Hello MikhailFirsov-1277,
Thank you for posting in our Q&A forum.
Here are the answers for your references:
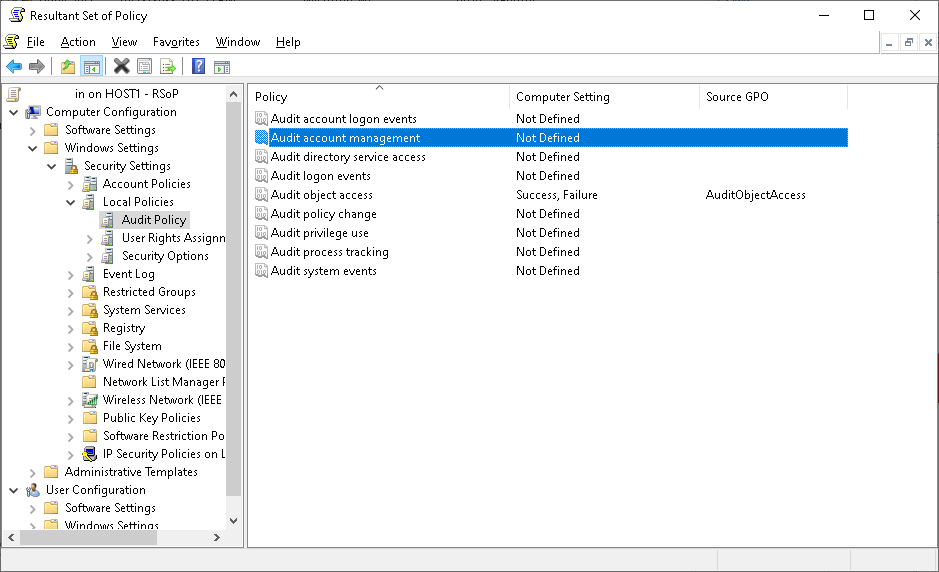
