Hello, I am having trouble determining the best route for this, or if it is possible at this time.
I have a Windows Server 2019 Data Center VM in Azure and a local WORKGROUP lab of 2 Windows 10 PCs. Both PCs are Registered to Azure AD with AAD users assigned AAD MFA licenses. The 2019 Server VM is Azure AD joined to the same Azure tenant as the AAD users.
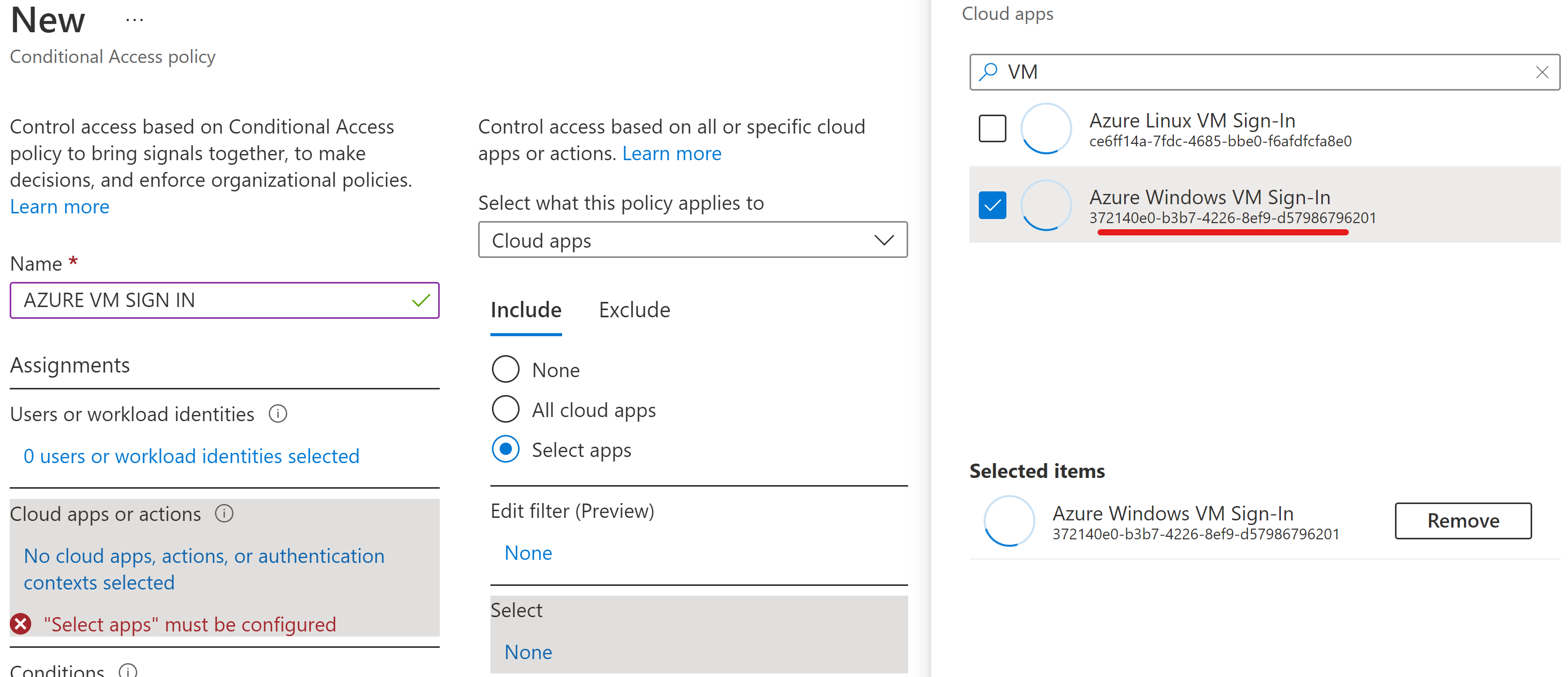
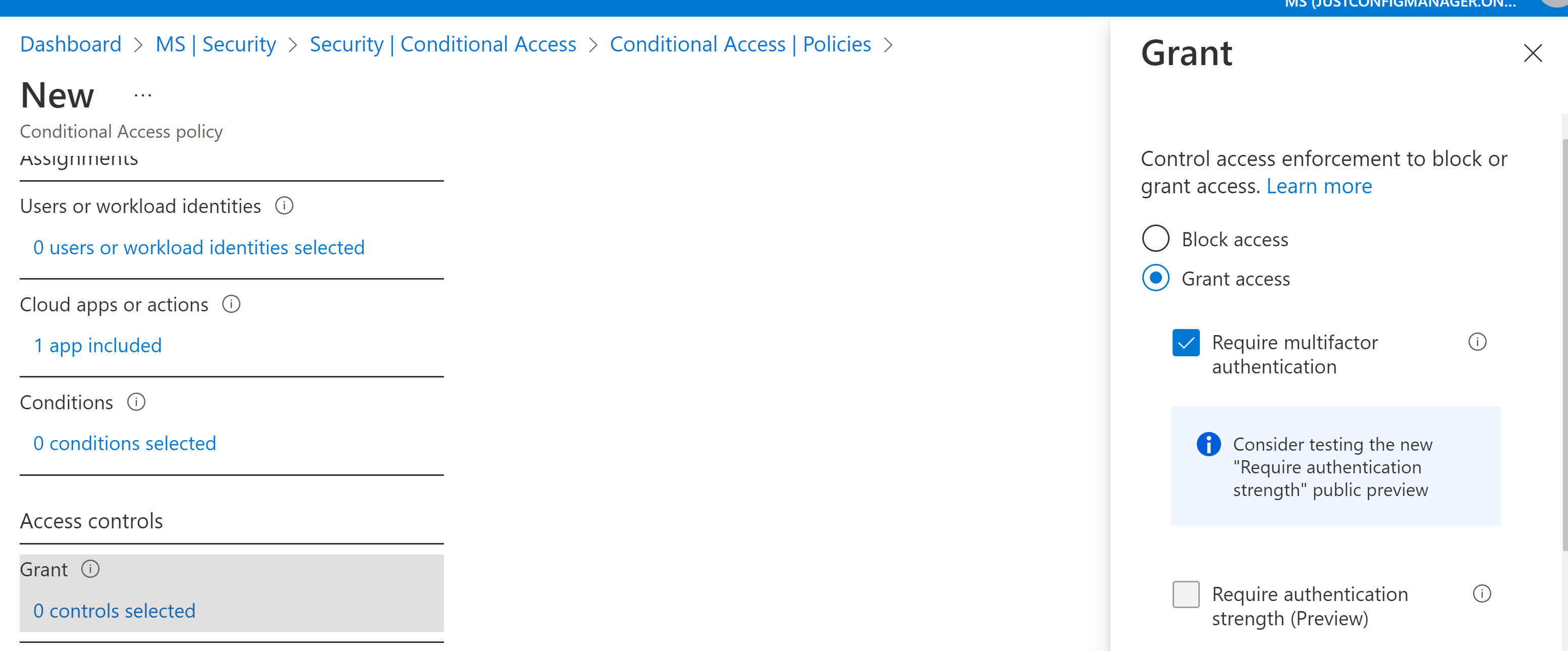
In this lab I am looking to configure the AAD Users to connect to the Windows Server 2019 VM via Remote Desktop from the PCs. The requirements would be that the AAD user utilize their AAD/Azure credentials to authenticate to the Azure server. Sign-on should also require MFA/2FA via Azure AD, MS Authenticator, PIN, or text message verification.
The basic flow would be:
User log into AAD Registered PC -> RDP Connect to 2019 Server -> Enter AAD User credential -> Complete MFA/2FA -> Log onto Server
Additional info:
PCs are workgroup machines - no Active Directory (besides AAD Registration)
No local account's will be allowed RDP login on the server - only granted AAD users via IAM membership.
Is this possible with today with Microsoft's offerings? If so, is there a clear path for deploying this? I'm happy to keep on digging to figure this out, but I don't want to be reinventing the wheel if this is already a documented practice.
Thank you in advance!!!