Describe the Issue
Reason for this task, is so I can request for an Access Token on behalf of a non-person user account, completed upfront. This is so, I can use it, for accessing Sharepoint via Graph API and in my python script just use that in the header as a bearer token and access the Sharepoint files, lists etc., Then refresh token when it expires, for this I assumed using offline_access as Scope would yield longer token expiry duration, that way, I don't have to refresh token as often. But that doesn't seems to be the case...
Steps Taken:
In postman add a new request
Go to Authorization tab, set up the following:
Configuration Options:
Token Name: my-token-name
Grant Type: Authorization Code
Callback URL: http://localhost:8888
Auth URL: https;//login.microsoftonline.com/my-tenant-id/oauth2/v2.0/authorize
Access Token URL: https;//login.microsoftonline.com/my-tenant-id/oauth2/v2.0/token
Client ID: my-client-id
Client Secret: my-client-secret
Scope: sites.manage.all offline_access
State: 12345
Client Authentication: Send as Basic Auth header
Then click on 'Get New Access Token' button
When I get a pop to choose which email account I want to use and then further prompts to enter the uid/pwd as credentials. Then it proceeds to authenticate and Grants Consent and asks to Proceed.
All looks good
3. Then clicking on Proceed button behind the scenes Postman issues a Post request to the access token url and the response pops up.
4. On checking in the Postman console, I see two requests one GET and another POST
In the GET request I do see the request body scope as what I set in the Configuration Options in Step 2.
GET https://login.microsoftonline.com/......./oauth2/v2.0/authorize?response_type=code&client_id=......&state=12345&scope=sites.manage.all%20offline_access&redirect_uri=http%3A%2F%2Flocalhost%3A8888
but when I check the POST request I do not see the Scope being passed to it in the Request body nor as a query string parameter either.
POST Request Body
grant_type: "authorization_code"
code: "..."
redirect_uri: "http://localhost:8888"
client_id: "...."
FYI: client_id, code masked above
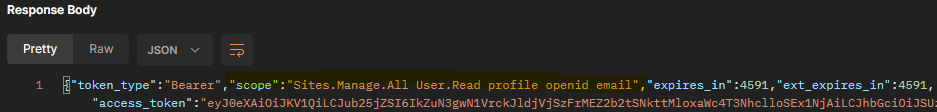
And so the expiry is not long enough, its about 4000-5000+ seconds. Reason for using offline_access in Scope, was because the documentation says that it gives longer period of expiration duration, and avoid having to refresh the token every so often in a day.
Screen shot of POST response is attached below...
Any help, is appreciated.
TIA