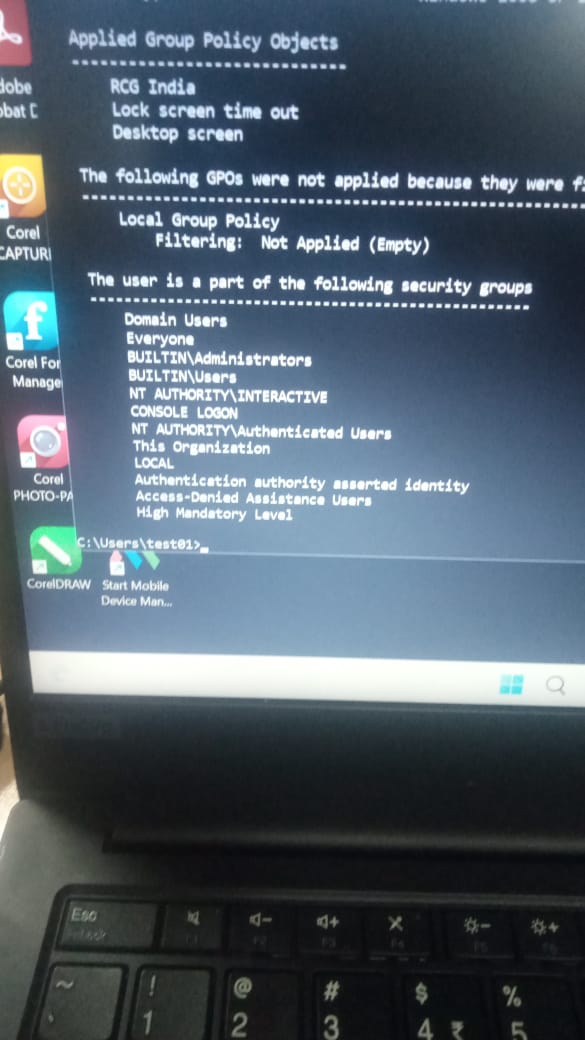
The groups displayed by the GPResult are a combination of the groups that the users is a member of and well-known SIDs added to the users access token to provide details of the users logon sessions and connection to the domain\workstation. See this link for more details on the well known SIDs https://learn.microsoft.com/en-us/windows/win32/secauthz/well-known-sids
From the screenshot, the following are well-known SIDs were added to the user's access token to identify user's session.
NT Authority\Interactive - you have logged on interactively
Console Logon - you are connected to the console session
This Organization - your user account is a member of the same domain as the workstation
Local - user account is logged onto a physical console
Authentication authority asserted identity, Access-denied assistance users, High mandatory level are details of the configuration of you windows session
NT Authority\Authenticated Users - your account has been authenticated by the domain\workstation
Everyone - all users get this SID
Only the following groups have been assigned based on AD group membership:
Domain Users - Assigned based on the primaryGroupID attribute of the user
Builtin\Administrators - Assigned probably because Domain Users is a member of the local Administrators group on the workstation.
Builtin\Users - Assigned because the Domain Users is a member of the local Users group on the workstation.
If you want to restrict the permissions the users has on the workstation, I would check if the membership of the local administrators group is controlled by group policy. You can see if there are any settings being applied by reviewing the log created by the gpresult -z
Gary.