@Upasana Ghosh I assume that you have used Azure AD & App registration to obtain the token using OAuth 2.0 grant types. Use the following snippet to validate that app-client-id must present on the token for the validation to succeed (refer docs). This way you can validate the token was obtained from specific client(s) (or same client in your case).
<validate-jwt header-name="Authorization" failed-validation-httpcode="401" failed-validation-error-message="Unauthorized. Access token is missing or invalid.">
<openid-config url="https://login.microsoftonline.com/{aad-tenant}/v2.0/.well-known/openid-configuration" />
<required-claims>
<claim name="aud">
<value>{app-client-id}</value>
</claim>
</required-claims>
</validate-jwt>
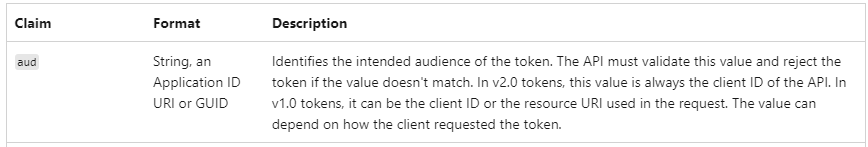
Refer Claims docs which describe about different claims in the token such as aud, oid (user or service principal), roles or groups etc.
Note: In short, application (or user) acquires a token from Azure AD and the token is sent in Authorization header to APIM and then gets validated with set of claims in APIM.
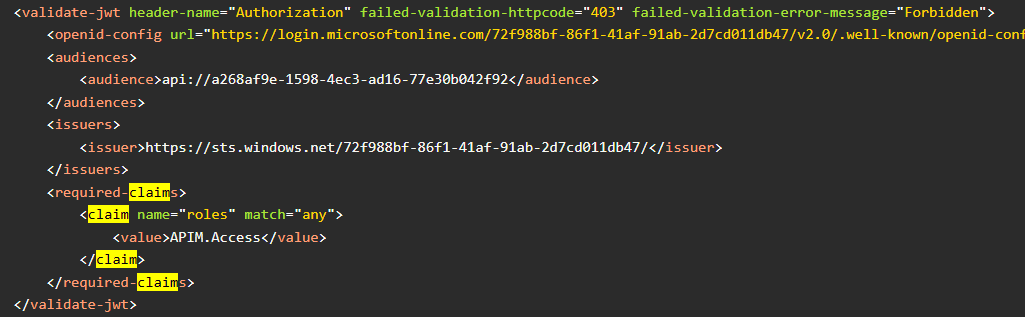
TechCommunity article describes roles with audience as APIM (hence audience was set along with required-claims).
I hope this answers your question or feel free to add a comment for any other questions. We would be happy to assist you.