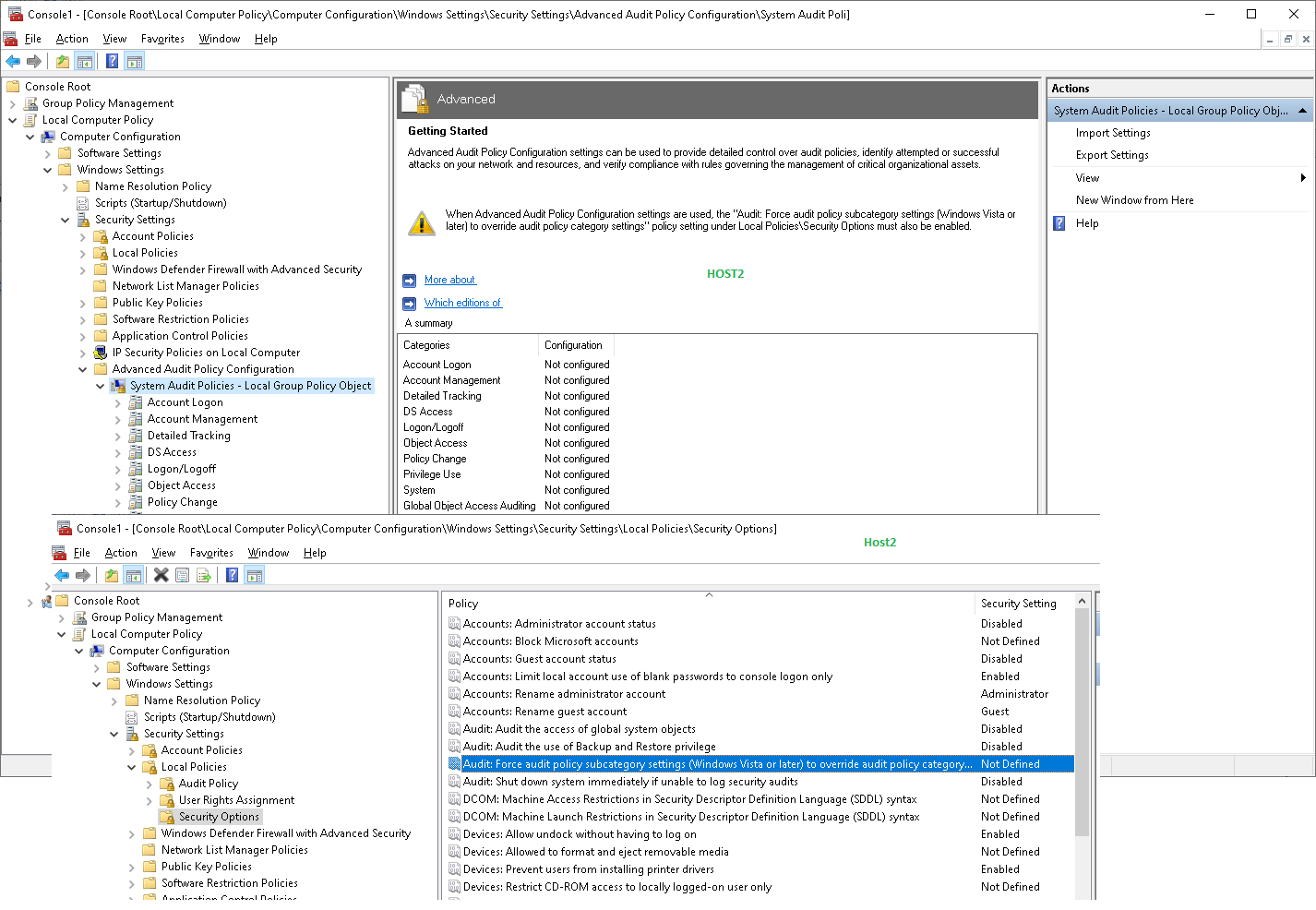
Based on the information above, I think host1 is in one domain and host2 is in one workgroup.
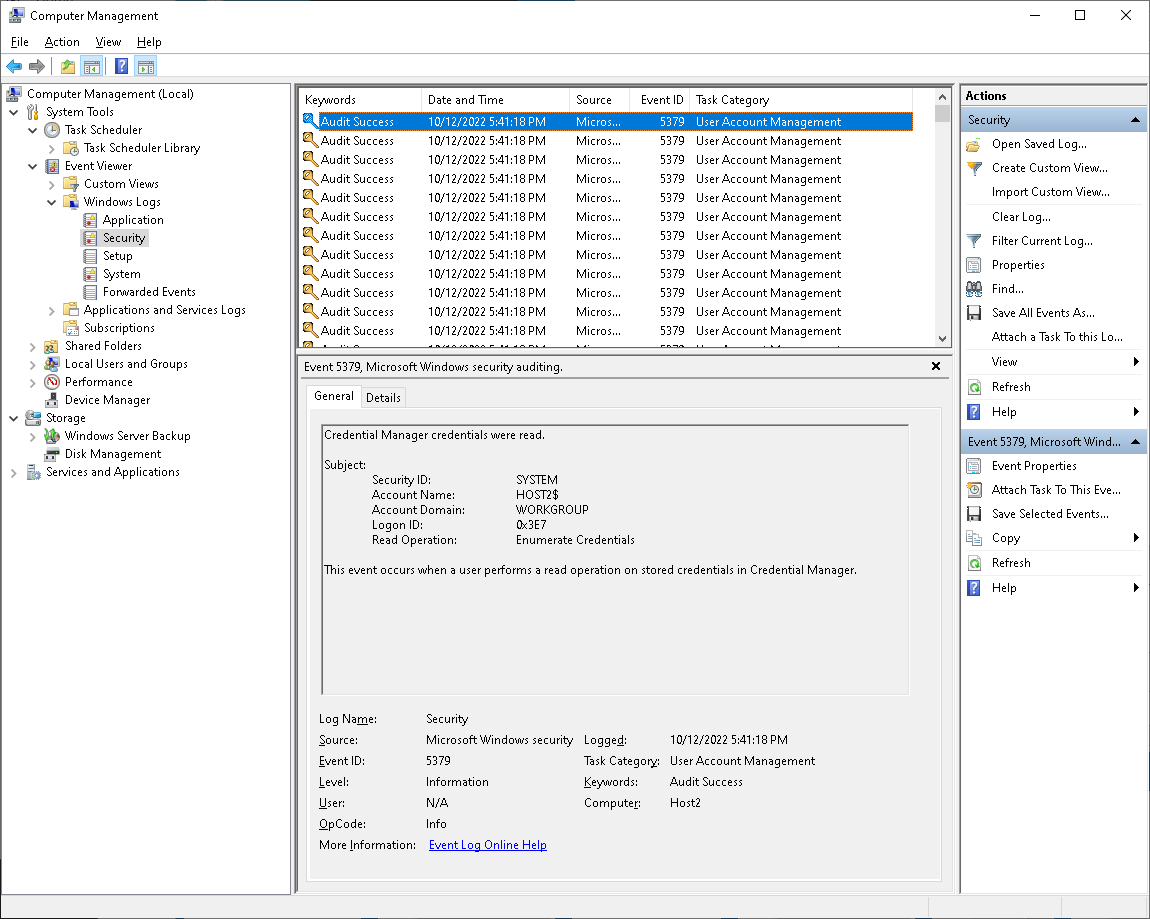
