Hello @HelmanJames-3118 ,
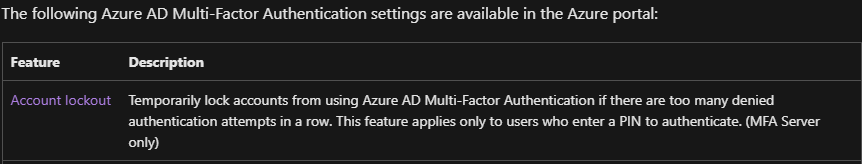
Yes, account lockout can be configured under the Azure MFA.
Go to Multifactor authentication, and account lockout settings are there.
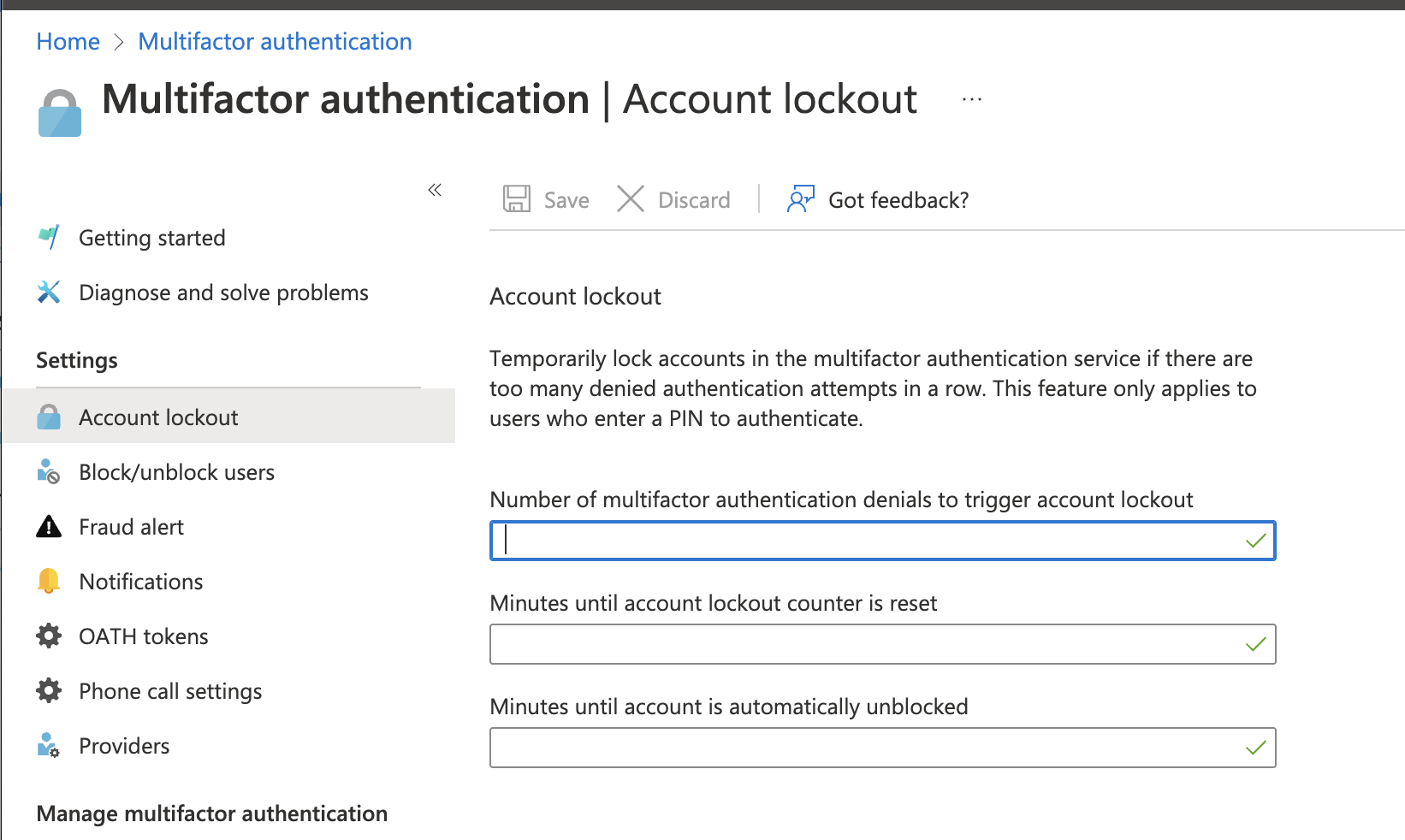
Please let me know if you need anything else. And if this helped, please click on the Select Answer button to help others who are searching for the same information.
Thank you,
Vukasin