anonymous user
In order to allow all Azure AD users in your Azure AD tenant to log into azure joined machines using RDP, you need to configure Remote Desktop settings as highlighted below:
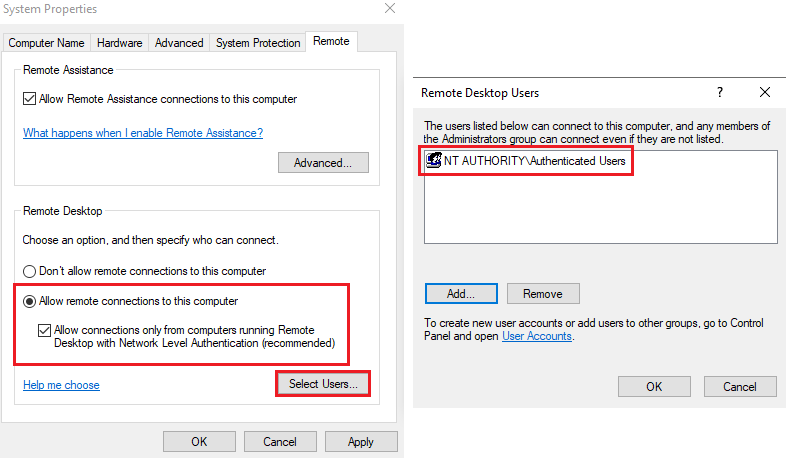
Once this is done, you can login by using AzureAD\UPN format i.e., AzureAD\username@your_tenant.onmicrosoft.com or AzureAD\username@your_verified_domain.com
-----------------------------------------------------------------------------------------------------------
Please Accept as answer wherever the information provided helps you to help others in the community.