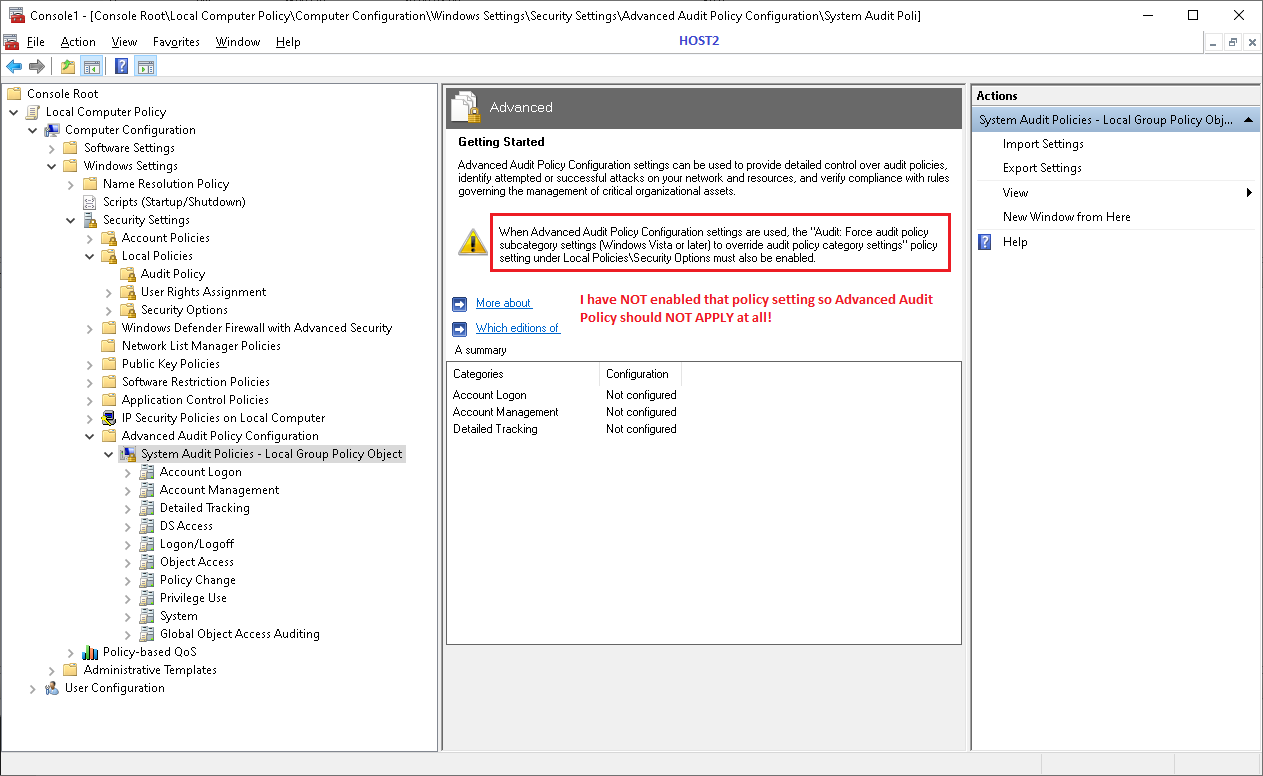
Q1: What makes these events 5379 appear in the log if there's no single audit policy enabled on Host2?
