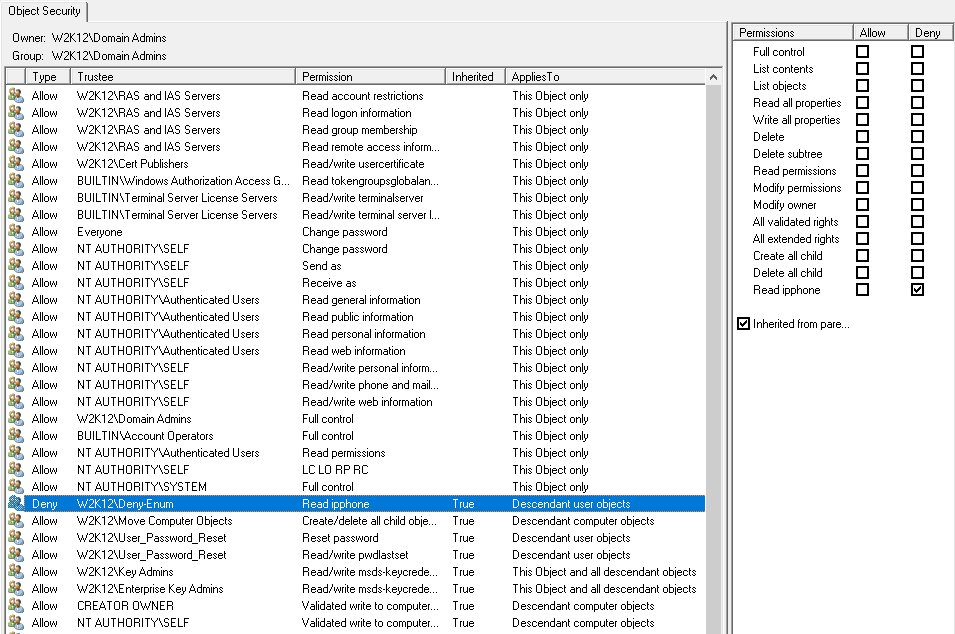
The deny permissions is shown as inherited as expected.
To understand why the deny permissions is not being applied, first we need to look the ipphone attribute and how the user is getting the permissions to read this attribute in the first place.
The ipPhone attribute is a member of a Property Set called Personal Information which includes a lot of attributes:
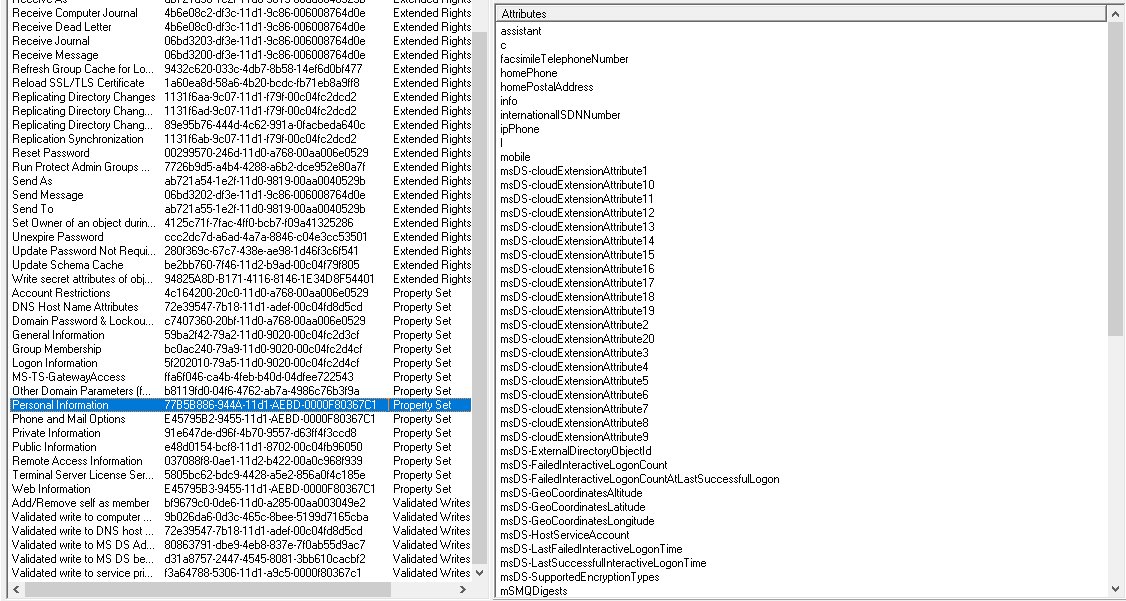
Looking at the permissions of the user the Authenticated Users has been granted read rights to the Personal Information Property set. As this permissions is an explicit permission which will take precedence over the inherited deny permission from the OU.
