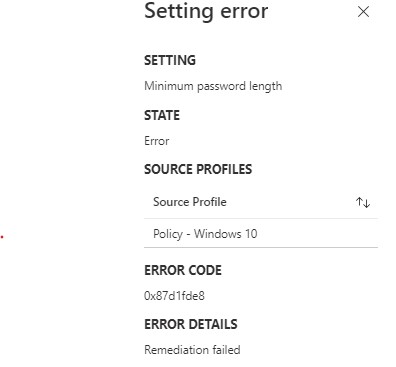
@Ritesh Sharma , Thanks for posting in our Q&A. From your description, I know you have deployed a compliance policy with a minimum password length which the password length must be 6 or above. And you set your device password, pin to more than 6 digits. But some devices get error in compliance policy. If there is any misunderstanding, feel free to let us know.
To check the issue, I go to my lab, create a compliance policy to set Minimum password length with 14 for windows 10.
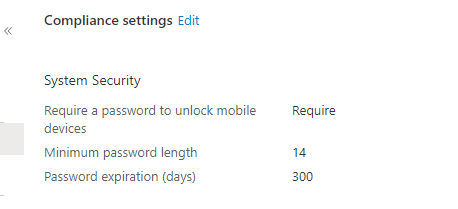
After the policy is applied, I sign in the test device with local account and AAD account. When I sign in with a local account of which password length not met, A notification is prompted to change the password. When I sign in whit an AAD account of which the password length is not met, it can still login without any affect. After researching, I find the setting is only with local account. Here is a link with more details for your reference:
https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-devicelock#devicelock-mindevicepasswordlength
For your situation, I would like to confirm if the minimum password length is set for local account. If not, please change the setting to not configured.
If yes. we can try the following steps to see if the issue can be fixed:
- Please check on the client devices if there are local user accounts, which have a value set for "User cannot change password" or "Password never expires".
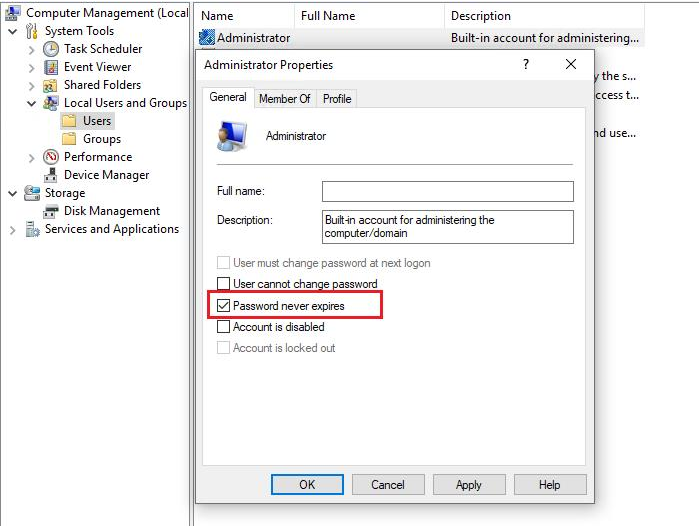
- Open the Computer Management snap-in and navigate to Local Users and Groups – Users. Please choose and double click the local user accounts and uncheck the User cannot change password and Password never expires options.
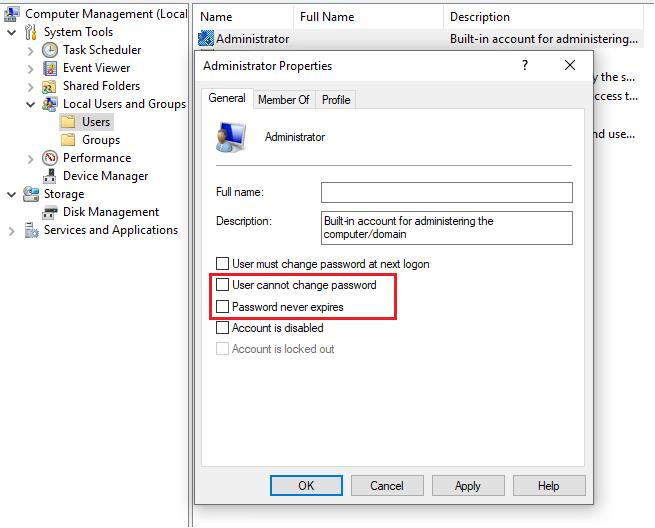
- Restart the device and manually sync the device(settings->account->access work or school->click on the account and select info->sync the device and check the compliance status on the Portal after the last check-in time has been updated)
However, if the issue still persists, you can check the event log under Applications and Services Logs > Microsoft > Windows > Device Management-Enterprise-Diagnostic-Provider to see if there’s any more finding:
https://learn.microsoft.com/en-us/windows/client-management/diagnose-mdm-failures-in-windows-10#collect-logs-directly-from-windows-10-pcs
Please check the above information and if there’s any update, feel free to let us know.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.