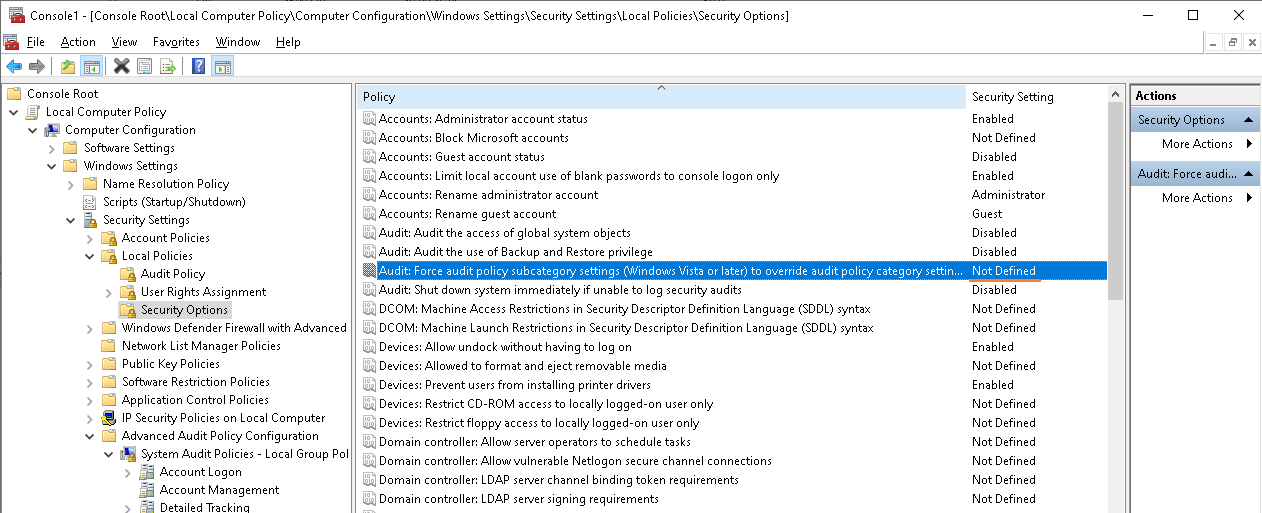
A1: You can check whether "User Account Manager category" is enabled under advanced audit policy on host2.
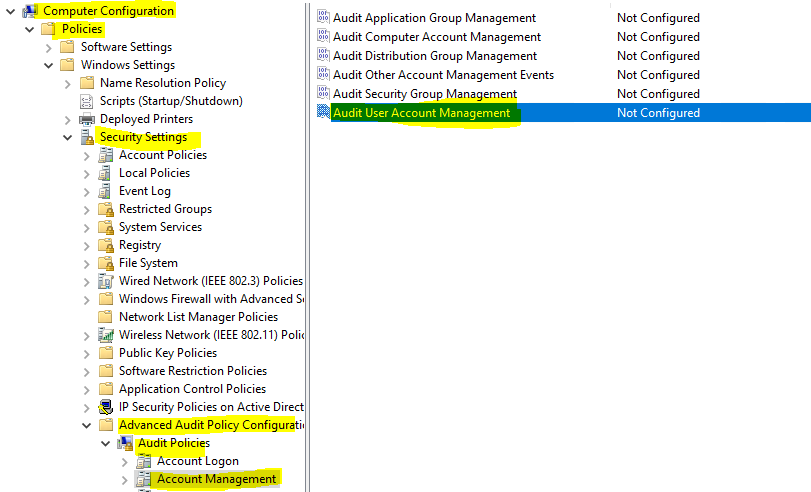
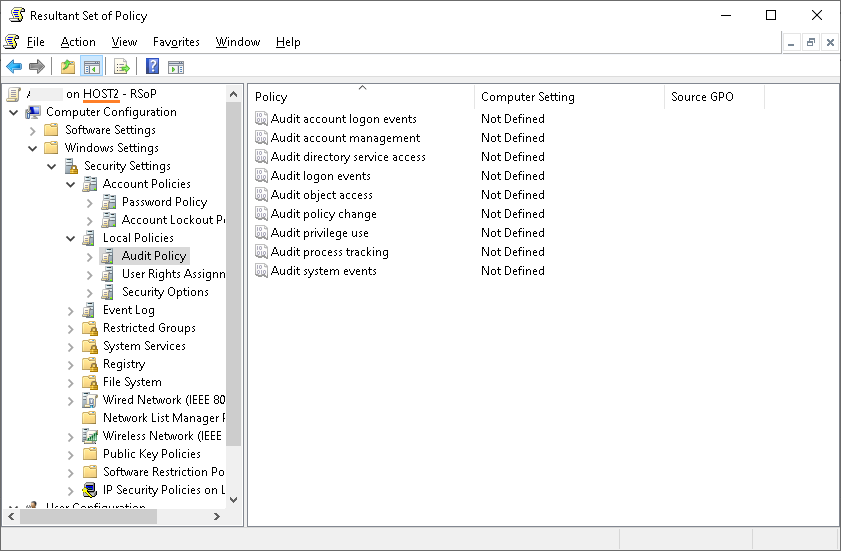
If "User Account Manager category" is not configured under advanced audit policy on host2.
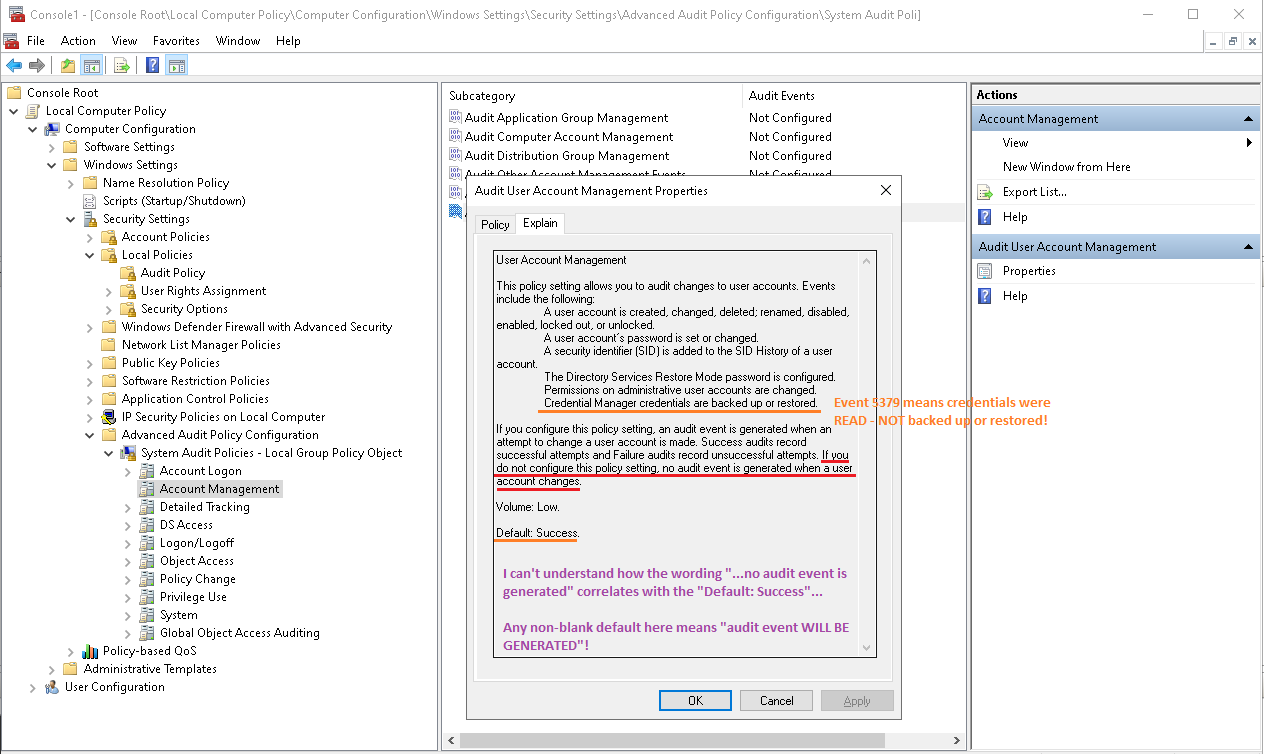
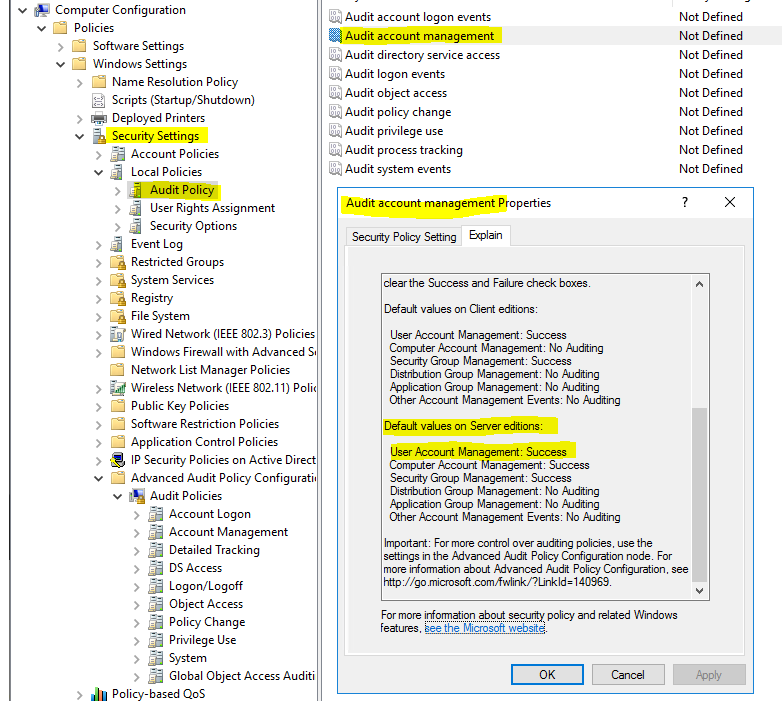
