@Daniel Niccoli Thanks for reaching out. If you have decided to build from scratch, you will have to perform the things in following order.
Please do remember that turning this off would make users status as In-Cloud means they can no longer use the ADFS for authentication, and would have to depend on password sync as backup. Once you have setup the AAD connect on separate server and processed a full sync after 72 hours, the users would join back to original set and then you can perform ADFS auth again.
1) Make sure you have password sync enabled for all users. as when you turn off the sync, all users will be using the synced password to login and not ADFS.
If not, follow these steps.
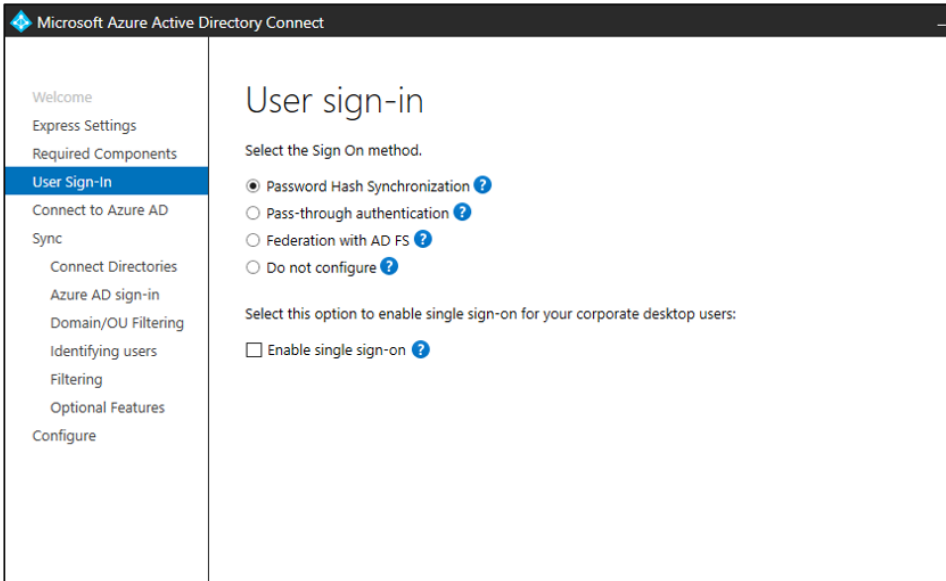
2) Once done, You will have to make sure to convert the Federated domain to managed then by using : Convert-MsolDomainToStandard commandlet
https://learn.microsoft.com/en-us/powershell/module/msonline/convert-msoldomaintostandard?view=azureadps-1.0
3) Turn of Dirsync (use powershell as mentioned in the link or use the office 365 portal to deactivate Sync ):
4) Setup the AAD connect on new server and then uninstall the previous one.
5) Turn on Dirsync after 72 hours
6) Federated the Domain to start using ADFS again using : https://learn.microsoft.com/en-us/powershell/module/msonline/convert-msoldomaintofederated?view=azureadps-1.0
Please note that there are many factors to consider, all of which cannot be written as answer here, but this is just a high level steps you would need to take. If you have decided to go this route and I would also suggest to open a support ticket with Microsoft when you do this as I have seen many scenarios where something might go wrong and these are prod users we are talking about which will generate more helpdesk calls if something goes unplanned.
If the suggested response helped you resolve your issue, please do not forget to accept the response as Answer and "Up-Vote" for the answer that helped you for benefit of the community.