Thanks for your patience on this.
Wanted to share below details to clear with AKS’s authentication concepts, which is also described here.
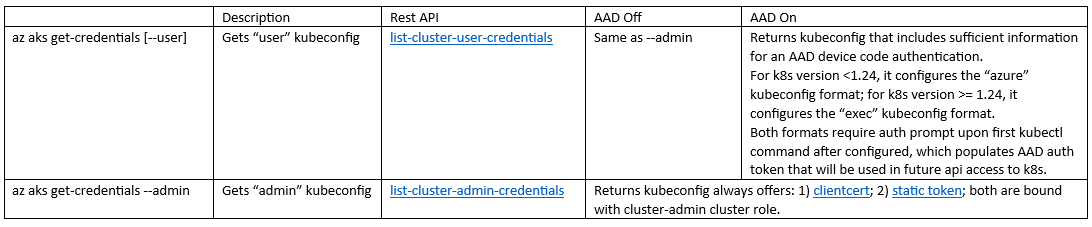
Ref:
list-cluster-user-credentials
list-cluster-admin-credentials
clientcert
static token
Below are the responses for your queries.
Is there any HTTP API that tells about Which model was used for AKS cluster authentication?
The managed-clusters/get call (az aks show) shows whether AAD based authentication is enabled.
Is there any common approach (Which works for all types of AKS clusters wither used AAD / K8s Service accounts)?
Service accounts always works. It however requires in-cluster operation to generate the service account and credentials prior to usage.
Admin token also works, note however that admin account can be blocked via disable local accounts. Admin accounts has its own problem, namely: 1) the permission is too broad for automation and can easily be abused; 2) Difficult to rotate on security breach.
I shared this in my previous response to extract both admin tokens and service account tokens.
Is /oauth2/token API call access token can be used as a bearer token for K8s resources API calls?
To which identity provider? If the provider is AAD, then yes. See the deprecated azure auth code in go-client (used in kubectl) that “Authorization: Bearer {token}” is used even for Azure authentication when talking with kubernetes.
Hope this helps.
If the suggested response helped you resolve your issue, please 'Accept as answer', so that it can help others in the community looking for help on similar topics.
