You could follow along here.
https://learn.microsoft.com/en-us/azure/cost-management-billing/manage/add-change-subscription-administrator
--please don't forget to upvote and Accept as answer if the reply is helpful--
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I work for a CSP, added a new customer to our marketplace, customer has an existing M365 account, the customer contact is the global admin for his company. He created a new Azure subscription, under that subscription he can see his Identity as global admin, but he has read only access, so he cannot create resources in Azure. How does he change his Azure identity to give him full amdin rights like what he has for his M365 subscription?
You could follow along here.
https://learn.microsoft.com/en-us/azure/cost-management-billing/manage/add-change-subscription-administrator
--please don't forget to upvote and Accept as answer if the reply is helpful--

@Vincent Van Gent
Thank you for your post!
I understand that you work for a CSP and added a new customer (Global Admin) to your marketplace. This new customer then created a new Azure Subscription but only has read access (I'm assuming through the Azure AD Elevate access feature) and can't create any resources within that Subscription.
Because Azure AD and Azure resources are secured independently from one another - Azure AD role assignments do not grant access to Azure resources, and Azure role assignments do not grant access to Azure AD, the customer will need to assign their user the appropriate RBAC role for the new subscription in order to create resources within Azure.
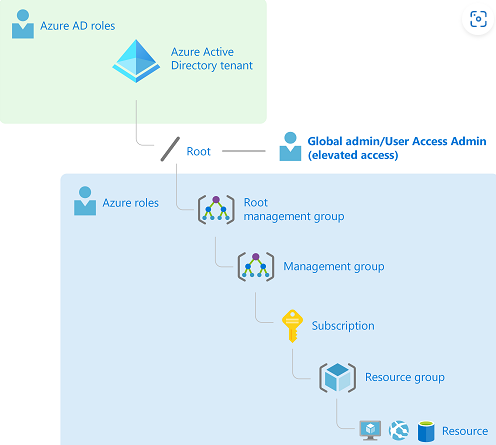
Assign Azure roles using the Azure portal:
Subscriptions, or a specific Resource group within the subscription) Access Control (IAM) page. Add role assignment. 
I hope this helps!
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.