This Authenticated Users right is grant by the default security descriptor from the User Object in the schema.
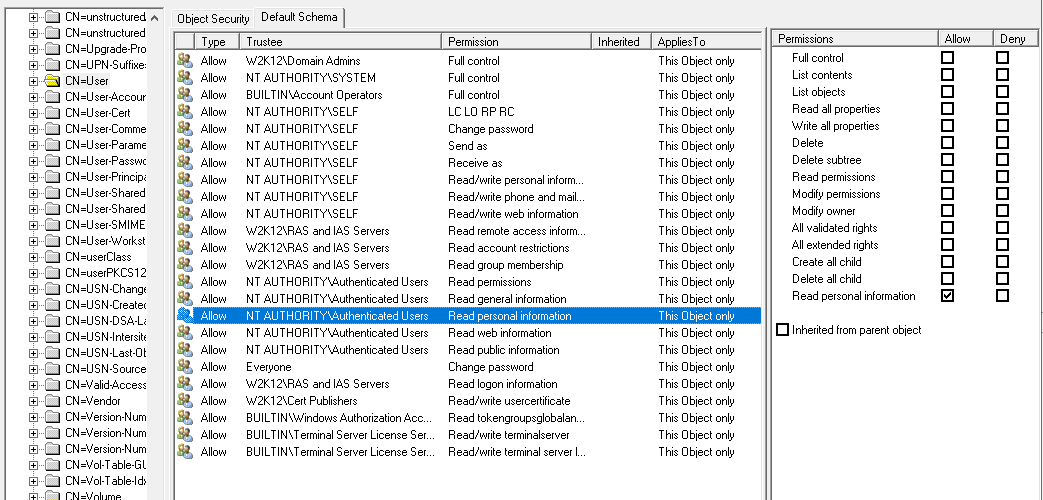
You could edit the default Security Descriptor but this could cause other issues down the track with other applications relying on this permissions.
Other option is to remove the ipPhone attribute from the Personal Information Property Set, however, like changing the default security descriptor it could cause issues later.
If you want to remove the ipPhone atttribute from the Personal Information Property Set, you just need to clear the AttributeSecurityGUID attribute from the Phone-Ip-Primary schema object.
This does work however, there is a sneaky permission that will still provide access the attribute via the Pre-Windows 2000 Compatible Access permissions, removing this does cause a lot of the attribute to inaccessible, so may cause other problems as well.
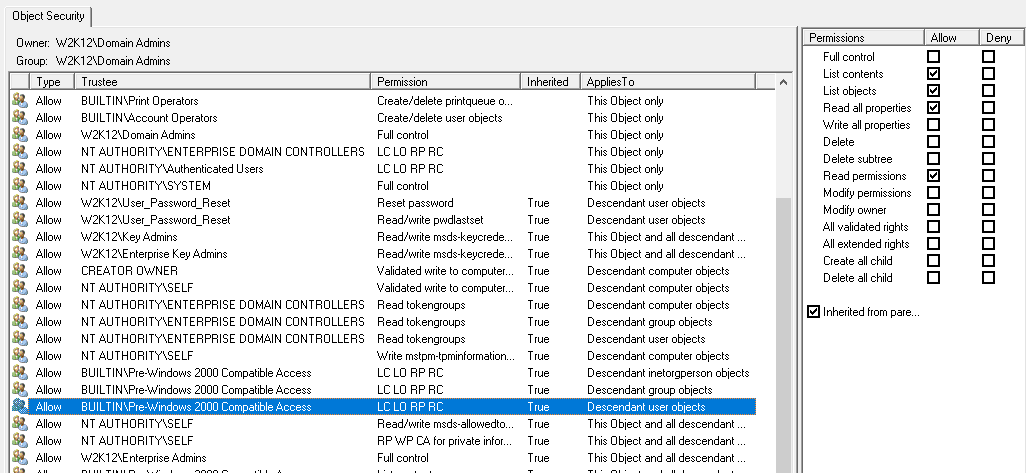
Probably best to get MS to provide their advice on how to deny access with the minimal downstream impacts. The simplest option might be to assign an explicit deny permission to the default security descriptor of the user object in the schema, but does mean this will only be applied to new user objects and you will have to apply this permission to all the existing user objects.
Gary.