I'm trying to automate the deployment of my Angular Azure Static Web, APIM & Function App with Github workflows and Bicep.
Questions:
- How do I automate fetching the function key from the azure function app and storing it in my instance of APIM as a query parameter for inbound processing policy as described here: openapi-apim-integrate-visual-studio? Do I use bicep? Do I use Github workflow yaml script? How about an example?
- How to use azure key vault? I would prefer to store the function key in a key vault instead of APIM as I have queried here in a comment: how-to-use-visual-studio-to-deploy-azure-api-manag.html... Hmm... Are these comments visible to everyone? If not, my question for that post is: How do I create an APIM inbound policy (using the portal.azure.com) to include the app function key as described here (openapi-apim-integrate-visual-studio) except store the key in the key vault instead of APIM so that APIM will safely fetch it from the key vault.
And, of course, the subject of this post would be how to do this (fetch the function key from the key vault so that APIM can use it) with Bicep/Github workflow instead of the portal.
I've been recording the elapse time to fetch a key from the key vault and have learned that this takes 10-14 seconds! Wow! So instead of having APIM fetch key from the key vault every time the function app is invoked, we would definitely want to fetch it only once from the key vault during the deployment with bicep.
I have posted a related question here: how-to-automate-fetching-ocp-apim-subscription-key.html.
Thu Nov 10, 2022 Update
Before I try that HTTP PUT (with curl? what is your favorite command line tool to execute that PUT?) I need to grant my APIM access to the key vault and eventually this needs to be in bicep. However, before we tackle the problem using bicep, I'd like to do it in the portal first.
Please help me follow these instructions: api-management-howto-properties using access policies to grant my APIM access to the key vault. Actually, I'd prefer using role-based-access-control (RBAC) but I cannot get that to work either. As per the guidance from various Microsoft sources, including Scott Hunter on DotNet Conf, we should be using RBAC... But let me try access policies first because we have explicit instructions.
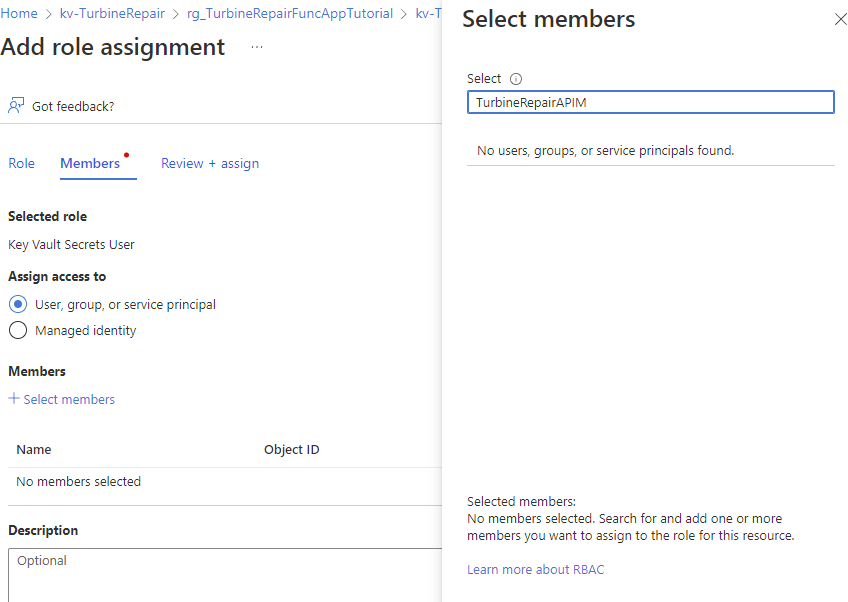
In Select principal, select the resource name of your managed identity. If you're using a system-assigned identity, the principal is the name of your API Management instance.
