@jamh
Thank you for your post!
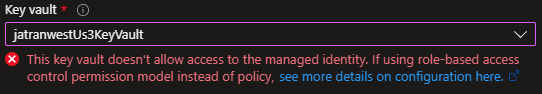
Error Message:
This key vault doesn't allow access to the managed identity. If using role-based access control permission model instead of policy.
I understand that you're having issues enabling TLS termination with Key Vault certificates and have already tried adding the appropriate Access Policies and running the PowerShell script. However, from your error message and the documentation that you're following, can you retry adding the appropriate Key Vault Access Policy or running the Key Vault Azure role-based access control permission model PowerShell script "piece-by-piece", in order to specify the Key Vault certificate via the RBAC permission model.
----------------------
Access Policy:
If your Key Vault is using Access Policies, you can add your Managed Identity by going to your Key Vault:
- Confirm your
Vault's Access Configuration - Select
Access Policies -
Add Access Policies -
Configure the Policy from a Template(Optional). The only permission you'll need isGETunder Secret Permissions -
Add&Save.

------------------------
Azure Key Vault RBAC:
If you're using the RBAC permission model specifying Azure Key Vault certificates is not supported via the portal. When I ran this script, I was able to run it line by line and didn't have any issues selecting my certificate afterwards.
# Get the Application Gateway we want to modify
$appgw = Get-AzApplicationGateway -Name MyApplicationGateway -ResourceGroupName MyResourceGroup
# Specify the resource id to the user assigned managed identity - This can be found by going to the properties of the managed identity
Set-AzApplicationGatewayIdentity -ApplicationGateway $appgw -UserAssignedIdentityId "/subscriptions/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/resourceGroups/MyResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/MyManagedIdentity"
# Get the secret ID from Key Vault
$secret = Get-AzKeyVaultSecret -VaultName "MyKeyVault" -Name "CertificateName"
# Remove the secret version so AppGW will use the latest version in future syncs
$secretId = $secret.Id.Replace($secret.Version, "")
# Specify the secret ID from Key Vault
Add-AzApplicationGatewaySslCertificate -KeyVaultSecretId $secretId -ApplicationGateway $appgw -Name $secret.Name
# Commit the changes to the Application Gateway
Set-AzApplicationGateway -ApplicationGateway $appgw
-------------------------------
I hope this helps!
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.
