Hi,
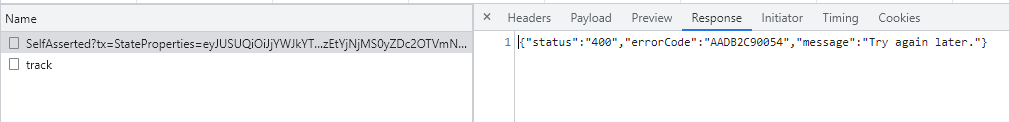
I would like to hide errorCode from SelfAsserted service response
as per security remediation report from the third party company.
Possible other error codes could be error-codes
You can reproduce this issue with showing these error codes using this demo website authorize with already created account by trying:
- to log in using non existing email account
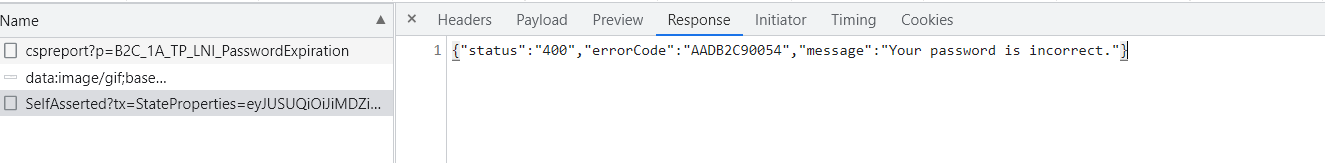
- to log in using existing email but wrong password
For these two above scenarios and many different I would like to have same message without letting the user know what is the error and what is exactly wrong.
Appreciate for any solution :)
Marek