Hi @Wade_Adapt ,
I see that you are looking for a policy to update all the resources in subscriptions with 12 empty tagNames. Azure Policy with 'Modify' effect will be a good solution for this use case. There are 2 inbuilt policies available in Azure Portal which can be edited to meet the requirement here. These policies are Add a tag to resources and Add a tag to resource groups.
The following are high level steps to edit these inbuilt policies from portal, assign them and create remediation task. For this sample, I have used Add a tag to resource groups inbuilt policy and similar steps can be used to edit the other policy as well.
1. In Azure Portal --> Azure Policy, select Definitions
2. Search for "Add a tag to resource groups", select it and click on "Duplicate definition" as shown below:
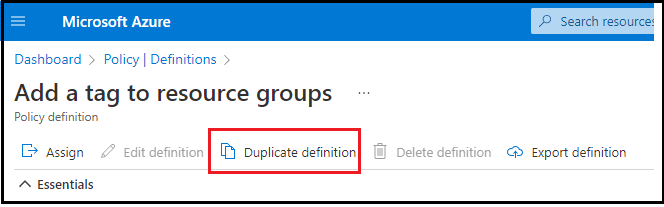
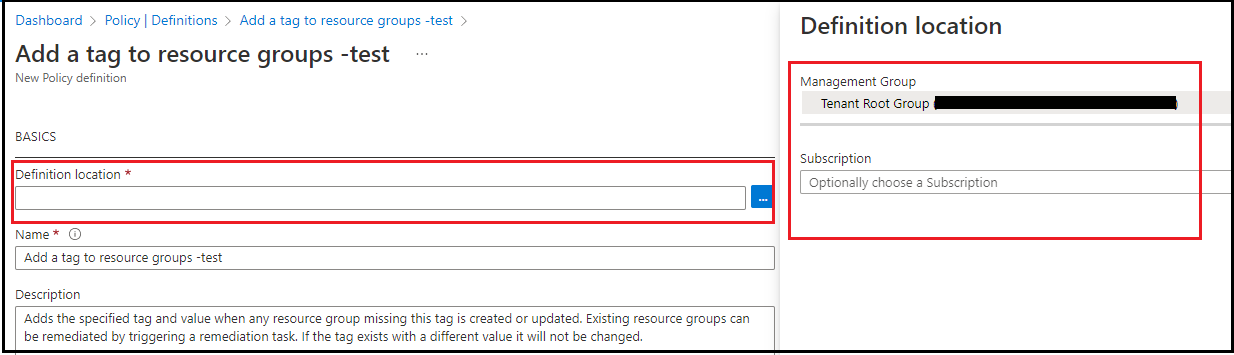
3. Select "Definition location". If you have an Azure Management Group with multiple subscriptions in it, you can select the location as "Management group". This would help you assign this policy to multiple subscriptions OR apply to all subscriptions in the Management Group. Alternatively, you can choose to save it in a particular subscription instead.
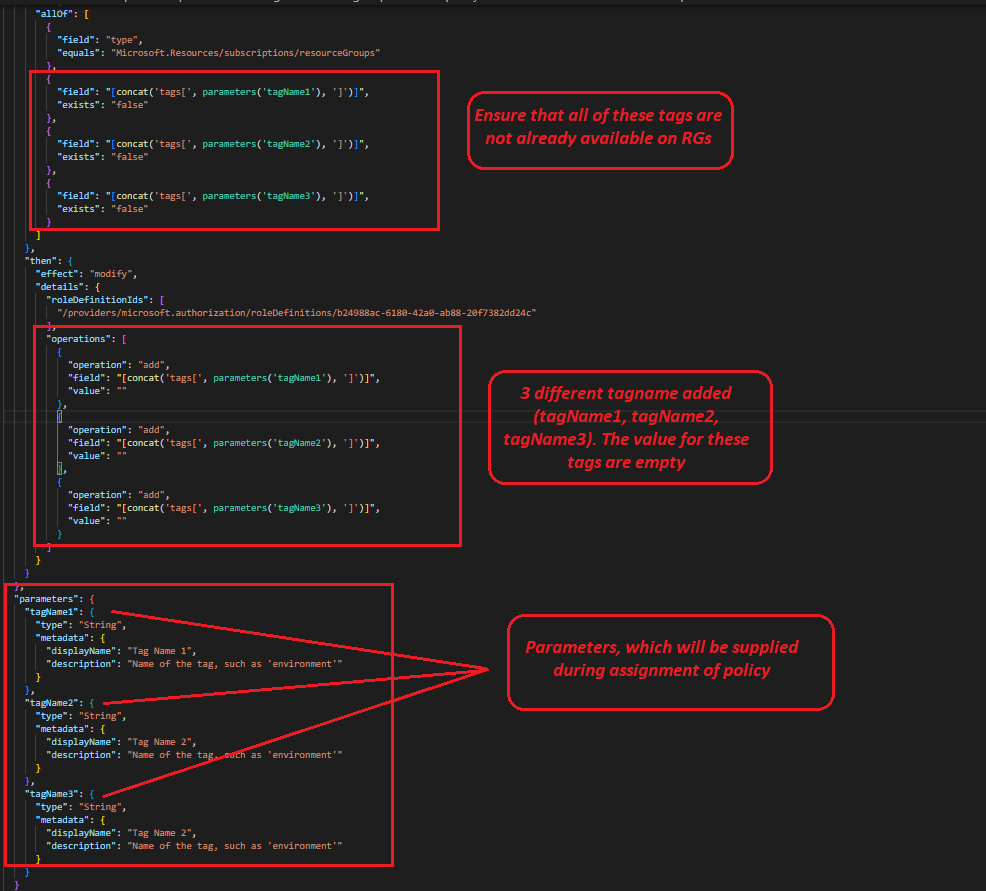
4. Update the Policy Rule. This policy is scoped to apply tagName and value to Resource group. The updated policy is attached with this reply, and the image below highlights the edited sections (In this example, I have added 3 tags with empty value. You can scale it to 12 parameters and with required tagNames):