I can see the default setting is "Success" for "User Account Manager category" as below.
Q2: Why this does not happen on Host1?
A2: I think maybe there are no following changes on host1. So, it does not generate 5379 events.
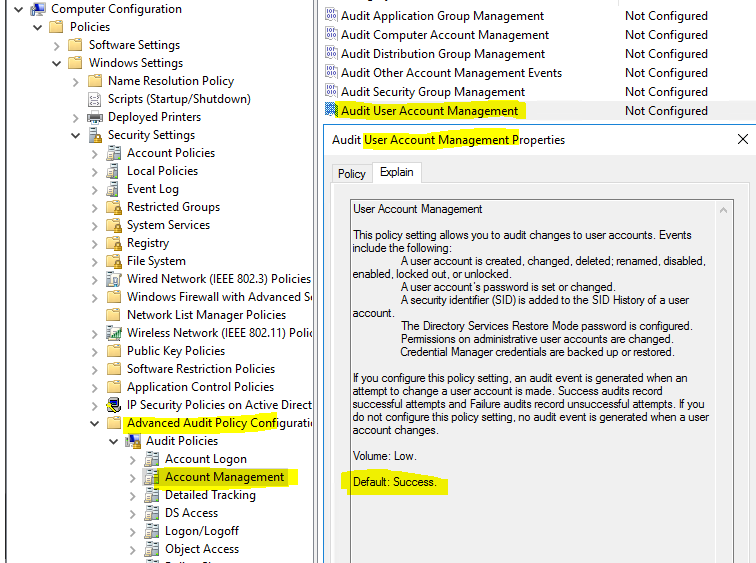
Here are the explain on the audit policy Properties.
This policy setting allows you to audit changes to user accounts. Events include the following:
A user account is created, changed, deleted; renamed, disabled, enabled, locked out, or unlocked.
A user account’s password is set or changed.
A security identifier (SID) is added to the SID History of a user account.
The Directory Services Restore Mode password is configured.
Permissions on administrative user accounts are changed.
Credential Manager credentials are backed up or restored.
Hope the information above is helpful.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.