@DavidPerry-1112
Hello David,
Thanks for reaching out to Q&A platform.
Regarding your query, if the issue is getting resolved by creating the “private zone”, I doubt you trying to access the service using Internal Access point.
Please reconfirm the configuration:
- Was the connector is Logic App ISE?
- What do you see in the access endpoint?
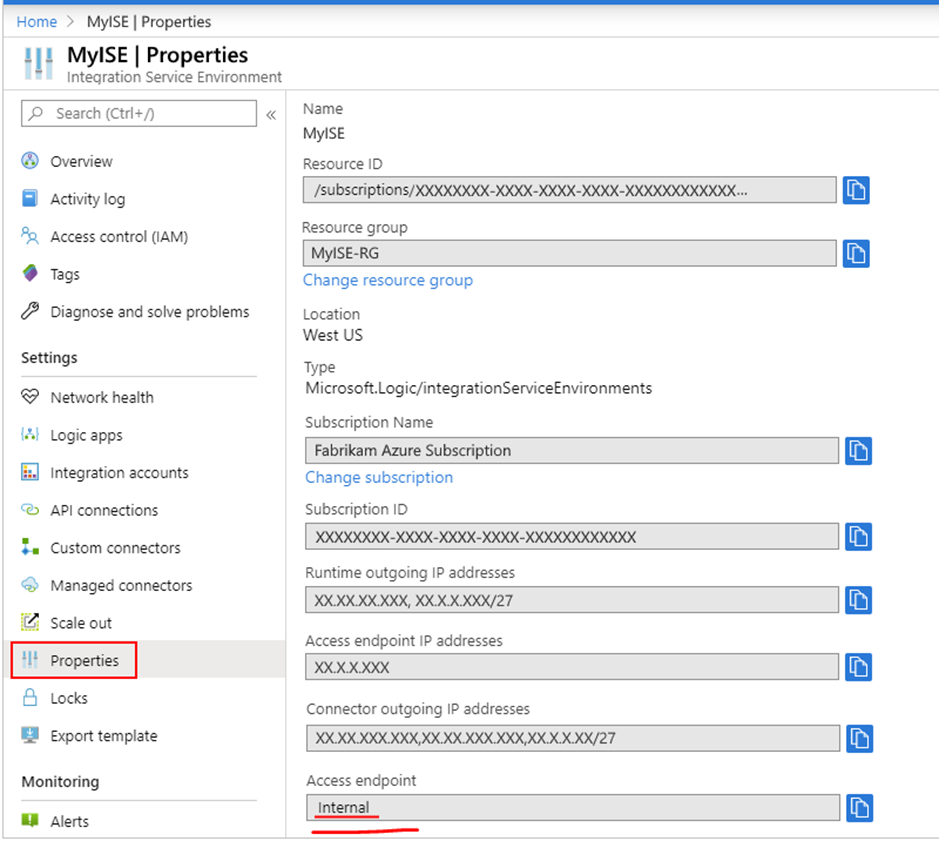
- Internal: Private endpoints permit calls to logic apps in your ISE where you can view and access inputs and outputs from logic apps' runs history only from inside your virtual network.
- External: Public endpoints permit calls to logic apps in your ISE where you can view and access inputs and outputs from logic apps' runs history from outside your virtual network. If you use network security groups (NSGs), make sure they're set up with inbound rules to allow access to the run history's inputs and outputs. For more information, see Enable access for ISE.
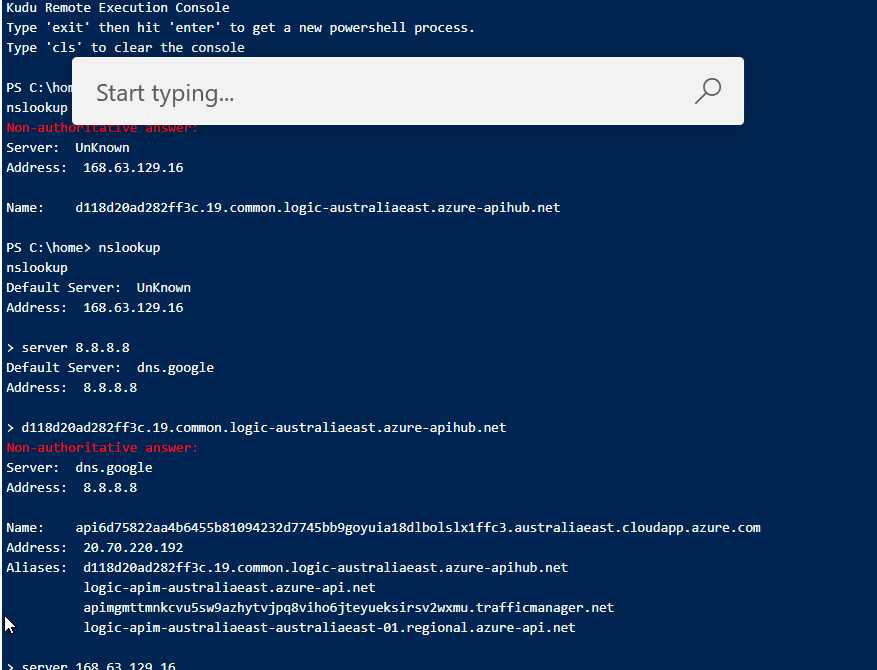
If using Private Endpoint, you need Private DNS zone to resolve the FQDN to a private IP address.
https://learn.microsoft.com/en-us/azure/logic-apps/connect-virtual-network-vnet-isolated-environment-overview#ise-endpoint-access
Regards,
Priya Kumar