5. Click on Save --> Click on "Assign"
6. Select Scope, which could be the Management Group or a subscription that you choose, click Next
7. Provide tagNames. Note that tagValue is not asked here, as it is required to be empty.
8. On "Remediation", select "Create a remediation task". This is to add tags on existing resources based on this policy. By default, the policy only adds tags to new/updated Resource groups and shwos the existing ones as non-compliant. Remediation helps to modify existing non-compliant resources based on a policy. You can see this link for details on remediation in Azure Policy. If you do not see the option to select "Create a remediation task", you might have selected the scope of assignment as "Management Group". In this case, you will have to create remediation task later, once the policy is assigned. Please see this link for details.
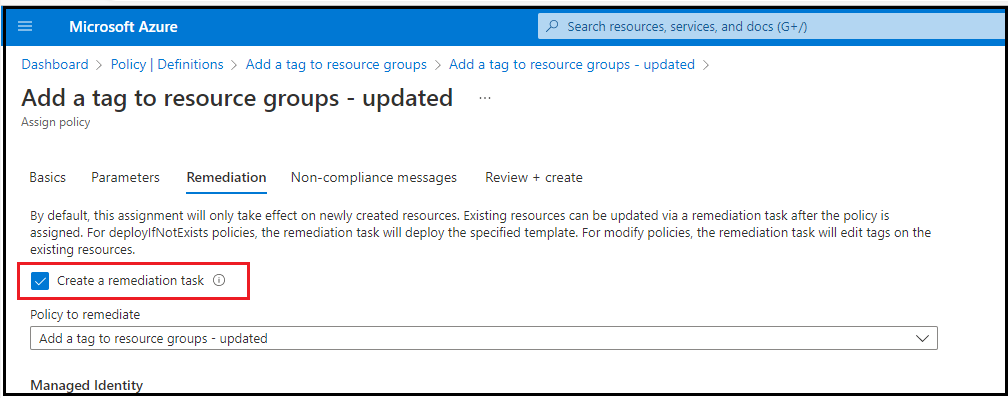
9. Next --> Next --> Create
In about 30 minutes, the assignment takes into effect and remediation task, if created, would apply tags to all the Resource Groups.
The steps above can also be replicated to duplicate and edit Azure Policy Add a tag to resources, to add tags on all resources.
Please let me know if you have any questions.
---
Please 'Accept as answer' and ‘Upvote’ if it helped so that it can help others in the community looking for help on similar topics.
