
Hi,
Have a look at this article which can be used to confirm that the policy is being applied correctly.
https://nettools.net/how-to-display-which-fine-grain-password-policy-is-applied/
Gary.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hi Guys,
I am applying FGPP for a domain user with a less restrictive settings than the Default Domain Policy...
RunspaceId : 4de3d0c4-0065-4db3-b8d9-18358169e995
ComplexityEnabled : True
DistinguishedName : DC=internal,DC=xxxx,DC=xx,DC=xx
LockoutDuration : 00:30:00
LockoutObservationWindow : 00:30:00
LockoutThreshold : 7
MaxPasswordAge : 60.00:00:00
MinPasswordAge : 1.00:00:00
MinPasswordLength : 8
objectClass : {domainDNS}
objectGuid : 8d55a069-0d8a-457d-8f5d-1ef515fdb41b
PasswordHistoryCount : 24
ReversibleEncryptionEnabled : False
Upper settings are from Default Domain Policy.
And the PSO I applied for min 6 char complexity disabled...
When I try set a new password for that user which I applied the PSO directly to the user I still get the password complexity warning...
Also, Just for a test, I changed the PSO settings to MAX lockout threshold to 3 and account end it up locking but still cannot set 6 char password without complexity...
Whats going on here any idea guys??
Regards,,


Hi,
Have a look at this article which can be used to confirm that the policy is being applied correctly.
https://nettools.net/how-to-display-which-fine-grain-password-policy-is-applied/
Gary.
Policy applying but not totally because you can confirm this by powershelll command with this:
Get-ADUserResultantPasswordPolicy
And Also you can check the AD User Attribute in AD which is two of them:
msDS-PSOApplied
msDS-ResultantPSO
They both showing my PSO object is applying but not able to pass complex password setting defined on Default Domain Policy...
Even though FGP should override Default Domain Policy....
AD Version is Server 2016..
Hello GokhanCil,
Thank you for posting in our Q&A forum.
Please check the password policy for this user that with FGPP.
Open Powershell and run the command below.
Get-ADUserResultantPasswordPolicy useraccount
For example:
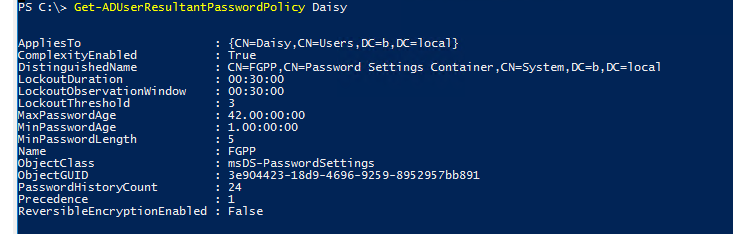
Also, please ensure AD replication is working fine.
Hope the information above is helpful.
Best Regards,
Daisy Zhou
===============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
PS C:\Users\admin_xxx> Get-ADUserResultantPasswordPolicy bne_kiosk
RunspaceId : 3b289949-5e71-4d6a-8056-300035d90300
AppliesTo : {CN=BNE_KIOSK,OU=Shared Login Kiosk,OU=Shared
Accounts,OU=_STAFF,DC=internal,DC=com,DC=au}
ComplexityEnabled : False
DistinguishedName : CN=PIN-CODE,CN=Password Settings
Container,CN=System,DC=internal,DC=com,DC=au
LockoutDuration : 00:30:00
LockoutObservationWindow : 00:30:00
LockoutThreshold : 0
MaxPasswordAge : 00:00:00
MinPasswordAge : 00:00:00
MinPasswordLength : 6
Name : PIN-CODE
ObjectClass : msDS-PasswordSettings
ObjectGUID : 1320a3ed-1b0d-4a7e-b4fe-79320dc4276b
PasswordHistoryCount : 1
Precedence : 2
ReversibleEncryptionEnabled : False
I wonder does it have anything to do with the DA account since I am using my delegated account??