Hi Everyone,
I had a issue on my environment after install cumulative update November 2022 on my Domain Controllers.
Clients running any version of Windows had a issue when try access network share or any resource use Kerberos when the server is Windows 2003
Example share:
On the client with this error, open cmd and run:
Klist
KRBTGT you will have a Ticket with encryption and Session key with AES-256-CTS-HMAC-SHA1-96
The SPN of the Windows Server 2003 will have a Ticket with encryption RSADSI RC4-HMAC(NT) and session key AES-256-CTS-HMAC-SHA1-96
Because the session key AES-256-CTS-HMAC-SHA1-96 this authentication fails
Windows Server 2003 doesn’t support this encrypt protocol on Kerberos
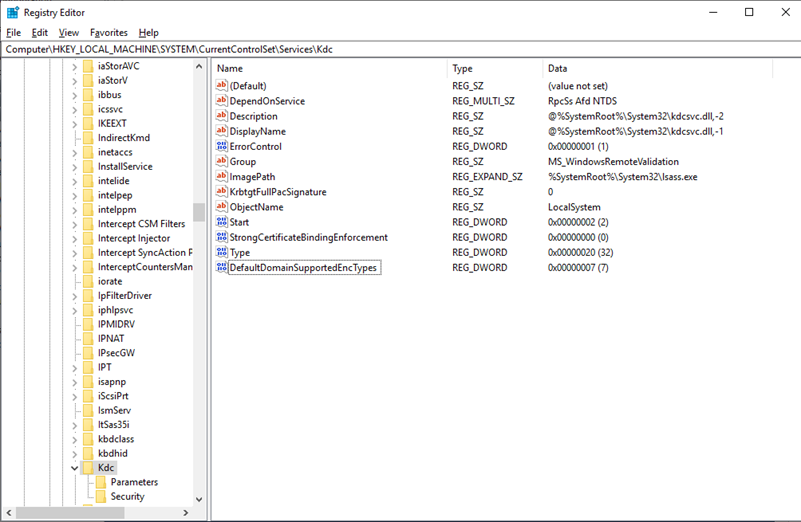
To mitigate this issue you can create Dword32 DefaultDomainSupportedEncTypes on the path HKLM:\SYSTEM\CurrentControlSet\Services\Kdc with value 0x7
The Default value after install KB 11-2022 is 0x27.
The explanation of value:
6cfc7b50-11ed-4b4d-846d-6f08f0812919
Convert to binary, check the bits will be enable and convert to Hexadecimal to set Dword DefaultDomainSupportedEncTypes.
In the simple way, 0x27 enable to force the Session key to be AES-256-CTS-HMAC-SHA1-96 when legacy encrypt protocol like RC4-HMAC(NT) is requested.
Reboot on DC is not required, but run the command klist purge (doesn’t execute as administrator, it need be run on the user session) on the client, or logoff and logon.
After change, the ticket and session key will be encrypted with RSADSI RC4-HMAC(NT) and the authentication will work normally.
If you have this issue with another unsupported operational System and doesn’t work after this change, try to add attribute msDS-SupportedEncryptionTypes with value 7 or 4 to computer object.
You can use the powershell command:
Set-ADComputer NameSERVERWithUnsupportedSO -Add @{'msDS-SupportedEncryptionTypes'=4}
Or
Set-ADComputer NameSERVERWithUnsupportedSO -Add @{'msDS-SupportedEncryptionTypes'=7}
I had this issue only with Windows server 2003 on my envionment, and I could not test this last solution.
More Details on:
3696351
Regard
Gilberto Lima



