James,
Thanks for all your help on this. I appreciate it a lot.
So, I'm trying to run either the API solution through an Azure DevOps pipeline or as a powershell script from the pipeline since the pipeline will login, authenticate and run this as the appropriate user with permissions. I've run into the following issues:
- The API fails (404) to find the Role Definition ID path which is in a variable like so:
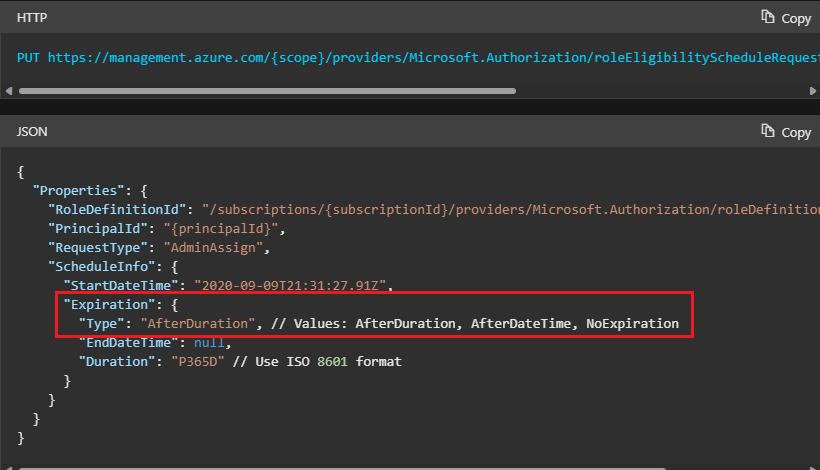
$pimRoleDefinitionId = "/subscriptions/<my_new_subscription>/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635" # the GUID is from the built-in Owner role
- The latest option - Update-AzRoleManagementPolicy - fails in the pipeline with either AzurePowerShell@5 (the latest I can use is 5.209.0 I believe) and I see the docs are written for AzurePowerShell@8 and 9. I say that because I get this error: "Unable to find type [RoleManagementPolicyExpirationRule]." RoleManagementPolicyExpirationRule shows up a Java class or my Powershell Version (5) doesn't recognize it. Or the pipeline wants ConnectedServiceNameARM set in the yaml file which may also require azureSubscription set (which doesn't accept the name of my new subscription) when I set AzurePowerShell@5 in the pipeline.
Is Update-AzRoleManagementPolicy meant to be an Inline script in the pipeline or can it be a script I call???
Also, I really like the option for the API call because it explicitly sets type to NoExpiration but the API won't run because of #1 above - error 404 - doesn't like something in the role definition id path which is a copy and paste from my az cli:
az role definition list --scope /subscriptions/<my_new_subscription_id> --name Owner
[
{
"assignableScopes": [
"/"
],
"description": "Grants full access to manage all resources, including the ability to assign roles in Azure RBAC.",
"id": "/subscriptions/<my_new_subscription_id>/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635",
....
API Call in PS:
Invoke-WebRequest -Method 'PUT' -Uri https://management.azure.com/subscriptions/$subscriptionId/providers/Microsoft.Authorization/roleEligibilityScheduleRequests/$roleEligibilityScheduleRequestName`?api-version=$apiVersion -Headers $headers -Body $roleEligibilityScheduleRequestBody | ConvertTo-Json -Depth 100
Do you have any working API code anywhere that does anything close to this? Should I be using Microsoft Graph? https://learn.microsoft.com/en-us/graph/api/rbacapplication-post-roleeligibilityschedulerequests?view=graph-rest-1.0&tabs=powershell