The trusted hosts list is not relevant here because the internal domain joined users are using kerberos to connect typically so you need to disable remote powershell
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hello,
I have Exchange Server 2016 on-prem installation. I am trying to follow the mitigation steps provided for CVE-2022-41040/CVE-2022-41082 mentioned here: https://msrc-blog.microsoft.com/2022/09/29/customer-guidance-for-reported-zero-day-vulnerabilities-in-microsoft-exchange-server/
I have successfully executed the EOMTv2 script mentioned here: https://microsoft.github.io/CSS-Exchange/Security/EOMTv2/
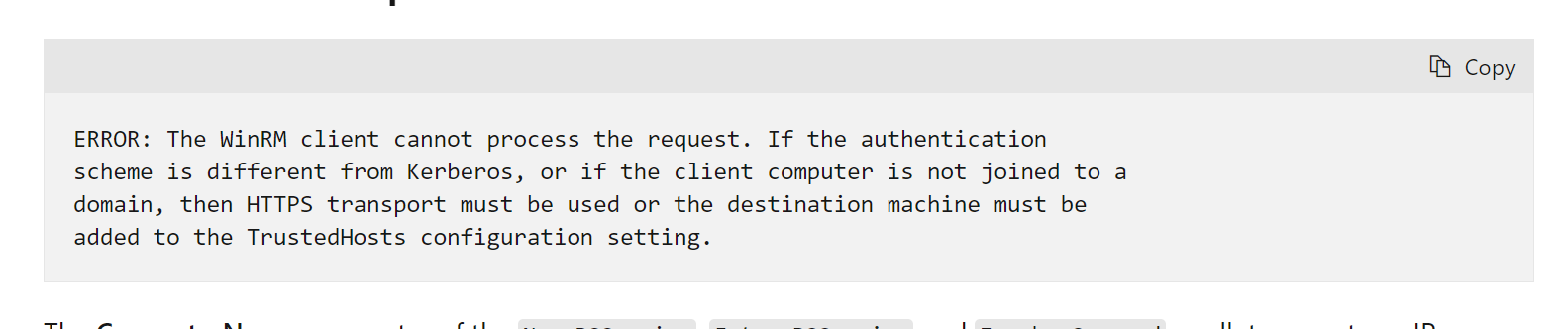
My question is about removing remote PowerShell access for users. So, exchange documentation says that every user, by default, has remote PowerShell access. However, to establish a remote session, the client host must be a part of "TrustedHosts" on the Exchange server. So, if I have not added any host to the TrustedHosts on the exchange server, do I still need to disable the remote PoweShell access for the non-admin users? Is the CVE still exploitable if a user has remote PowerShell access but does not have a TrustedHost?
Thank you.
Mo.

The trusted hosts list is not relevant here because the internal domain joined users are using kerberos to connect typically so you need to disable remote powershell
