@Mathew James Thanks for the response.
• Basically, this would be the DNS resolution when you try to access the page outside from Public Internet:

• By default, when you enable Private Endpoints to your Web App, you disable all public access.
• The access restrictions configuration of a Web App isn't evaluated for traffic through the Private Endpoint. So even if setup the “Access Restriction” with source 0.0.0.0/0 the webapp throws 403, but it evaluate the traffic even before it hits the Application hosted.
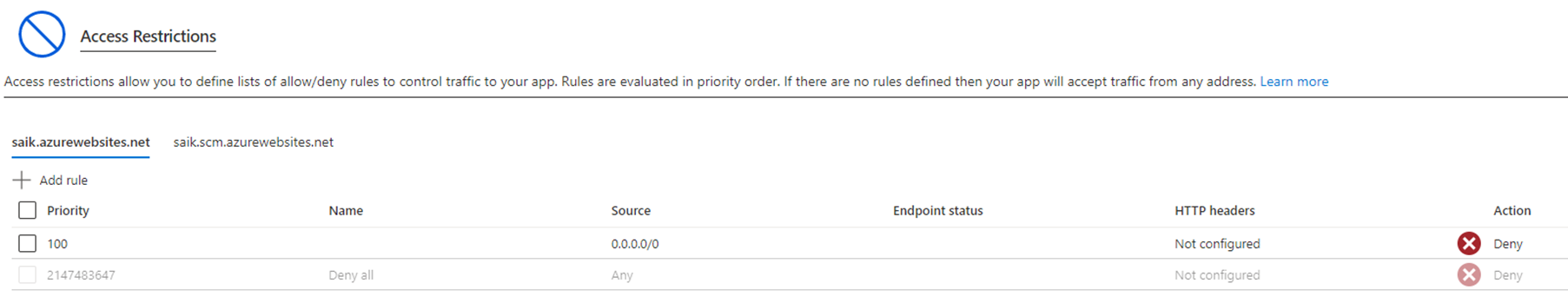
• By setting up access restrictions, you can define a priority-ordered allow/deny list that controls network access to your app.
• When a request is made to your app, the FROM address is evaluated against the rules in your access restriction list. If the FROM address is in a subnet that's configured with service endpoints to Microsoft.Web, the source subnet is compared against the virtual network rules in your access restriction list. If the address isn't allowed access based on the rules in the list, the service replies with an HTTP 403 status code.
• Considering the Public IP address for example 40.122.110.154 is Azure IP address, by default Basic Azure DDOS plan is enabled on all the Public IP’s. But its not available for Paas Services. Hence you cant use the DDOS protection for App Service IP address. https://learn.microsoft.com/en-us/azure/ddos-protection/ddos-faq#can-i-protect-my-paas-resources-using-ddos-protection-
• Or for further security concern, you could have a Frontdoor or App Gateway Infront of this App Service and have a WAF enabled.
• Please visit: Azure DDoS Protection reference architectures | Microsoft Learn.

