Hi MSTechie,
We would need to know a bit more information on what type of MFA deployment you have - Is it Per-User MFA or Conditional Access MFA ?
If you have PerUser MFA - Make sure the account authenticating does not have the policy Enforced requiring MFA at every sign-in.
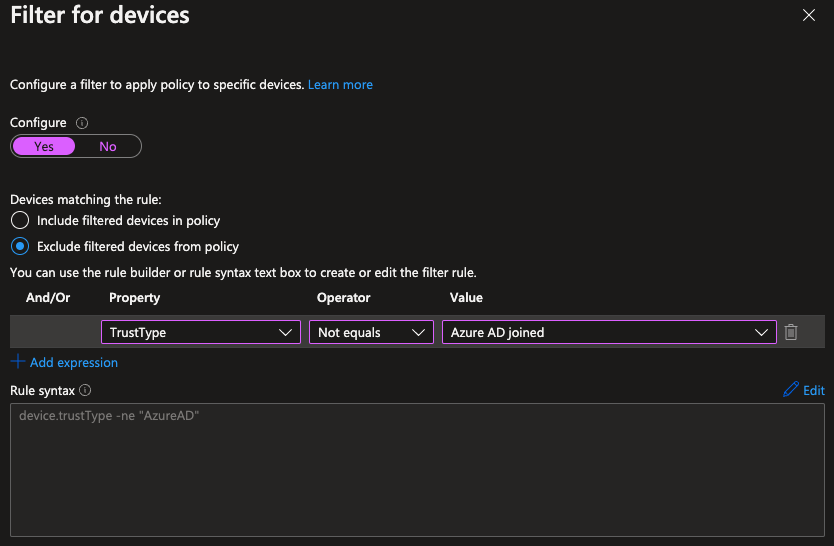
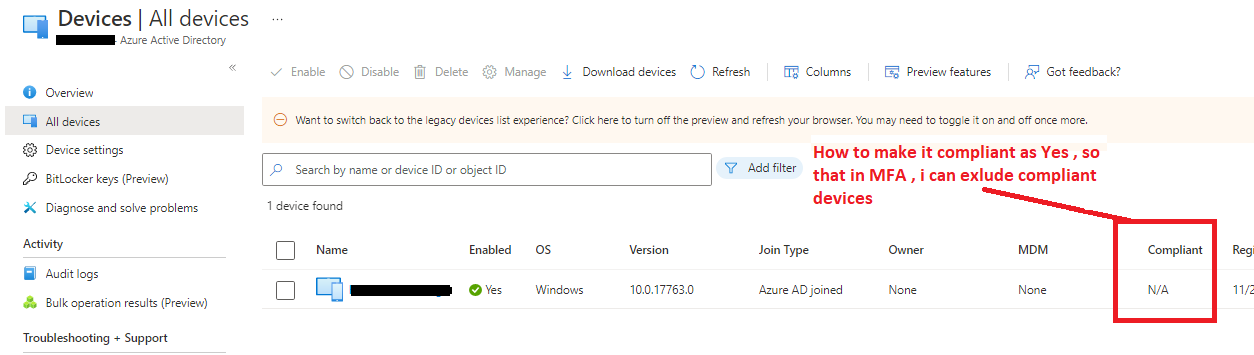
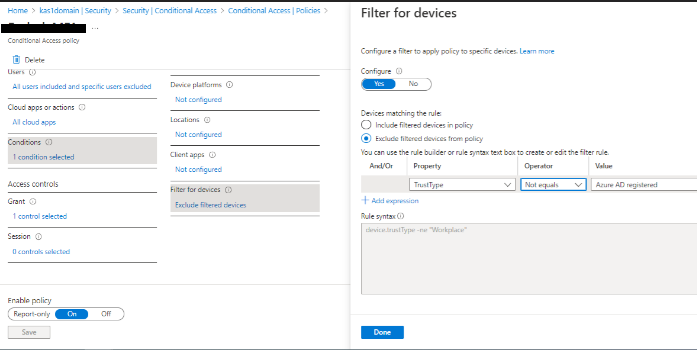
If it's Conditional Access MFA, inside your Conditional Access Policy that requests MFA prompt to authenticate the user you can go to conditions and use the "Filter for Devices" options to exclude devices with Trust Type - Azure AD Joined.