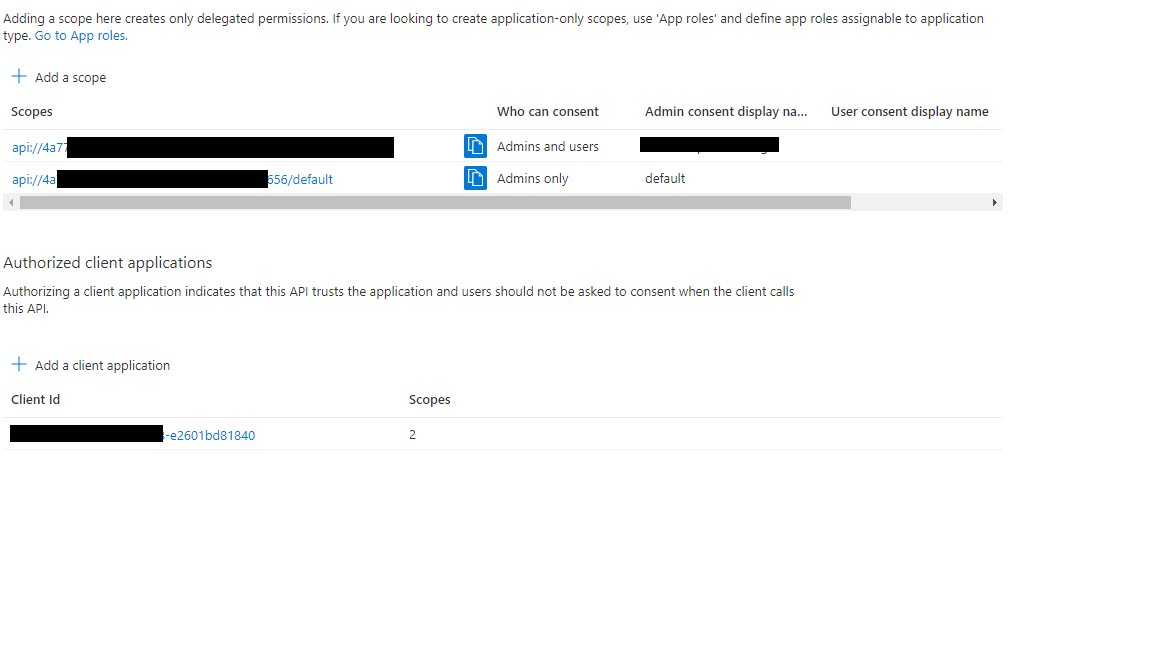
@Ano Acco Thank you for sharing the additional information/trace. The policy statements are executed sequentially and based on the code snippet above, authentication-managed-identity is first run. This policy obtains an access token from Azure Active Directory for accessing the specified resource (Func App here) and sets the new token in Authorization header.
When validate-jwt policy is executed, it checks Authorization header's new value and hence it is getting failed. So, you can move authentication-managed-identity statement after validate-jwt policy and validate (set correct claim xxxx-480e-b6bf-xxxxxx). Also, as mentioned in other docs, make sure to set "accessTokenAcceptedVersion": 2 on the client app side (App registration).
<validate-jwt header-name="Authorization" failed-validation-httpcode="401" failed-validation-error-message="Unauthorized. Access token is missing or invalid.">
<openid-config url="https://login.microsoftonline.com/contoso.onmicrosoft.com/v2.0/.well-known/openid-configuration" />
<issuers>
<issuer>https://login.microsoftonline.com/72f988bf-86f1-41af-91ab-2d7cd011db47/v2.0</issuer>
</issuers>
<required-claims>
<claim name="aud" match="all">
<value>e3ca38a3-74ab-4e09-9082-191efe69c1a9</value>
</claim>
</required-claims>
</validate-jwt>
<authentication-managed-identity resource="func-id" />
Feel free to add a comment if you have any other questions. We would be happy to assist you. Please 'Accept as answer' and ‘Upvote’ if it helped so that it can help others in the community.