I cannot get this step to work in the portal. Here is my attempt:
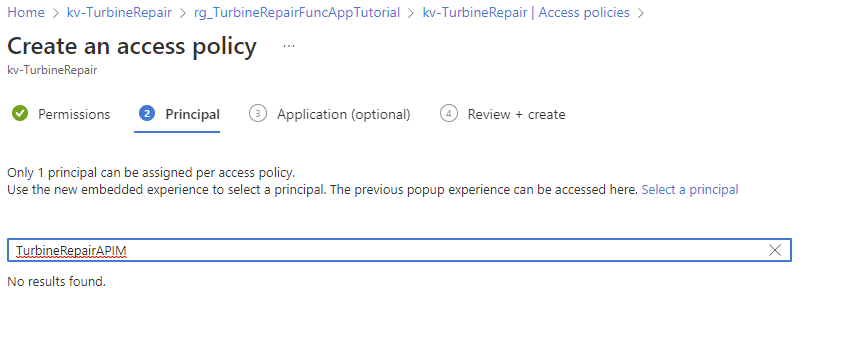
I'm using a system assigned principal and it is not accepting it.. I have the same problem with using the preferred RBAC approach:
So I think I'm experiencing the same problem with access policies and RBAC. So there is no point in trying out that HTTP PUT command until I get this figured out.
Thanks!
Fri Nov 11 2022 Update:
I don't think this is going to fit in a comment reply!
I did
az account get-access-token | ConvertFrom-Json
echo $token.accesstoken
and insert this token in my curl command
curl -X PUT https://management.azure.com/subscriptions/${AZURE_SUBSCRIPTION}/resourceGroups/rg_TurbineRepairFuncAppTutorial/providers/Microsoft.ApiManagement/service/TurbineRepairAPIM/namedValues/TRFFK?api-version=2021-08-01 -H "accept: application/json" -H "Authorization: Bearer really-big-bearer-token" -H "Content-Type: application/json" -d
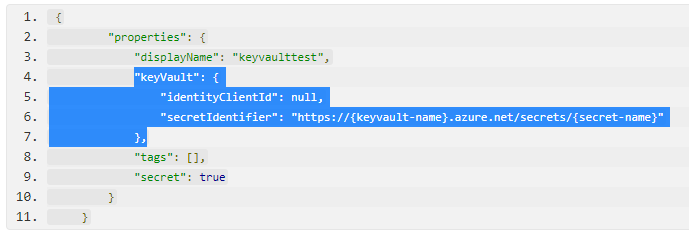
" {
\"properties\": {
\"displayName\": \"TurbineRepairFunctionFunctionKey\",
\"keyVault\": {
\"identityClientId\": null,
\"secretIdentifier\": \"https://key-vault-name.azure.net/secrets/TurbineRepairFunctionFunctionKey/<required-secret-version-goes-here>\"
},
\"tags\": [],
\"secret\": true
}
}"
I also had to use the portal and go to my key vault to display the secret details and noticed that I need to supply secret version number as part of the secret identifier.
Now when I execute this curl command, I don't get an error message! But since I already had a named value in the APIM I tried to delete the named value to confirm that the curl command was working and I could not delete it (I got this error message when I tried):
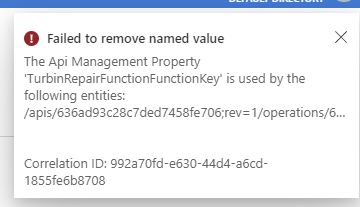
So how do I delete this old named value I created with the portal?
Well, OK, let's run that curl command again with a new named-value called TRFFK002 and see if it appears in the portal... Shucks! No luck. No error message. No new named pair in the portal... (just the old one I created in the portal but cannot delete).
(1) What am I doing wrong when I run that "curl -X PUT" command above? I know from previous attempts that if I get anything wrong in the body describing the key vault, key vault secret or key vault URL... I get an error. So I think my key vault references are correct. And if I misspell the APIM name or the resource group name, I get an error so we know those are correct. So why don't I see my new named value in the portal (after having refreshed the web page, of course!) when I run the above curl command?
(2) Please tell me about the version number of this secret that is required... What are the perils of hard coding this in my deployment script? If I don't hard code it, how do enhance my script to fetch this value?
(3) How do I delete that old named value I created in the portal?