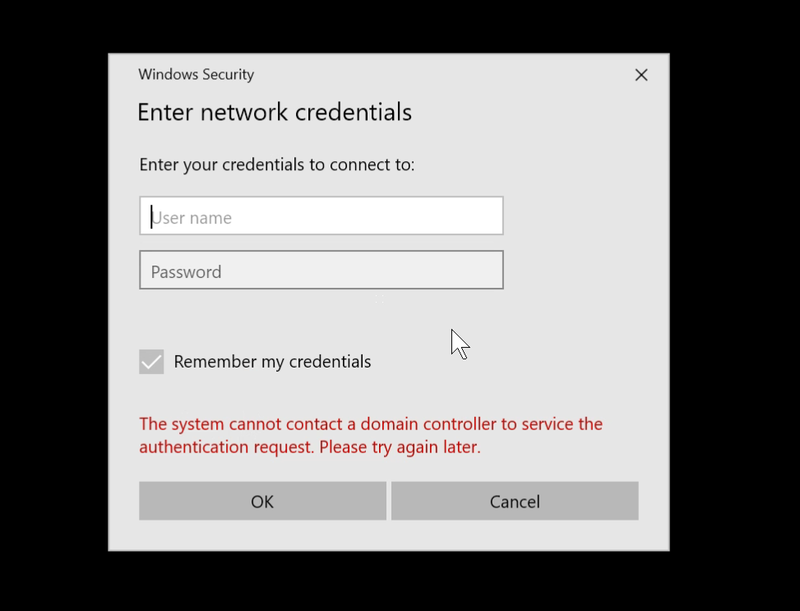
if your client machines are AADJ (cloud joined). They trust your domain name present by the KDC certificate
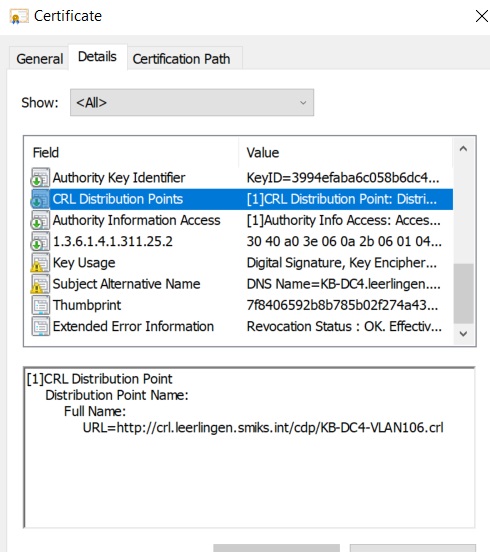
your KDC certificate should contain subject with "Distinguishname" -where it can extract "DC=contoso, Dc=Com" i.e if your domain is contoso.com
Else if you have CA template 2012R2 and above , default Subject alternative names populate domain name in it.
i.e dns name =DC1.contoso.com , DNS name =contoso.com
we already listed this in our known issue (I was the one updated the doc :)) . This would often happen if they used third party CAs too.